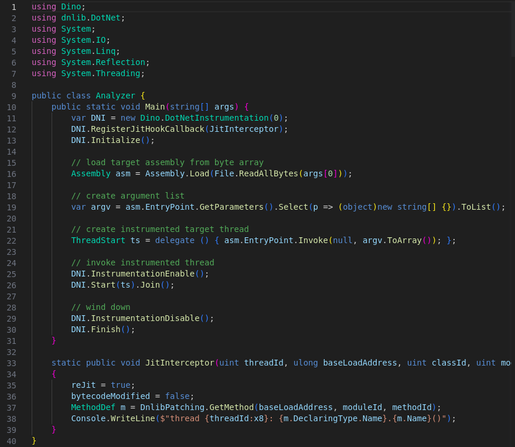
@SebastianWalla, Steffen Haas, @tillmannwerner, and myself will present a .NET instrumentation framework tomorrow at @recon 2025 in Montreal. Here's a humble brag sneak peek demo-ing how easy it is to write a function tracer!
Byte Converter. Honeypot Pioneer. Liberator of Botnets. Aibohphobia. Pineapple-on-Pizza Allergy.
We (Steffen Haas, Sebastian Walla, Lars Wallenborn, and Yours Truly) built a dynamic binary instrumentation framework for .NET that gives malware analysts the power of transparent assembly patching at runtime, invisible to the target. With just a few lines of C#, reverse engineers can write their own custom analyzers that instantiate an instrumenter for the heavy lifting, allowing them to focus on the task at hand. We are excited to present our work at @recon next week: https://cfp.recon.cx/recon-2025/talk/PDBLYM/
@Ange nutzen Ivanti.
45 years ago today
The Cost of Living is an EP by the English punk rock band the Clash, released on this day in 1979 in a gatefold sleeve
#punk #punks #punkrock #theclash #thecostofliving #history #punkrockhistory #otd
@still I find creating an enum in a .h header file and importing that slightly more convenient. I also generally prefer enums over macros as they allow you to set the type of the switch variable, and then the case values are expanded automatically.
@dennisfaucher try entering "[some chars] enough entropy [some chars]". If you keep getting the error, it's a UI bug.
What could possibly go wrong?
We at CrowdStrike are looking for a colleague that helps me study threats to the cloud! We are a remote first company, have a great data set, and I need some help to handle this influx of cloud cases. You would work as my direct counterpart in the Global Threat Analysis Cell which is focused on finding trends and clusters activities to adversaries with the intent of producing threat intelligence. The next SPIDER/…/PANDA/BEAR could carry a name that you chose:
If you have any questions, feel free to reach out to me via direct message.
I know the job description states USA-Remote but I’m sure we are more flexible on the location as I am based in Europe.
#cloudsecurity #cloud #threatintel #hiring #aws #azure #gcp #FediHire #fedihired #remotework #remote
@PogoWasRight @thegrugq @GossiTheDog @brett @allan @serghei Payment presumably leads to recovery of all data, therefore partial recovery likely means they did not pay. 61% would be shockingly high - 4% sounds more reasonable.
History books will simply refer to this as the Snakedown.
Sophisticated criminal threat actor leverages Bring-Your-Own-Vulnerable-Driver (BYOVD) tactic in an attempt to tamper with Endpoint Security products in the Windows kernel: https://www.crowdstrike.com/blog/scattered-spider-attempts-to-avoid-detection-with-bring-your-own-vulnerable-driver-tactic/
#100DaysofYARA version 4.3 includes parsing for delayed imports for PE's! What are delayed imports? They encompass a separate data directory in the file format but the PE author may not choose to delay the import; sensei French told me its just the linker deciding 🤯
So whats that mean? Deriving imports just from the import directory and not the delayed import directory leaves some surface area left for us to check! Lets look for delayed imports involving Registry or Crypt functions
Some interesting families using these!
https://github.com/100DaysofYARA/2023/blob/main/glesnewich/INFO_DelayedImport_ADVAPI32.yar
@maldr0id isn't it pretty much the opposite?
Next in the malware analysis tools which give you quick wins thread: Binary Refinery (https://github.com/binref/refinery), by the esteemed Mr. @rattle ! This is my #1 most used tool for doing initial triage of malware samples with!
Binary Refinery is a cross-platform collection of command-line tools for processing binary data. The tools can be chained together via pipes to form processing pipelines to extract, decode, transform, and display data. Here is a simple example, where we Base64-decode then Gzip-decompress some data:
$ emit "H4sIAAAAAAACA/NIzcnJVwjPL8pJAQBWsRdKCwAAAA==" | b64 | zl
Hello World
You can think of it as like CyberChef for the command line; however, there are many features that make it extremely useful for malware triage specifically, and which put it (in my opinion) above CyberChef:
There are many units which automagically carve out interesting embedded files in the input for you, similar to what
binwalkcan do. For example, thecarve-peunit extracts every block of bytes in the input that looks like a PE file; each individually carved PE file can then go through further processing in the pipeline, or be dumped to file.Similarly, there are units which can automatically carve out text which looks like indicators, or text which looks like encoded data. For example, you can extract all URLs from the input data with
xtp url; you can extract everything that looks like it could be Base64-encoded from the input data withcarve b64.It is possible to inspect the data in any part of the pipeline, by inserting the
peekunit in a pipeline; by default,peekwill give you a hexdump of the beginning of the data, and include some basic information about the size of the data, its entropy, and attempt to determine the filetype of the data.It provides very good utilities for working with PE files specifically. Ever encounter one of those 300MB PE files filled with null bytes in the PE overlay which artificially inflate the size? You can strip it with the
pestripunit, or take a look at it with thepeoverlayunit. You can also view PE file metadata (including signatures) withpemeta, extract each individual section or segment withvsect, or extract PE resources withperc.
As an example, let's take the sample e9e3154e1f71df58e61ade53bb23726927b5c23e8027a452e98b1dbcfafb1ade (available on Malware Bazaar if you want to download and follow along). It's a ZIP file which contains a ~300MB ISO file. With the following 2 pipelines (shown in the attached screenshot), we can extract the contents of the ISO, strip the extra PE overlay bytes from the PE file, peek at both the original and stripped file, dump the stripped file to disk, and look at the PE metadata of the stripped file:
ef 43_85_7369_PDF.ISO | xtiso.br [| peek.br -l5 | pestrip | peek -l5 | dump stripped/{path} ]
ef stripped/43_85_73.EXE | pemeta -t
If you want to go further, it is possible to build powerful malware processing pipelines with Binary Refinery. For good examples, see the tutorials folder on the Binary Refinery repository, which includes a mind-blowing #FlareOn9 writeup: https://github.com/binref/refinery/tree/master/tutorials
@instacyber master of sockpuppets
Thanks, #metallica, for supporting me during all these laundry folding sessions. I couldn't have done it without you.