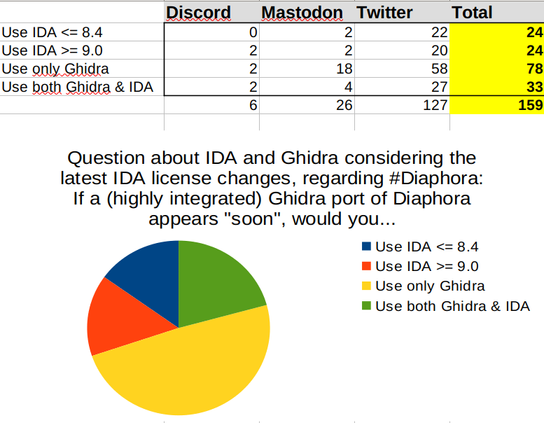
@godotengine Damn, took threat actors long enough.
I've long held a pet theory that writing malware using Godot would give a threat actor a fairly good return on investment even when comparing other engines. That said, I don't think this is Godot's fault; IMO it is still difficult to safely run untrusted games and Windows still lacks serious sandboxing capabilities that are available for all users. On Linux you can at least use something like firejail or bubblewrap or Bottles… and even those options feel somewhat lacking or dauting for the average user.
Most Godot games out there cannot be run on W10 Windows Sandbox due to requiring Vulkan or OpenGL (this is the "anti-sandbox technique" Checkpoint Research talks about, and for the average malware sandbox I'd say this applies with any game engine), although this was fixed in Godot 4.3 with the addition of DirectX support. With Windows Sandbox being IMO the most user-friendly way to run untrusted Windows application, this makes it more difficult for an end user to safely run any untrusted Godot game.
Plus, you got a fully-fledged scripting engine out of the box that cannot be introspected by AMSI on Windows (not that it does a lot on red team scenarios anyway) and the engine is open source and single-executable so it's easy to add new capabilities at the C++ level and break existing reversing tools, with everything being compiled to a huge executable that makes Ghidra sweat (and gamedevs especially pre-4.0 can often end up shipping custom versions of the engine with added extensions, so you cannot just do a similarity analysis and discard executables that deviate too much from upstream without getting some significant false positives).
While encouraging gamedevs to lean towards web exports, I've also seen a lot of indie devs out there be frustrated with them in most game engines for various reasons, and now there seems to be an gamedev culture of "please download the game if you experience performance issues", setting the end user expectative and making the issue worse.
All in all, this is more of a systemic issue; the state of cybersecurity on gaming just sucks.