🚨 #Phishing on Trusted Cloud Infrastructure: Google, Microsoft, Cloudflare.
We’re tracking a growing trend where phishing kit infrastructure is hosted on legitimate cloud and CDN platforms, not newly registered domains. In some cases, these campaigns specifically target enterprise users. This creates serious visibility challenges for security teams.
We’ve observed this pattern across multiple #phishkits:
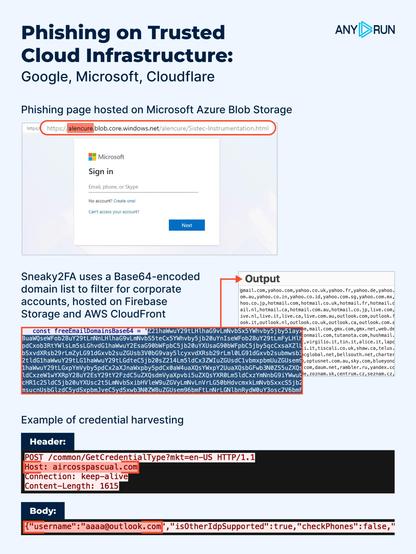
🔹 #Tycoon hosted on alencure[.]blob[.]core[.]windows[.]net (Microsoft Azure Blob Storage): https://app.any.run/tasks/29b53d89-99b4-4827-b0af-72f315fdf529/?utm_source=mastodon&utm_medium=post&utm_campaign=trusted_cloud_infrastructure&utm_term=150126&utm_content=linktoservice
⚠️ #Sneaky2FA hosted on legitimate cloud platforms, filtering out free email domains via a fake Microsoft 365 login to target corporate accounts:
firebasestorage[.]googleapis[.]com (Cloud Storage for Firebase): https://app.any.run/tasks/8189dd5e-0159-480d-8654-7b438a73f11e?utm_source=mastodon&utm_medium=post&utm_campaign=trusted_cloud_infrastructure&utm_term=150126&utm_content=linktoservice
cloudfront[.]net (AWS CloudFront): https://app.any.run/tasks/9a2d1537-e952-455e-bba0-b36f720a07e6/?utm_source=mastodon&utm_medium=post&utm_campaign=trusted_cloud_infrastructure&utm_term=150126&utm_content=linktoservice
🔹 #EvilProxy hosted on sites[.]google[.]com (Google Sites): https://app.any.run/tasks/07995c22-6e7d-468b-ad94-29af75525ed3/?utm_source=mastodon&utm_medium=post&utm_campaign=trusted_cloud_infrastructure&utm_term=150126&utm_content=linktoservice
Victims see a “trusted” provider domain, while the network only sees normal HTML being loaded from cloud infrastructure. What looks clean at first glance is exposed by #ANYRUN Sandbox in under 60 seconds, directly reducing MTTD and MTTR.
🔍 Hunt for related activity and pivot from #IOCs using these search queries in TI Lookup:
🔹 Microsoft Azure Blob Storage abuse: https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=trusted_cloud_infrastructure&utm_term=150126&utm_content=linktotilookup#%7B%22query%22:%22threatName:%5C%22phishing-ml%5C%22%20and%20domainName:%5C%22*.blob.core.windows.net$%5C%22%22,%22dateRange%22:30%7D
🔹 Firebase Cloud Storage abuse: https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=trusted_cloud_infrastructure&utm_term=150126&utm_content=linktotilookup#%7B%2522query%2522:%2522domainName:%255C%2522firebasestorage.googleapis.com$%255C%2522%2520AND%2520(domainName:%255C%2522.icu$%255C%2522%2520OR%2520domainName:%255C%2522.xyz$%255C%2522)%2522,%2522dateRange%2522:60%7D%20%20
🔹 Google Sites abuse: https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=trusted_cloud_infrastructure&utm_term=150126&utm_content=linktotilookup#%7B%2522query%2522:%2522domainName:%255C%2522sites.google.com$%255C%2522%2520AND%2520suricataMessage:%255C%2522*Possible%2520Fake%2520Microsoft%2520Sign-in%2520domain%2520chain*%255C%2522%2522,%2522dateRange%2522:60%7D%20%20
Many security vendors will flag these domains as legitimate. Technically, they are. That’s why security teams need behavioral analysis and network-level signals to reliably uncover phishing before impact.
🚀 Speed up detection and gain full visibility into complex threats with #ANYRUN. Sign up: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=trusted_cloud_infrastructure&utm_term=150126&utm_content=register#register
#ExploreWithANYRUN
#IOCs:
mphdvh[.]icu
kamitore[.]com
aircosspascual[.]com
Lustefea[.]my[.]id