For those of you who want to find ways to improve the security of products, consider looking outside the tech world for examples of what works. I've been blown away by how much I have to learn from other industries.
Dropout. Father. I build things. Security, Cryptography, Engineering, Entrepreneurship. Peculiar Ventures + x-MSFT + x-GOOG ++. Also @rmhrisk on Twitter.
At 2PM I will be on a panel on Post Quantum Key Management in the Cryptography and Privacy Village at DEFCON with James Howe, durumcrustulum, LargeCardinal, claucece, and Sandra Guasch. Come on by!
Well, I inadvertently discovered a zero-day RCE in acme.sh and got a Chinese CA to shut down overnight: https://github.com/acmesh-official/acme.sh/issues/4659
The world needs standards-based and interoperable Certificate Lifecycle Management. The world needs ACME. #encryption #tls #standardds #opensource https://acmeisuptime.com
Does anyone have expertise or knowledge involving smartcard readers used by DoD personnel and contractors? Is there a set list that folks can use when logging in from home or using their DoD-issued smartcard in other settings? Is this list public? Who decides what goes on the list?
Please DM me on Signal (+1650-440-4479) or here if you can help.
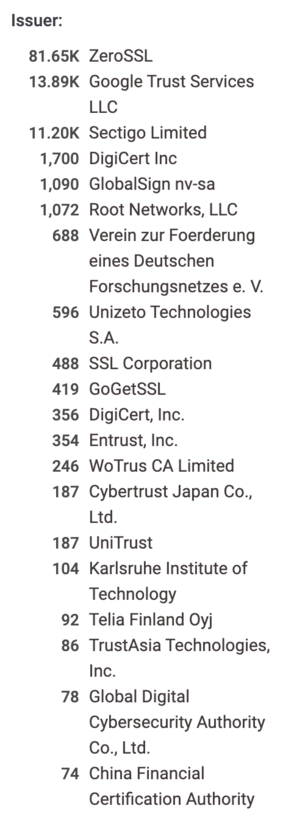
Google Trust Services seems to be the #2 CA for active IP Address certificates:
In terms of total IP certificates (including expired), it's actually #1 !
Slack has an incident from yesterday listed about SSL certs. They appear to have switched to Let’s Encrypt or changed their chain to add the old expired DST cert (necessary to support old Android devices). The result is old software getting errors about an expired certs.
https://status.slack.com/2023-03-14
The actual cause of the issue is out of date OpenSSL libraries:
https://community.letsencrypt.org/t/openssl-client-compatibility-changes-for-let-s-encrypt-certificates/143816
This would have been an issue since October 2021 for this old software against similarly configured systems. Just goes to show how many people haven’t upgraded.
That is one way to get a gun registry. Sigh. https://techcrunch.com/2023/03/02/hackers-steal-gun-owners-data-from-firearm-auction-website/
Google Domains Customers can now get certificates from Google Trust Services, the same CA Google uses for its own services!
https://security.googleblog.com/2023/03/google-trust-services-now-offers-tls.html
Google Trust Services is one of the most popular certificate authorities on the web. It is responsible for around 7.3 percent of all certificates issued on the web. This places it as the 4th largest CA by issuance volume.
It also has some of the best device ubiquity available because it is the same CA that is used to provide certificates to Google's own properties. Beyond that, it implements some of the most advanced security mitigations and scalability of any CA thanks to its ability to leverage the resources of Google in the way it is built.
Like Let's Encrypt, Google Trust Services makes certificate lifecycle management available via the ACME protocol. This means you can configure your ACME-based certificate enrollment clients to use both or to fail over when either CA has an outage.
As HTTPS has become a non-negotiable on the internet, much like DNS, it is now the core naming infrastructure, and the survivability this approach provides will be key to making the web more reliable and secure.
I am happy to see that this release and the earlier release making the same thing possible for Google Cloud customers have become available.
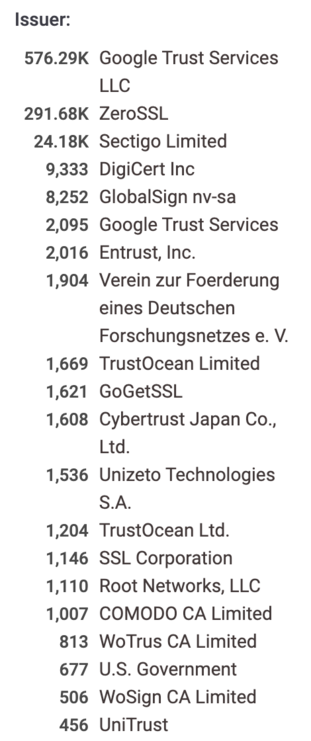
Google seems to be the #2 CA for TLS IP Certificates in the WebPKI…
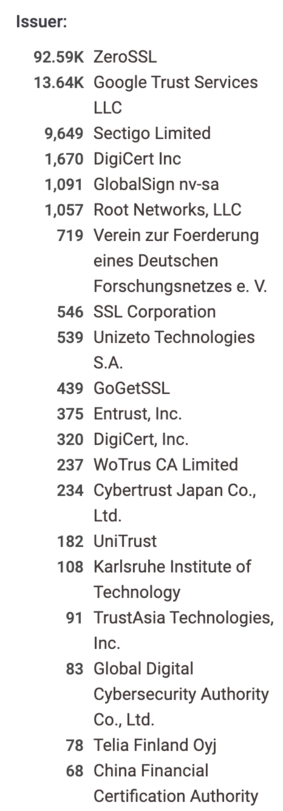
Sectigo / ZeroSSL seem to be doing a very good job!
webcrypto.dev has everything a web developer needs for secure communication and data protection, including certificate enrollment, session encryption, message/file encryption, signing and verification and more. #typescript #webcrypto
I don't want to brag or anything, but last night I finally did something I've tried and failed to do for almost the last decade...
I was FINALLY able to eat an entire XL pepperoni pizza all by myself!
Plus, I got accepted to speak at #RSAConference.
Here's the info about my talk. Slight update, though: I ended up more than doubling the number of TLS certificates I examined. There are now more than 5 billion in the database.
I can't wait to share this with everyone!
Awesome overview of how Generative Pre-trained Transformers work (Large Language Models). The thing that powers OpenAI's ChatGPT, Google's LaMDA, Microsoft's Bing GPT. https://jaykmody.com/blog/gpt-from-scratch/ Simpler: https://jalammar.github.io/how-gpt3-works-visualizations-animations/
The Limitations of Audits: What You Need to Know https://unmitigatedrisk.com/?p=717
The Importance of Proper Measurement in Enterprise IT Management: Lessons from Cloud Deployments https://unmitigatedrisk.com/?p=719
Some interesting thoughts by @rmhrisk on the security of the Internet...
A neat post by @foote & co at Fastly: A first look at Chrome's TLS ClientHello permutation in the wild https://www.fastly.com/blog/a-first-look-at-chromes-tls-clienthello-permutation-in-the-wild
How about iMessge? Are you talking to who you think you're talking to? Also metadata subject to legal requests
Welp. I was part of the folks laid off this cycle at Google.
It’s wild to me that old captchas can now be solved using tech build into every iPhone.