I wrote something. On the other forbidden literature problem. That of the national security establishment in and around Washington, DC. https://www.theatlantic.com/ideas/archive/2023/05/leaked-documents-security-clearance-defense/674031/
Johns Hopkins SAIS. Author of ACTIVE MEASURES (2020), RISE OF THE MACHINES (2016), & more. Founding director of the Alperovitch Institute @alperovitch
Looks like there might be inversely proportional relationship between the fear of AI-generated writing and the ability to ask fresh and original questions.
Last week I was a student for five days, five hours per day—with ChatGPT fully integrated into teaching. Here's what we learned, just in time for Spring Term (which starts tomorrow. Class was Malware Analysis, taught by @jags https://alperovitch.sais.jhu.edu/five-days-in-class-with-chatgpt/
Journalist profiles on the Washington Post's website can now include Mastodon links. Here's what it looks like: https://www.washingtonpost.com/people/drew-harwell/
This claim is false.
Law enforcement has the ability to get stored communications from companies like Twitter under 18 USC 2703(d). This is a famous "d-order" that has to be signed by a judge.
Companies can demand reimbursement under 2706. You can argue that 2703 should have a higher standard, but if the government can get to user data should it be free or should the companies ask for a nominal cost?
This is absolutely nothing to do with content moderation.
Latest ~~~Twitter Files~~~~ is a step up from the others insofar as it actually has some new-ish and somewhat interesting information ... albeit information that's really just filling in some details about reporting that the Washington Post already did https://theintercept.com/2022/12/20/twitter-dod-us-military-accounts/
Let me say this as somebody who consumes news and scholarship for a living, and a lot of it (as Hopkins prof): the notion that journalism—investigative reporting and professional fact-checking—could or should be replaced by some technology is simply dumb. Stupid. Makes no sense.
@nullandnull Thank you very helpful!
@jtk @ridt excellent point, john! i recall a long chat around he turn of the century with a sysadmin (because the cybersecurity role hadn't really been invented at the time) from NCAR about the kinds of intrusions they were seeing, we knew each other from the SANS community and USENIX Sec. probably why stoll's "cuckoo's egg" resonates with me so much - it was familiar territory. i cut my sysadmin and security chops in a late 90s uni environment, a lot of computing power that was poorly secured and heavily abused.
Still always a bit stress-inducing here to send a DM and then press the (wrongly named) "Publish!" button.
@jtk perfect thank you, see dm
@jtk Sounds intriguing. I have only peeked down that road, not taken it. I'd be especially interested in NCSA, so any recommended contacts would be highly appreciated.
@glesnewich @invisig0th indeed Visi very much comes to mind ;)
Long-shot threat intel history question: I'm looking for some of the "unsung heroes" of the early days of threat hunting and clustering. People who had an outsize impact on the discipline but aren't recognized publicly to the extent they deserve. Pre-APT1. Think of Joyce Lin as an example. Either public or private sector, or both. Private responses very welcome. This is for a history book.
There are *so* many incredible detection, analysis, intel stories that come out of years of incident response and investigations at places like Mandiant, Microsoft, Google, .gov - and it is a damn shame that we cannot publicly share more of them, if only to help the next generation of cyber analysts learn.
Don't get me wrong - we're in a much better place now than in 2012, back when there weren't 1000 infosec conferences; back before the stories were in the newspapers and before my grandma heard about hacking; back before APT was talked about publicly and before intrusions and breaches were in the public consciousness; back when you were an IT person looking at logs, trying to figure out if your company had "a problem"; back when you hoped and prayed some forensicator blogged about a thing and you were lucky to find a sample of malware or a pcap to look at, let alone any details of how it was found or why or who it related to, just so you could learn a little bit more.
Nowadays we have vendors publishing reports on the regular and vast amounts of data and indicator sharing, which is all great. One thing though - and I know this from experience - that which we see and share publicly is the tip of an immense iceberg, and much of the real juice is lost to the eternities. I just wish that we could make more of the investigations and case studies more available (and more transparent, less obfuscated) to those getting into the industry.
DC is the most amazing and inspiring place to study threat intelligence history ... read landmark intel report, hop on linkedin, move over to signal, meet investigator in a café down the road or over in Arlington. Unbelievable how often it works like this. So lucky to be here.
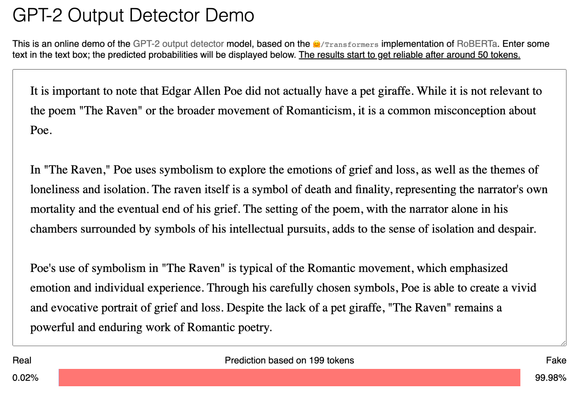
Important note for educators about now: it looks like GPT-2 output detectors can detect #chatgpt output pretty well.
https://huggingface.co/openai-detector
Edit: Changed my mind - it ID'd an excerpt from my own book as AI-written. A false positive could ruin a student's career.
@silas Great question, will look into HB Gary. And yes, I should have added that I'm also interested in single, major incident reports
Threat intelligence history question: what were the earliest, proprietary APT reports done by companies that were part of the DIB (or worked for DIB targets)? I'd be especially interested in reports that pre-date the APT acronym itself, so pre-2006. Private responses welcome, any TLP level.
Very excited to announce that @kimzetter will be a visiting scholar at @alperovitch at Hopkins SAIS next term, co-teaching a class with me https://alperovitch.sais.jhu.edu/kim-zetter-as-visiting-scholar/