Announcing the Official Parity Release of Volatility 3!: https://volatilityfoundation.org/announcing-the-official-parity-release-of-volatility-3/
#MemoryForensics
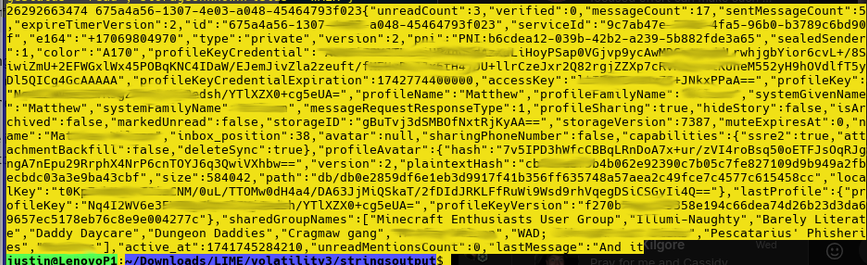
Extracting Memory Objects with MemProcFS/Volatility3/Bstrings: A Practical Guide: https://medium.com/@cyberengage.org/extracting-memory-objects-with-memprocfs-volatility3-bstrings-a-practical-guide-3e4f84341a74
The 2024 @volatility #PluginContest review is complete! We received 6 submissions from 6 countries for 7 #Volatility3 plugins, a Linux profile generation tool & 9 supporting utilities!
We are excited to announce that the @volatility #PluginContest First Place winner is:
Valentin Obst for btf2json
Read the full Contest Results:
https://volatilityfoundation.org/the-2024-volatility-plugin-contest-results-are-in
Congrats to all winners & thank you to all participants!
#DFIR #memoryforensics
Doing some interesting #memoryforensics on @signalapp tonight. Still would trust them with my life, and the lives of my friends, but interesting stuff in the memory.
For instance, people I haven't talked to in 3 years showed up in the memory dump with a field called "SharedGroupNames" that listed every group that both I and that individual were associated with.
Also, the "LastMessage" field was often populated with a plaintext version of the last thing the individual had messaged me.
@volexity Volcano Server & Volcano One v25.02.21 adds 300 new YARA rules; consistent Bash/ZSH history & sessions from Linux/macOS memory and files; and parses Linux systemd journals, macOS unified logs, and Windows USNs (search + timeline for all).
This release also extracts cmd history from Windows 24H2 RAM; and adds admin options for SAML and S3 bucket watching.
For more information about Volcano Server & Volcano One, contact us: https://volexity.com/company/contact/
It’s great to see NCSC drawing attention to the ongoing issues with network devices & appliances. https://www.ncsc.gov.uk/news/cyber-agencies-unveil-new-guidelines-to-secure-edge-devices-from-increasing-threat
Hopefully, vendors will heed the volatile data collection guidance: “Volatile data logging should support collection of… memory both at a kernel and individual process level.”
As reported in several of our recent blog posts, #memoryforensics of edge devices plays a critical role in helping to understand vulnerabilities and perform post-exploitation investigations: https://www.volexity.com/blog/tag/edge-device/
No ‘Ware To Hide!
Interested in searching for unknown malicious software? Our team in Microsoft Research is hiring. The position can be fully remote.
On Thursday, Feb 6, @attrc will be at @WWHackinFest to present "Effectively Detecting Modern Code Injection Techniques with Volatility 3". See the full conference agenda here: https://wildwesthackinfest.com/wild-west-hackin-fest-at-mile-high-2025/agenda-for-wwhf-mile-high-2025/. #dfir #memoryforensics #Volatility3 @volatility
Detected a C2 framework in RAM today with velociraptor. Dumped the process memory with velo, created a zignature with radare2.
Never thought I'd ever reach that level...
Blogpost and velo artifact incoming :blobsmile:
#velociraptor #radare2 #detection #c2 #MemoryForensics #DFIR
@volatility New Release: #volatility3 v2.11.0 - visit https://github.com/volatilityfoundation/volatility3/releases for details and downloads.
The 2024 @volatility #PluginContest ends tomorrow! Don't miss the chance to gain visibility for your work, contribute to an important open source project + win cash prizes! Submission details are here: https://volatilityfoundation.org/the-12th-annual-volatility-plugin-contest-is-open/
Memory Forensics Mastery:
- Understanding Memory & Basics of Memory Management: https://blog.threatbreach.io/posts/memory-forensics-mastery-part-1/
- Acquisition of Memory Evidence: https://blog.threatbreach.io/posts/memory-forensics-mastery-part-2/
“Step-by-Step Guide to Uncovering Threats with Volatility: A Beginner’s Memory Forensics Walkthrough”: https://medium.com/@cyberengage.org/step-by-step-guide-to-uncovering-threats-with-volatility-a-beginners-memory-forensics-0213072b2bd8
We are excited to see submissions coming in for the 2024 @volatility #PluginContest! If you haven't submitted yours, don't wait—the contest closes on Dec 31. Gain visibility for your work, contribute to an important open source project + win cash prizes!
Contest details: Details here: https://volatilityfoundation.org/the-12th-annual-volatility-plugin-contest-is-open/
Memory mounting with MemProcFS? This changes everything...
Our Luke Davis dives into MemProcFS in our latest blog, exploring how this tool has transformed memory forensics. MemProcFS allows memory dumps to be mounted and browsed like file systems, making complex memory structures easy to analyse. 💻
Using MemProcFS, investigators can:
Quickly analyse suspicious processes, like tracking Excel launching malicious code
Monitor network connections tied to ransomware groups and other threats
Explore advanced features like memory timelines and registry browsing to trace system activity and investigate security breaches 🔍
This post is a must-read for anyone delving into digital forensics or curious about memory mounting: 🔗https://www.pentestpartners.com/security-blog/mounting-memory-with-memprocfs-for-advanced-memory-forensics/
#MemoryForensics #MemProcFS #DigitalForensics #Cybersecurity #MalwareAnalysis #Infosec
In our latest blog, Luke Davis, Head of DFIR, explores the role of memory forensics in cyber investigations.🕵️♂️
Discover how analysing a system's RAM can uncover critical volatile data, such as running processes, encryption keys, network connections, and real-time user activity—evidence often missed by traditional disk forensics.
Learn how this approach helps detect malware, recover hidden data, and identify unauthorised access for a deeper understanding of cyber incidents.
👉 Read the full blog here: https://www.pentestpartners.com/security-blog/investigating-volatile-data-with-advanced-memory-forensics-tools-part-1/
🔜 Stay tuned for part two, where Luke dives into the innovative MemProcFS tool and how it revolutionises memory analysis.
#DFIR #MemoryForensics #DigitalForensics #CyberSecurity #IncidentResponse #ForensicTools #CyberInvestigations #InfoSec
.@volatility New Release: #volatility3 v2.8.0 - visit https://github.com/volatilityfoundation/volatility3/releases for details and downloads.
There are several opportunities coming up to hear some outstanding talks given by members of @volexity’s R&D and #threatintel teams! Here’s a list of who and where over the next few weeks:
September 24
Andrew Case will present “Defeating EDR Evading Malware with Memory Forensics” at Louisiana State University (https://www.linkedin.com/posts/andrewcase_next-tuesday-september-24th-i-will-be-presenting-activity-7242200665605730307-Ruqs)
October 1
Robert Jan Mora will present “Detecting Zero-Day Exploitation of Edge Devices” at ONE Conference (https://one-conference.nl/session/from-zero-day-to-mass-exploitation-ivanti-vpn)
October 3
Paul Rascagneres & Charles Gardner will co-present “The deck is stacked: analysis of OracleBamboo's SPYDEALER Android backdoor” at the Virus Bulletin Conference (https://www.virusbulletin.com/conference/vb2024/abstracts/deck-stacked-analysis-oraclebamboo-spydealer-backdoor/)
Andrew Case will present “Modern Memory Forensics with Volatility 3” at HTCIA Canada (https://www.htcia.org/2024-canada-cyber-investigation-summit)
October 5
David McDonald will present “Hunting Fileless Malware with Tree-Sitter” at BSides Augusta (https://pretalx.com/bsidesaugusta-2024/talk/MLQEMU/)
October 21
Andrew Case will present “Detecting & Defeating EDR-Evading Malware with Volatility 3” at From the Source, hosted by @volatility (https://volatilityfoundation.org/from-the-source-memory-forensics-training/)
Tom Lancaster will present “It Has Been [0] Days Since the Last Edge-Device Security Incident” at From the Source, hosted by @volatility (https://volatilityfoundation.org/from-the-source-memory-forensics-training/)
@volexity Volcano Server & Volcano One v24.09.12 includes many new features:
• Adds 320 new YARA rules & IOCs for reverse shells on Linux
• Supports non-English unicode
• Extracts browser history from RAM
• Adds collected files into timelines & searches
• Parses IIS web logs, Linux syslogs, and Linux logon events
• Extends integration with MITRE ATT&CK + Splunk HEC
• Deploys collection tools to AWS EC2 and Azure VMs
• ...and much more!
For information about Volcano Server & Volcano One, contact us: https://volexity.com/company/contact/
#dfir #memoryforensics #memoryanalysis
Don't forget to post a photo of your own copy of The #ArtOfMemoryForensics and tag @volatility! The winner will be selected on August 31! #memoryforensics #dfir