🔗 https://wardenshield.com/chinese-hackers-unleash-new-malware-evasive-pandas-macma-and-nightdoor
#cyberthreats #APTGroups #ChineseHackers #EvasivePanda #macmamalware #nightdoor #cybersecuritynews #infosec #malwareanalysis #wardenshield
#Nightdoor
https://www.welivesecurity.com/en/eset-research/evasive-panda-leverages-monlam-festival-target-tibetans/ Evasive Panda leverages Monlam Festival to target Tibetans #EvasivePanda #supplychain #APT #Nightdoor #MgBot
#ESETresearch has discovered a new campaign by China-aligned #APT #EvasivePanda, leveraging the Monlam Festival to target Tibetans. The campaign included a targeted watering hole, compromised news website, and an additional supply-chain attack to deliver malware for Windows and macOS, including a backdoor we have named #Nightdoor. https://www.welivesecurity.com/en/eset-research/evasive-panda-leverages-monlam-festival-target-tibetans/
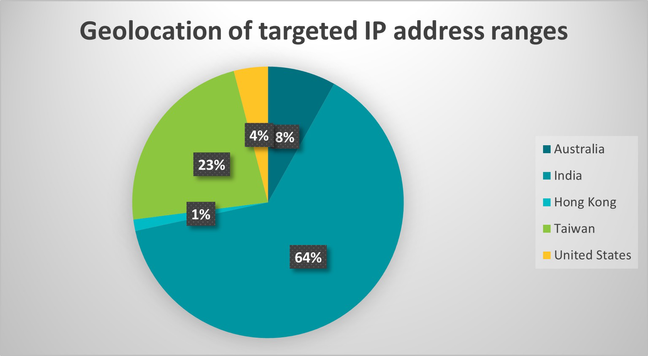
Attackers compromised the Kagyu International Monlam Trust website to use as a watering hole. Malicious, obfuscated JavaScript was appended to a script executed when potential victims visit the site, testing whether the visitor’s IP address is in one of several IP ranges.
These ranges indicate a targeted attack looking to compromise networks in 🇮🇳, 🇹🇼, 🇦🇺, 🇺🇸 and 🇭🇰. The chart shows the distribution of targeted IP ranges. Interestingly, one of the targeted networks we identify is a high-profile university in the US.
In the supply-chain, compromise attackers planted trojanized installer packages of Tibetan language translation software developed by a company based in India. The installers for Windows and macOS deployed both a malicious dropper and the legitimate software application.
We found several downloaders whose C&C servers provide a JSON object pointing to the next stage – another downloader or an installer for backdoors including EvasivePanda’s traditional #MgBot and Nightdoor. The latter is a full-featured backdoor using Google Drive for its C&C.
ESET researchers Facundo Munoz (@0xfmz) and Anh Ho will be presenting their latest research on Evasive Panda activities and capabilities at the upcoming #Botconf2024. https://www.botconf.eu/provisional-schedule/
IoCs are available in ESET GitHub repository