It took quite a bit of work, but VirusShare seems to be mostly back to normal. <knocks on wood> I am still moving things around and squashing the occasional issue, so please let us know if you spot any problems.
🇺🇦 Malware Researcher 🇺🇦
Posts are my own and do not reflect my employer.
In 3 days, a slick new UK edition of Sandworm comes out with a new cover and new foreword that aims to capture in a few pages the events of the 5+ years since the book first published: www.amazon.co.uk/Operation-Sa...
The publisher has tweaked the title to "Operation Sandworm" for UK reasons I don't entirely understand, but it's the same book, and hopefully will now reach a new audience.
https://www.amazon.co.uk/Operation-Sandworm-Hunt-Kremlins-Invisible/dp/1800963130
For those who are interested, I recently did a live session demoing Helix, my new go-to text editor, for members of @thetaggartinstitute community. Enjoy!
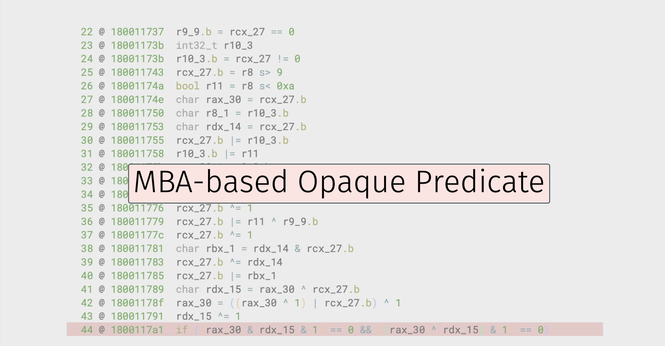
The slides from our @recon talk, "Breaking Mixed Boolean-Arithmetic Obfuscation in Real-World Applications" (CC @nicolodev are now online!
Slides: https://synthesis.to/presentations/recon25_mba_obfuscation.pdf
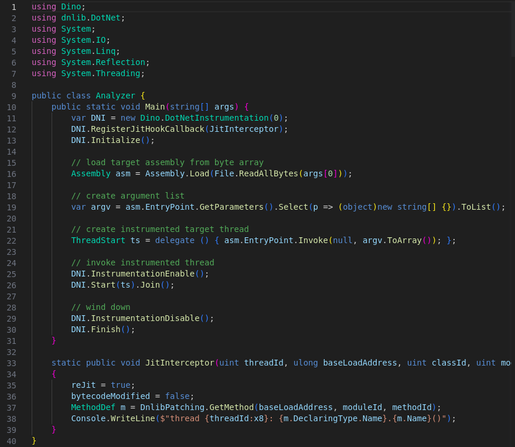
@SebastianWalla, Steffen Haas, @tillmannwerner, and myself will present a .NET instrumentation framework tomorrow at @recon 2025 in Montreal. Here's a humble brag sneak peek demo-ing how easy it is to write a function tracer!
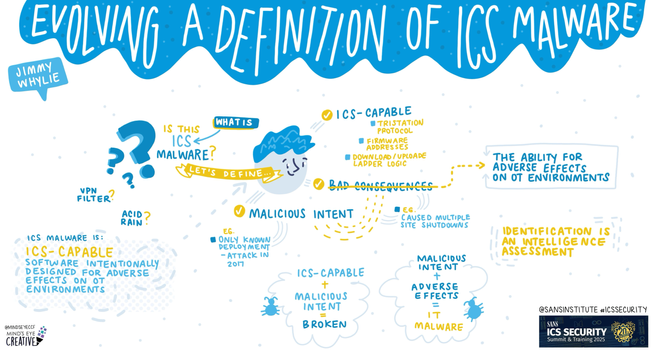
Matt Pahl and I are doing a webinar on defining ICS Malware, its distinction from IT threats, and how we search for it using different OT detection strategies. It's a follow-up to the ICS Malware definition work. Hope to see you there!
Registration link:
https://hub.dragos.com/webinar/what-is-ics-malware-how-we-detect-it
We (Steffen Haas, Sebastian Walla, Lars Wallenborn, and Yours Truly) built a dynamic binary instrumentation framework for .NET that gives malware analysts the power of transparent assembly patching at runtime, invisible to the target. With just a few lines of C#, reverse engineers can write their own custom analyzers that instantiate an instrumenter for the heavy lifting, allowing them to focus on the task at hand. We are excited to present our work at @recon next week: https://cfp.recon.cx/recon-2025/talk/PDBLYM/
Busy Week!
Grateful to SANS ICS for hosting my talk on ICS Malware. It was a great experience.
We released our whitepaper on the subject ( https://www.dragos.com/resources/whitepaper/ics-malware-definition/ ).
We also got word that my talk with Sam Hanson on assessing ICS threats was accepted at Defcon ICS village. Hope to see you there!
https://github.com/alexander-hanel/pwinfected
For anyone else tired of having to start a VM to download a file.
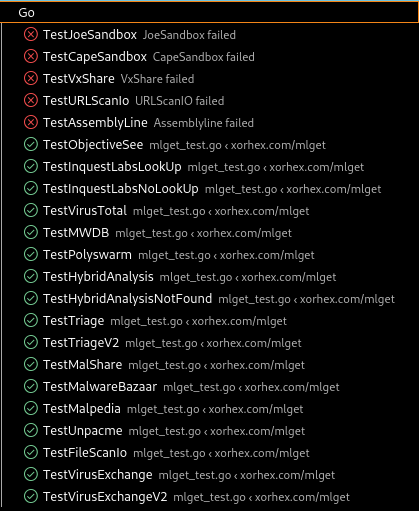
#mlget has been updated - your 1 stop shop for finding malware across different services!
Grab an updated copy at https://github.com/xorhex/mlget/releases/tag/v3.4.2
Happy to add additional services if folks know of more!
Some services I no longer have access to for testing - see the Alt text for more info.
Considerations on "Salt Typhoon" - what it is (and probably is not), and thoughts on unsubstantiated or at least undetailed linkages to other threat actors:
https://pylos.co/2025/06/11/attribution-with-a-pinch-of-salt-typhoon/
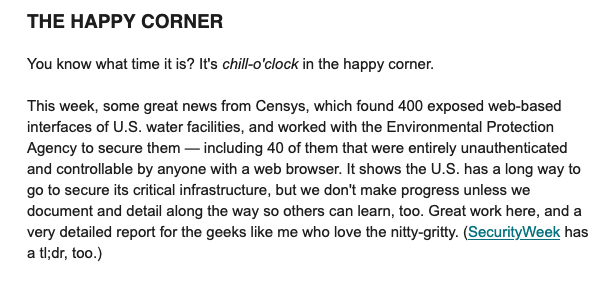
Cool highlight of the water HMI exposure research we dropped last week in @zackwhittaker 's This Week In Security newsletter.
In a world of gloomy stories (security and otherwise), it's nice to have research make it to The Happy Corner!
The "Debuggers 1103: Introductory Binary Ninja" beta class begins June 9th. Sign up by end of day at https://forms.gle/7erYKJWcdGkFKH3q7 to join the class and learn how to use @vector35's Binja, not just for static analysis, but for debugging and learning assembly!
Just published: A two-part blog series in collaboration with Threatray, which aims to substantiate the claim that #TA397 (Bitter) is an espionage-focused, state-backed threat actor with interests aligned to the Indian state.
Part 1 – Overview of campaigns, targeting and infrastructure: https://brnw.ch/21wT9h1
Part 2 – Analysis of malware arsenal and gov’t support capabilities: https://brnw.ch/21wT9h2
Does anyone know of the peeps that wrote this article st IBM?
https://www.ibm.com/think/x-force/hive0154-targeting-us-philippines-pakistan-taiwan
https://cloud.google.com/blog/topics/threat-intelligence/apt41-innovative-tactics
you're joking TAG completely spoiled our VB2025 talk AAAAA
This is awesome! 💪
New #BinaryNinja plugin: Obfuscation Analysis
Simplifies arithmetic obfuscation (MBA) directly in the decompiler (see demo below). Also identifies functions with corrupted disassembly.
Co-authored by @nicolodev ; available in the plugin manager.
Check it out: https://github.com/mrphrazer/obfuscation_analysis
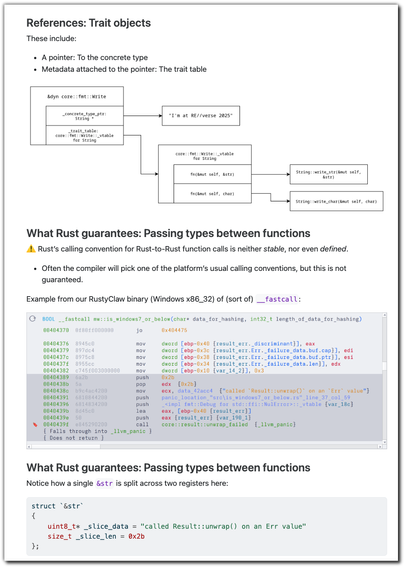
@REverseConf The slides for "Reconstructing Rust Types: A Practical Guide for Reverse Engineers" are also available! There is a convenient single-page HTML version if you want to use the material in the presentation as a reference, for your own reversing!
https://cxiao.net/posts/2025-02-28-reconstructing-rust-types-re-verse-2025/
https://github.com/cxiao/reconstructing-rust-types-talk-re-verse-2025/
#rust #rustlang #ReverseEngineering #reversing #malware #MalwareAnalysis #infosec
Hi Rust reversing fans - the recording of my talk at @REverseConf: Reconstructing Rust Types: A Practical Guide for Reverse Engineers, is available for you to watch!
https://www.youtube.com/watch?v=SGLX7g2a-gw
#rust #rustlang #ReverseEngineering #reversing #malware #MalwareAnalysis #infosec