I love when it happens to other companies too 🙃
I'm an entrepreneur, audio tech and IT guru. A music lover, geek, dancer, cancer survivor, aspie, and just the right amount of crazy! 🤨😆
Tech profile: most toots will be about networking, hardware and cyber-stuffs.
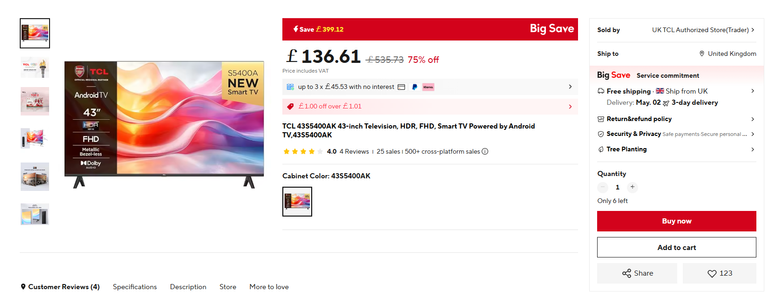
@Edent It's (reportedly) shipped locally from TCL's warehouse, so should be the same delivery time as other marketplaces. Still, I don't mind waiting at all. I don't even _need_ the TV, but at that price I'll find a use for it! 😅
43" 1080p LED LCD, HDR, 400 nits - for £136.61?! I mean... 🛒🚚
Cogent: I can sell you transit on the world's best network for the cheapest, rock bottom prices, only $0.05/Mbit.
Me: I already pay $0.04/Mbit.
Cogent: Oh! We can beat any deal. Who's that with?
Me: uh, AS174...
Cogent: *ends call*
Whoa: The European Space Agency's Solar Orbiter spacecraft got a spectacular view of Comet ATLAS (C/2024 G3) as it passed close to the Sun. Look at that enormous, splintered tail!
This comet won't be seen again for another 600,000 years.
https://www.esa.int/Science_Exploration/Space_Science/Solar_Orbiter #space #science #art
@CenturyAvocado It's the 'minging' for me! 😂
I thought that was only a geordie/northern word!
By making minor changes to command-line arguments, it is possible to bypass EDR/AV detections.
My research, comprising ~70 Windows executables, found that all of them were vulnerable to this, to varying degrees.
Here’s what I found and why it matters 👉 https://wietze.github.io/blog/bypassing-detections-with-command-line-obfuscation
Imagine taking your phone into the repair shop thinking that you've cracked the screen, only to be shown it's the pre-applied screen protector and have it peeled off before your eyes, in a crowded store.
Yes, I work with technology for a living. 😂🙈
Huh. Not bad!
https://www.servethehome.com/this-is-the-asus-ascent-gx10-a-nvidia-gb10-mini-pc-with-128gb-of-memory-and-200gbe/
This thing is screaming to be a cheap, high-perf router. At $3k for 2x 200GbE? Throw on some Deb/Ubu, FRR, VPP and you're winning.
Oh. If anyone's ever fantasized about unaliving me, now's your chance. The gas board's dug up a 10ft+ deep hole right outside my office door and we have no fire escape. Drop a match and it's game over. Peace. 🙃
My son has a friend over, and he saw a USB thumb drive laying on my desk and asked me if it had Linux on it
Rather surprised, I told him yes (because installing Linux is the only thing I use thumb drives for) and asked why he assumed that.
He rather sheepishly told me he has a collection of thumb drives containing Linux that he uses to boot to and bypass controls on school and other computers he has to use
The kids are all right
$185 to connect our KVMoIP to a server. One fucking hundred and eighty fucking five dollars. 🤯😠
The bridge bassline in MiC LOWRY's Oh Lord matches the resonant frequency of my desk and it's making everything shimmy under my fingertips. 😅
And now a random RouterOS TTL bug crops up 🙃
Whoops, I nulled HKG but it's back now 🙃
rr05 coming online
+10G transit coming online
+216 CPU, 1.72TB RAM, 108TB SSD coming online
🔨🔧🪛👲
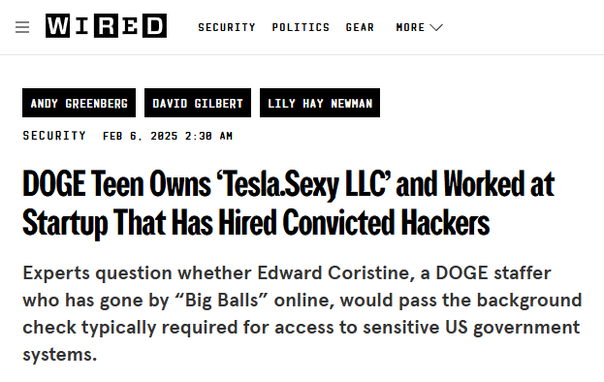
Oh man, I have so many stories about the "startup" (Path Network), which the 19-year-old DOGE employee, Edward Coristine previously worked for.
https://www.wired.com/story/edward-coristine-tesla-sexy-path-networks-doge/
My first interaction with the founder, Marshal Webb, was in 2016 when the company was called "BackConnect'. I'd recently posted a research paper on the Mirai botnet, which lead to him harassing me online, simply because he considered himself to be the sole authority on Mirai.
It later turned out, that a lot of his knowledge came from the fact that he was personally hosting the threat actors' infrastructure, therefore had direct insight into the botnet. He tried to play it off as an "intelligence gathering operation". Everyone knew he was really just in bed with the threat actors, but nobody could prove it enough to make a case against him.
At some point shortly after, a DDoS-for-hire service got hacked and its entire customer database along with all DDoS attack logs was leaked online. One of the records traced back to an employee of his DDoS mitigation firm, and from a combination of attack logs and corroboration with customers, it was determined that they had been launching DDoS attacks against businesses, then cold calling them to sell DDoS protection services.
It was fairly apparent from the fact the emails coincided with the DDoS attacks, but did not originate from the the employee performing the attacks that the company was in on it, and this wasn't the work of some rogue employee. Nevertheless, said employee got thrown under the bus, convicted, and was unsuccessful in proving that his employer was in on the conspiracy, although they most certainly were.
Eventually, the founder ended up being named in some kind of criminal complaint or other FBI related court document. The specific wording seemed to imply that he'd gotten caught doing something illegal enough that he'd become an informant to save himself. Amusingly, when the document surfaced, the company just issued a press release about how they were "helping the FBI stop crime" and nothing become of it.
The company has always been shady as hell, and while it's not abnormal for cybersecurity firms to hire reformed hackers, I've not seen a single employee who was not directly involved in cybercrime immediately prior to getting hired. Furthermore, multiple of the employees have been caught committing cybercrime while working for the company.
Originally, when I posted this thread on February 6th, I stopped short of any allegation that Edward himself was involved in cybercrime. Since then @briankrebs was able to trace his aliases back to a known cybercrime organization and confirm he indeed was directly involved in cybercrime as recently as May 2024.
You can find Brian's Mastodon thread on the matter here:
https://infosec.exchange/@briankrebs/113965646509637016
https://infosec.exchange/@briankrebs/113957683483583881
Lol. It's a nightmare trying to troubleshoot this script flow. 😆
Great start to the morning! 😳🙈