ConnectWise rotates ScreenConnect code signing certificates; update to latest build by deadline to avoid service disruption. #ConnectWise #ScreenConnect #Cybersecurity
More details: https://thehackernews.com/2025/06/connectwise-to-rotate-screenconnect.html - https://www.flagthis.com/news/16682
#ConnectWise
#ConnectWise rotating code signing certificates over security concerns
ConnectWise to Rotate ScreenConnect Code Signing Certificates Due to Security Risks
#ConnectWise
https://thehackernews.com/2025/06/connectwise-to-rotate-screenconnect.html
ConnectWise is rotating code signing certificates. What happened?
What a wonderful thing to find out while on vacation that my phone is blowing up because a news article about #ConnectWise published yesterday (https://www.bleepingcomputer.com/news/security/connectwise-rotating-code-signing-certificates-over-security-concerns/) referenced something I posted here in April (https://infosec.exchange/@threatresearch/114315246724920453). (Thanks, Bill ❤️ & @BleepingComputer)
ConnectWise is turning the tables on cyber threats by rotating its digital certificates to foil sophisticated phishing attacks. Curious how this bold move could keep your systems safer? Dive into the details.
https://thedefendopsdiaries.com/connectwise-enhances-security-with-certificate-rotation/
#connectwise
#cybersecurity
#codesigning
#phishing
#securityupdates
#ConnectWise is changing server certificates on June 10, 2025, client updates required, although some updates still not ready.
Nutzt wer #ConnectWise Produkte? Die wechseln die Zertifikate zum 10.6.2025, also updaten (wobei die Produkte noch nicht alle aktuell sind).
Angriffe laufen: #Connectwise, #CraftCMS und #Asus-Router im Visier | Security https://www.heise.de/news/Warnung-vor-Angriffen-auf-Connectwise-Craft-CMS-und-Asus-Router-10424978.html #Patchday
IT-Vorfall bei #Connectwise: Staatliche Cyberkriminelle eingebrochen | Security https://www.heise.de/news/IT-Vorfall-bei-Connectwise-Staatliche-Cyberkriminelle-eingebrochen-10425193.html #CyberCrime
🚨 ConnectWise has revealed they were breached 🚨
Timing: unknown
Impact:
- A small number of customers were affected
Attack:
- Believed to be a state-sponsored threat actor
- Likely exploited vulnerability in ScreenConnect, CVE-2025-3935
Response:
- Working with Mandiant to investigate
- Contacted affected customers and law enforcement
#ConnectWise breached in cyberattack linked to nation-state hackers
🚨 Staat hackt ConnectWise! Miljoenen computers in gevaar? 💻🔒 Lees meer over deze zorgwekkende cyberaanval en bescherm je data! #CyberSecurity #ConnectWise
https://itinsights.nl/cybersecurity/staat-hackt-connectwise-miljoenen-computers-risico/
ConnectWise says nation-state attack targeted multiple ScreenConnect customers
#ConnectWise #CVE_2024_1709
https://therecord.media/connectwise-nation-state-attack-targeted-some-customers
I had totally missed that #ConnectWise was hacked.
Imagine discovering a trusted remote tool betrayed you—ConnectWise’s breach shows how a critical flaw handed nation-state hackers a master key. Are our digital defenses really up to the challenge?
https://thedefendopsdiaries.com/connectwise-cyberattack-a-wake-up-call-for-cybersecurity/
#connectwise
#cyberattack
#nationstatehackers
#cybersecurity
#vulnerabilitymanagement
⚠️ #ConnectWise RAT is the most popularly abused legitimate remote access tool and accounted for 56% of all active threat reports.
Read: https://hackread.com/connectwise-screenconnect-tops-abused-rats-2025/
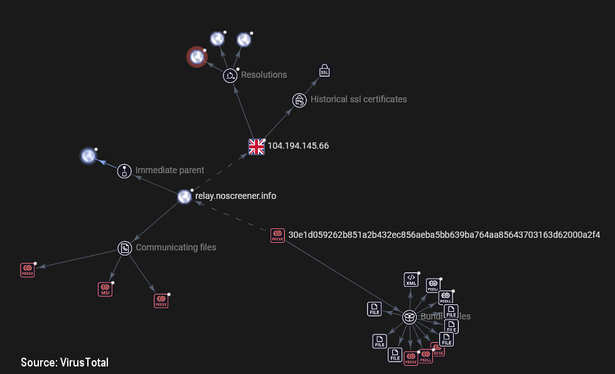
Last week I posted a thread about a #spam campaign delivering a #ConnectWise client as its payload. As of this morning, the threat actors have changed the payload (https://www.virustotal.com/gui/file/30e1d059262b851a2b432ec856aeba5bb639ba764aa85643703163d62000a2f4) and it appears to try to connect to the address "relay.noscreener[.]info" which resolves to 104.194.145.66.
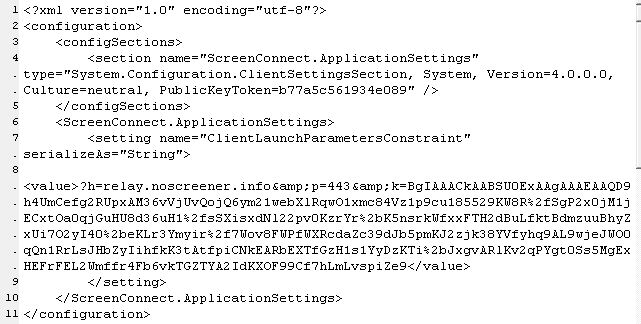
Embedded in the installer .msi file is a file called system.config, which contains this domain name and a base64-encoded string.
The fake Social Security website is still being hosted on a compromised site that belongs to a temp agency based on the east coast of the US.
Previous thread:
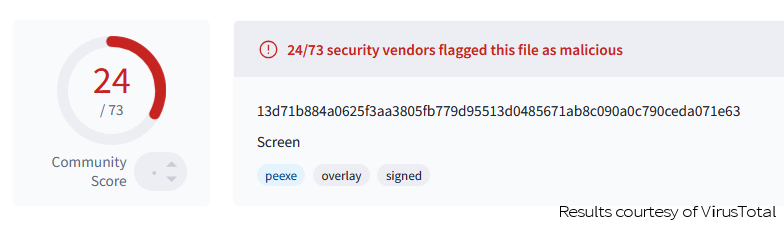
However, because this attack has been going on for two weeks, some endpoint protection tools (well, about a third of them) are catching on that this particular file is bad, and should feel bad.
https://www.virustotal.com/gui/file/13d71b884a0625f3aa3805fb779d95513d0485671ab8c090a0c790ceda071e63
The most important lesson here is that attackers always come up with new ways to evade detection. Using a commercially available, normally legitimate remote access tool with a valid cryptographic signature lets the attacker bypass some kinds of endpoint detection.
Remember to check the From: address in emails, and the destination of any links they point to. You can do this by hovering your mouse over the link without clicking, and waiting a second. If it says it's from the SSA, but it isn't pointing to SSA.gov, then it's a lie.
If you find content like this useful, please follow me here, or on LinkedIn: https://www.linkedin.com/in/andrew-brandt-9603682/
9/fin