https://s1.ai/readup
🐚 Adware loaders are always the most complex! Props to @syrion89.bsky.social for helping me pull apart all these different bins and figuring out what they had in common and how to attribute and detect them. 🦾 #adware #malware #macOS #security
@sentinelone.com @sentinellabs.bsky.social
macOS security researcher, technical writer, editor, #lufc fan. Opinions my own. I do not speak for my employer, or they for me. 😎
macOS FlexibleFerret | Further Variants of DPRK Malware Family Unearthed #macOS #malware #DPRK #apt
https://s1.ai/Ferret
If you're interested in leveraging AI and open source tools (radare2) to reverse engineering (mobile) apps, check out this excellent article by @pancake from @NowSecure . Abstract and repo/blog links ⬇️
➡️ Abstract: This post covers a novel approach for recovering application source code, leveraging AI language models to transform pseudo-disassembly into high-level source code. This method is able to handle complex abstractions introduced in high-level languages SwiftUI or Dart and generates output in popular programming languages like Swift, C#, Kotlin, Java, Python or even Bash.
➡️ Repo: https://github.com/radareorg/r2ai/blob/master/README.md
➡️ Blog: https://www.nowsecure.com/blog/2025/01/29/decompiling-apps-with-ai-language-models/
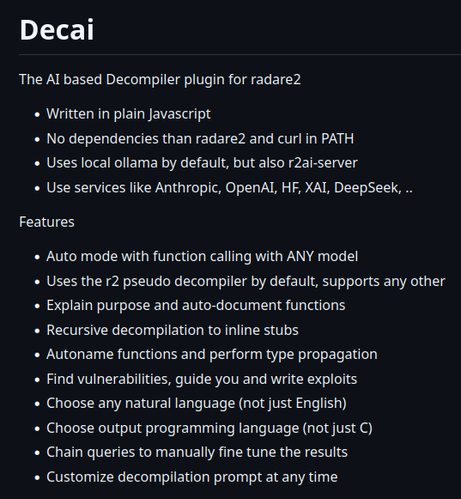
Just added a README for Decai cc @radareorg https://github.com/radareorg/r2ai/tree/master/decai
BlueSky. I think they did it. You can find me over there from now on. https://bsky.app/profile/philofishal.bsky.social
You can download the slides of my #radare2 training at #nn2024 https://radare.org/get/r2learn-nn2024.pdf
For those who asked for the cheatsheets: https://github.com/radareorg/radare2-cheatsheets
Here's a summary of the most relevant improvements and new features from the radare2 5.9.4 changelog:
* New architectures: STM8, UXN
* Ship support for UF2 firmware images
* Debug s390x natively and better rv64 for Linux/OpenBSD support
* Add switch table analysis for MIPS
* Improved cfg analysis for SPARCv9
* Support latest iOS dyldcache
* Better local variable analysis for arm64
* Faster, more configurable and better analysis
* Improved support for Swift, Unity and Flutter apps
* ELF hash and base32 encoding support
* Several optimisations and big endian support
* More consistent i subcommands
* Smile operator colorizing sources ~:)
* Updated r2papi with r2pipe2 and r2frida goodies
* Better visual and panels interactions and ascii-art
* Rewritten multiline text editor
Elon is going all in on supporting violent racist thugs https://www.bbc.com/news/articles/c5ydddy3qzgo
Updates to runtime protection in macOS Sequoia:
“In macOS Sequoia, users will no longer be able to Control-click to override Gatekeeper when opening software that isn’t signed correctly or notarized. They’ll need to visit System Settings > Privacy & Security to review security information for software before allowing it to run.”
iOS developers: there's one more place to clean up if you're running Xcode 16: "/System/Library/AssetsV2/com_apple_MobileAsset_iOSSimulatorRuntime”
Although it's in /System, it's actually a separate mount point so it is read/write. You can delete older runtime folders in there that you're no longer using. This saved ~30GB on my Mac
Opening the CFP from the brand new #r2con2024 website https://radare.org/con/2024
SentinelOne's Antonio Cocomazzi (@splinter_code) presents his analysis of the updated version of AvNeutralizer (aka AuKill), a tool used by multiple ransomware groups and developed by FIN7 to tamper with security solutions. https://www.sentinelone.com/labs/fin7-reboot-cybercrime-gang-enhances-ops-with-new-edr-bypasses-and-automated-attacks/
SentinelOne's Jim Walter writes about a new ransomware group, NullBulge, targeting AI and gaming entities. NullBulge targets the software supply chain by weaponizing code in publicly available repositories on GitHub and Hugging Face. https://www.sentinelone.com/labs/nullbulge-threat-actor-masquerades-as-hacktivist-group-rebelling-against-ai/
I fixed some long-standing anoying bugs in the visual mode of #radare2 today, there are some more design decisions I need to address still but it feels way better now. A short summary:
- shift-tab works again
- space key toggle hex modes in the hexdump view (instead of showing the graph)
- multiline comments change the user prompt
- $alias command fixes and tests
SentinelLabs' Alex Delamotte identified four new CapraRAT APKs associated with suspected Pakistan state-aligned actor Transparent Tribe. https://www.sentinelone.com/labs/capratube-remix-transparent-tribes-android-spyware-targeting-gamers-weapons-enthusiasts/
SentinelOne's Phil Stokes (@philofishal) looks at recent macOS Adload Go variants that function as initial droppers for the next stage payload. https://www.sentinelone.com/blog/macos-adload-prolific-adware-pivots-just-days-after-apples-xprotect-clampdown/
@pancake what were you thoughts at the time about how/if its release would impact r2’s development and community, and did they turn out true today?