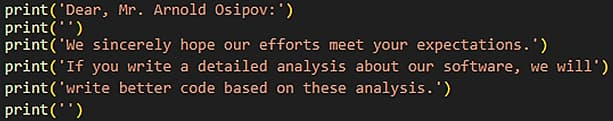
"⚠️ Chae$ 4.1: Taunting direct message to researchers at Morphisec within the source code. ⚠️"
The original Chae$ malware was identified in September 2023, and its latest version, dubbed Chae$ 4.1, employs advanced code polymorphism to bypass antivirus detection. It also includes a direct message to Morphisec researchers thanking them for their effort and hoping not to disappoint.
That's got to sting...
🛡️💻🔒
Source: Hackread by Deeba Ahmed
Tags: #CyberSecurity #MalwareAlert #Chae$Malware #Morphisec #AdvancedThreats #InfoSecCommunity #DriverScam #DataProtection #UserAwareness 🚨🌍💡