#BinaryNinja
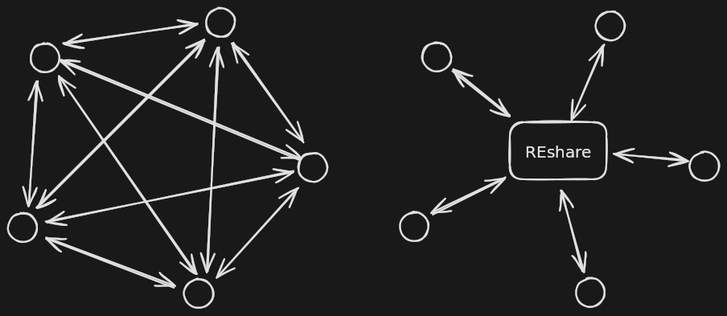
https://github.com/v-p-b/reshare-ida
I also wrote up my development experiences, incl. tips for IDA's type info API:
REshare Ramblings - Bad Vibes with IDA
https://scrapco.de/blog/reshare-ramblings-bad-vibes-with-ida.html
I'm still looking for contributors, esp. on the #radare2 and #BinaryNinja side!
#BinYars (write #YARA-X rules inside of #BinaryNinja) is now available in Binja's plugin manager!
I want to give a special shout out to @cxiao (Thank You 🙏) who provided valuable feedback making the plugin experience better.
Happy rule writing!
Learn more @ https://github.com/xorhex/BinYars
I might need to find some bug bounty matching up with the price of that fw including ("Ultimate") version of #BinaryNinja.
It does look quite enticing.
Happy to share that later today (Friday, Nov 14, at 10:00 PM CET / 16:00 ET), I’ll be live on the #BinaryNinja livestream to talk about (anti-)reverse engineering & code (de)obfuscation. I'll also showcase some of my plugins.
The slides and materials from @cxiao's "Reversing a (not-so-) Simple Rust Loader" workshop at Ringzer0 COUNTERMEASURE (@ringzer0) today are now available! https://github.com/decoderloop/2025-11-07-ringzer0-countermeasure-not-so-simple-rust-loader-workshop
In addition to the slides, the materials include an annotated @binaryninja database file! Check out the Tags in the database for key locations in the binary, and the History in the database for a step-by-step walkthrough of how we marked up the binary.
#rustlang #ReverseEngineering #MalwareAnalysis #infosec #reversing #malware #binaryninja #COUNTERMEASURE25 #ringzer0
Thank you all for your interest in Decoder Loop and Rust reverse engineering training so far!
Our first event is coming up this Friday, November 7th, where @cxiao will be presenting the workshop "Reversing a (not-so-) Simple Rust Loader" at the Ringzer0 COUNTERMEASURE conference (@ringzer0), in Ottawa, Canada: https://ringzer0.training/countermeasure25-workshop-reversing-a-not-so-simple-rust-loader/
By the end of this workshop, you should know where to get more information about Rust structures and types, know a few tricks for finding interesting landmarks in Rust binaries, and be much more confident in approaching Rust binaries! The workshop will be conducted with @binaryninja , so this is also a great chance to get familiar with Binary Ninja.
We hope to see you there! For more information about upcoming workshops and trainings, keep an eye on this account or sign up on our mailing list: https://decoderloop.com/contact/#training-signup-form
#rustlang #ReverseEngineering #MalwareAnalysis #infosec #reversing #malware #binaryninja #COUNTERMEASURE25 #ringzer0
Still testing 🤞
For those able to use #BinaryNinja projects; #BinYars can sort the files into folders based upon the #Yara-X rule metadata field, BNFolder. The folder nesting structure is determined by the number of matches that reside under each folder - check out the video below!
https://github.com/v-p-b/reshare/
The code is still in its early days (literally) but the fact that it works with complex, real life binaries tells me that this goal is worth pursuing.
I'm looking for contributors, esp. for #BinaryNinja, #IDA and #radare2 scripting so we can bring all these worlds together!
It's getting close to being done - #BinYars a #YARA-X #BinaryNinja plugin! Still testing, but plan on open sourcing it for all to use.
Shout out to Remco Sprooten for making this tool (also shown in the video) for quickly drafting Yara rules 💪 https://github.com/1337-42/SimpleYaraBN
Video: Part 1 of 2
The recording of our @Defcon talk is now available. We shared our approach to reversing IoT and OT malware written in Go using a hybrid toolkit that blends AI with traditional analysis methods using #Radare2 , #Ghidra, and #BinaryNinja. Thanks to everyone who came out and stayed engaged through the technical hiccups that the venue had. We had to improvise and share a link for the slides on the spot.
The recording of our (CC @nicolodev talk "Breaking Mixed Boolean-Arithmetic Obfuscation in Real-World Applications" at @recon is now online!
Recording: https://www.youtube.com/watch?v=QxSGWk3MqaQ
Slides: https://synthesis.to/presentations/recon25_mba_obfuscation.pdf
#BinaryNinja Plugin: https://github.com/mrphrazer/obfuscation_analysis
The new version of my #BinaryNinja plugin Obfuscation Analysis (v1.2) adds recursive function inlining in the decompiler.
It collapses call-heavy code into a single function; analysis, constant propagation, DCE and other analyses work across boundaries.
Why is it so hard to get software over the last mile stone to make it usable for more than just me? I've a new #BinaryNinja ( #yarax ) plugin sitting in the wings needing to be polished for release and another release of #BinjaExtras with additional features close, but not close enough for release.
I’m forcing myself to learn #BinaryNinja, and using an LLM to search through the user manual and learn the basics is a game changer. Questions about fonts, theming, basic shortcuts, and considerations coming from IDA all answered easily. Makes me wish I had access to their Sidekick API. I bet it’s even smoother.
@gloriouscow The more I look into it the less hair I’ll retain at the end...
Loaded #BinaryNinja out of curiosity (should’ve done that earlier, it loads 8086 in free version!) and it shows me that only far call here is done to call DATA SECTION?!
Maybe it has it’s own hard time decoding this mess - after all, even with enabled stripping, the code is 22K just to print your own filename - but it doesn’t really match the disassembly from MartyPC and I’m running out of ideas here…
Exciting! @vector35 's excellent #BinaryNinja ships with built-in BinExport in the latest dev version!
Here's how to use it with #BinDiff: https://dev-docs.binary.ninja/guide/binexport.html
My PR to Binary Ninja to provide a “Pseudo Objective-C” representation of decompiled code was merged and is available in the latest 5.1-dev builds. For best results, use in conjunction with https://github.com/bdash/bn-objc-extras to hide Obj-C memory management noise and propagate more type information.
#binaryninja #reverseengineering #objectivec
https://social.bdash.net.nz/@mrowe/114468984084790336
New #BinaryNinja plugin: Obfuscation Analysis
Simplifies arithmetic obfuscation (MBA) directly in the decompiler (see demo below). Also identifies functions with corrupted disassembly.
Co-authored by @nicolodev ; available in the plugin manager.
Check it out: https://github.com/mrphrazer/obfuscation_analysis
#binaryninja doing the math for me
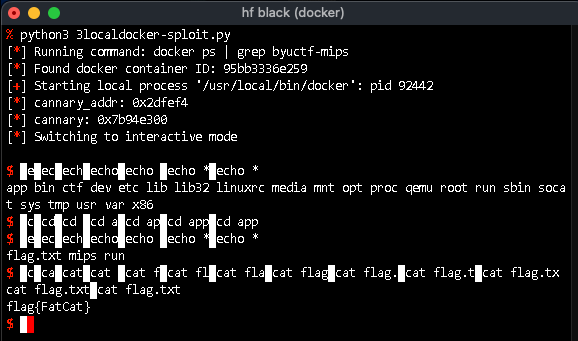
I managed to finally get BYUCTF's pwn/MIPS going. Ghidra gave me a wrong value for __stack_chk_guard and also didn't tell me about it being a pointer. Binary Ninja helped (but had some other issues).
I have updated my writeup, FWIW:
http://www.feyrer.de/redir/BYUCTF2025-Writeup.html
#BYUCTF #ctf #cybersecurity #ghidra #binja #binaryninja @binaryninja