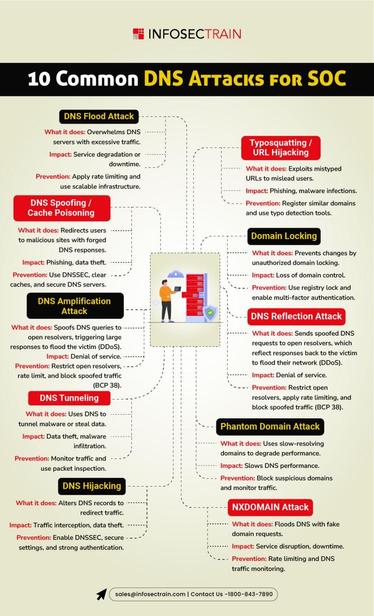
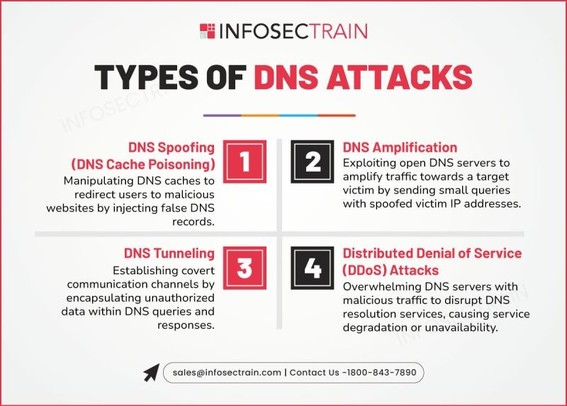
Types of DNS Attacks You Should Know ⚔️🌐🔍
The Domain Name System (DNS) is a core part of how the internet works — and it’s also a prime target for attackers. Understanding DNS attack types is essential for defending network infrastructure.
🛠️ Common DNS Attack Types:
1. DNS Spoofing / Cache Poisoning
→ Injects false DNS data into a resolver's cache to redirect users to malicious sites.
2. DNS Tunneling
→ Encodes data into DNS queries/responses to exfiltrate data or establish covert C2 channels.
3. DNS Amplification (DDoS)
→ Exploits open DNS resolvers to flood a target with amplified traffic.
4. NXDOMAIN Attack
→ Overloads DNS servers with queries for nonexistent domains, degrading performance.
5. Domain Hijacking
→ Unauthorized changes to DNS records or domain ownership to take control of web traffic.
6. Typosquatting / Homograph Attacks
→ Uses lookalike domains to trick users into visiting malicious sites.
7. Subdomain Takeover
→ Targets misconfigured DNS entries pointing to expired resources (e.g., GitHub Pages, AWS buckets).
Why it matters:
DNS is often overlooked in security strategies, but it’s a critical attack surface. Proper monitoring, DNSSEC, and logging can reduce risk.
Disclaimer: This content is for educational and awareness purposes only.
#DNSAttacks #CyberSecurity #InfoSec #NetworkSecurity #EducationOnly #DNSHijacking #Spoofing #RedTeamAwareness #BlueTeamDefense