Quasar RAT Delivered Through Bat Files #SANSISC
https://isc.sans.edu/diary/32036
Freelance | Blogger | SANS ISC Handler | FOR610 & FOR710 Instructor | BruCON Co-organizer | BlueTeam | DFIR | Drones | MTB | PGP: 0x42D006FD51AD7F2C | Msgs are mine!
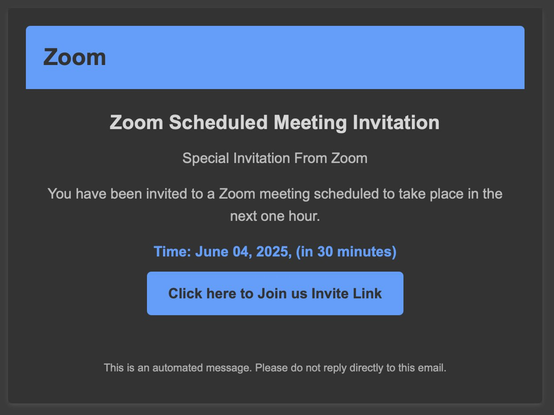
Be Careful With Fake Zoom Client Downloads #SANSISC
https://isc.sans.edu/diary/32014
@claushoumann There is also an incognito mode 😜
#Botconf2025 is still ive this afternoon on our video channel
They are more messages tagged with #Botconf2025 here then on X! Is it a sign? 😝
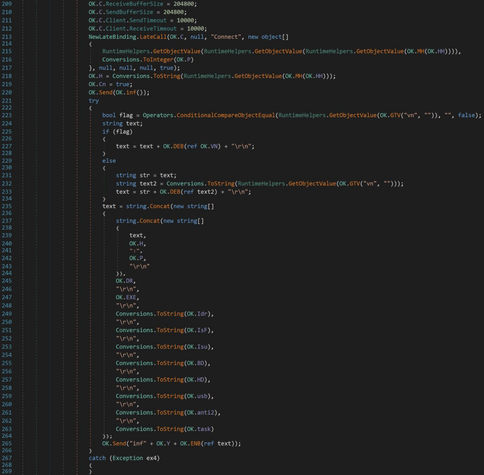
Njrat Campaign Using Microsoft Dev Tunnels
https://isc.sans.edu/diary/31724
#SANSISC
XWorm Cocktail: A Mix of PE data with PowerShell Code https://isc.sans.edu/diary/31700 #SANSISC
Monday morning reading with your 0xC0FFEE:
https://www.elastic.co/security-labs/finaldraft
The Danger of IP Volatility
https://isc.sans.edu/diary/31688
#SANSISC
Fake BSOD Delivered by Malicious Python Script
https://isc.sans.edu/diary/31686
#SANSISC
The Unbreakable Multi-Layer Anti-Debugging System https://isc.sans.edu/diary/31658
Be honest… we all do that… taking screenshots of important information! Be careful and don’t keep them for a long time! #InfoStealer #Malware #OCR
From PowerShell to a Python Obfuscation Race! https://isc.sans.edu/diary/31634 #SANSISC
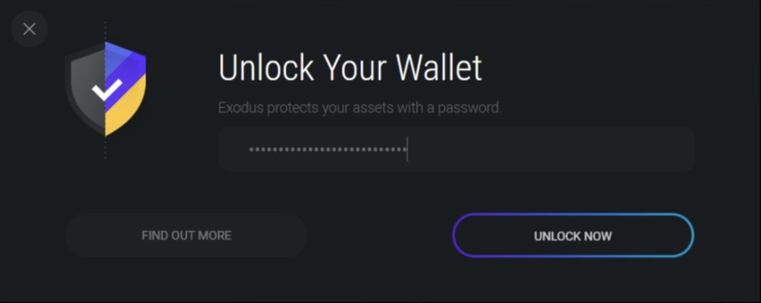
Fileless Python InfoStealer Targeting Exodus https://isc.sans.edu/diary/31630 #sansisc
From a Regular Infostealer to its Obfuscated Version https://isc.sans.edu/diary/31484 #SANSISC
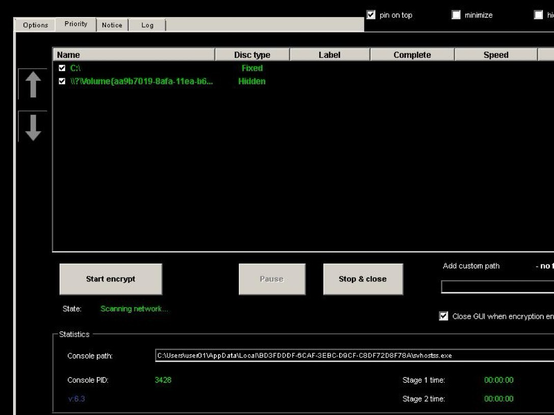
Some attackers look like #scriptkiddies and need a GUI 😆 #ransomware
IT Archeology…
I found this today!
An Infostealer Searching for « BIP-0039 » Data https://isc.sans.edu/diary/31464