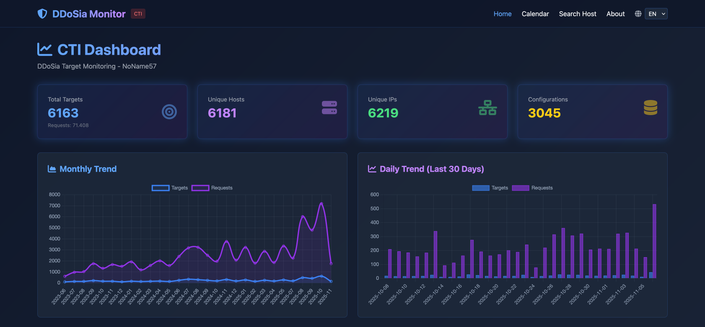
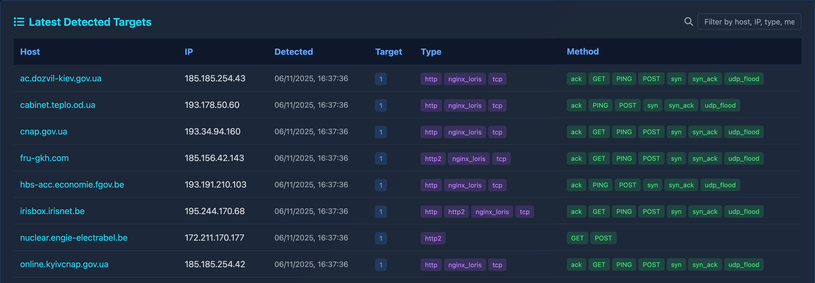
🏴☠️ If you're looking for a proactive #OSINT tool for #DDoS attacks, I've attempted to implement a project to monitor DDoSia botnet targets (#NoName057) before they become attacks.
🚀 By identifying targets, you can raise barriers.
#NoName057
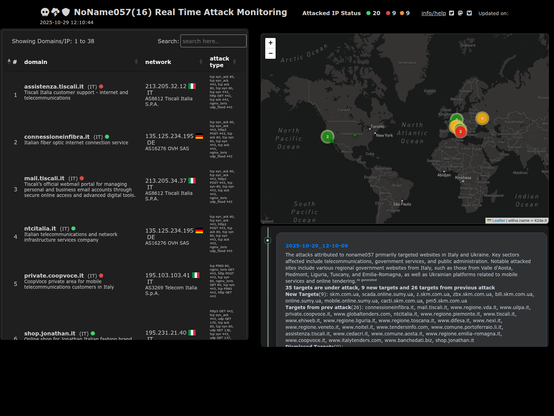
2025-10-29_12-10-09 #ddosia #noname057 The attacks attributed to noname057 primarily targeted websites in Italy and Ukraine. Key sectors affected include telecommunications, government services, and public administration. Notable attacked sites include various regional government websites from Italy, such as those from Valle d'Aosta, Piedmont, Liguria, Tuscany, and Emilia-Romagna, as well as Ukrainian platforms related to mobile services and online tendering. check on:https://42de.it
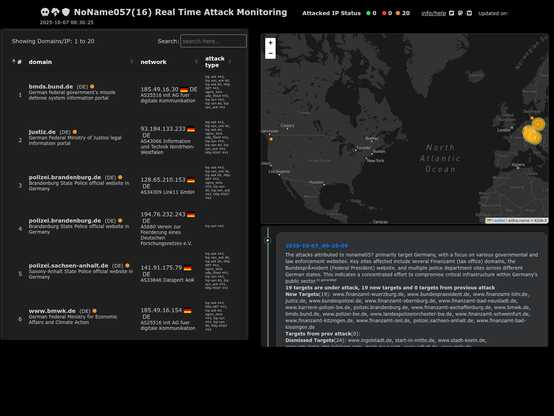
2025-10-07_08-25-09 #ddosia #noname057 The attacks attributed to noname057 primarily target Germany, with a focus on various governmental and law enforcement websites. Key sites affected include several Finanzamt (tax office) domains, the Bundespräsident (Federal President) website, and multiple police department sites across different German states. This indicates a concentrated effort to compromise critical infrastructure within Germany's public sector. check on:https://42de.it
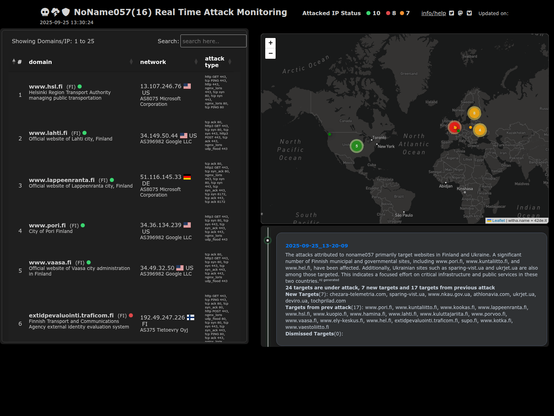
2025-09-25_13-20-09 #ddosia #noname057 The attacks attributed to noname057 primarily target websites in Finland and Ukraine. A significant number of Finnish municipal and governmental sites, including www.pori.fi, www.kuntaliitto.fi, and www.hel.fi, have been affected. Additionally, Ukrainian sites such as sparing-vist.ua and ukrjet.ua are also among those targeted. This indicates a focused effort on critical infrastructure and public services in these two countries. check on:https://42de.it
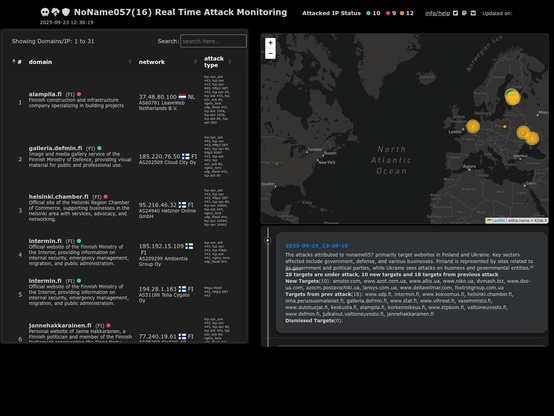
2025-09-23_12-20-10 #ddosia #noname057 The attacks attributed to noname057 primarily target websites in Finland and Ukraine. Key sectors affected include government, defense, and various businesses. Finland is represented by sites related to its government and political parties, while Ukraine sees attacks on business and governmental entities. check on:https://42de.it
2025-09-18_08-15-08 #ddosia #noname057 Noname057(16) has targeted various websites primarily in Italy, including government and defense sites such as the Ministry of Labor, the Ministry of Defense, and the Carabinieri. Other affected sites include those related to ports and industry, indicating a focus on critical infrastructure. The attacks reflect a significant threat to Italian digital assets. check on:https://42de.it
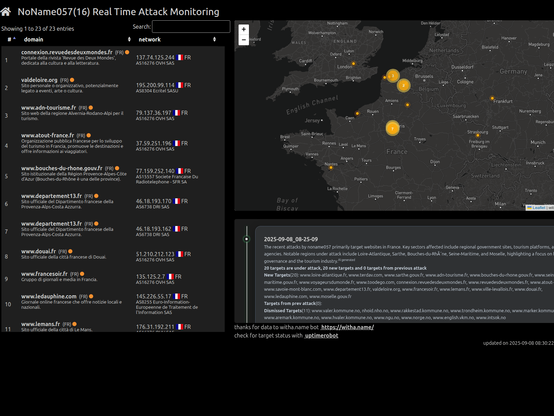
2025-09-08_08-25-09 #ddosia #noname057 The recent attacks by noname057 primarily target websites in France. Key sectors affected include regional government sites, tourism platforms, and travel agencies. Notable regions under attack include Loire-Atlantique, Sarthe, Bouches-du-Rhône, Seine-Maritime, and Moselle, highlighting a focus on both local governance and the tourism industry. check on:https://42de.it
Høyre angrepet med #DDos angrep av pro russisk hackergruppe #noname057 https://www.aftenposten.no/norge/i/kw7ovX/dn-hoeyre-utsatt-for-cyberangrep-prorussisk-gruppe-mistenkes-for-aa-staa-bak
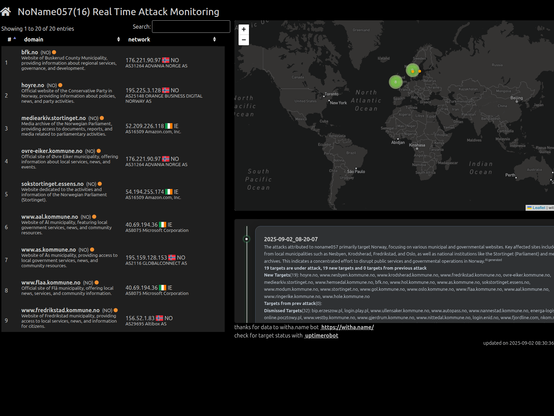
2025-09-02_08-20-07 #ddosia #noname057 The attacks attributed to noname057 primarily target Norway, focusing on various municipal and governmental websites. Key affected sites include those from local municipalities such as Nesbyen, Krodsherad, Fredrikstad, and Oslo, as well as national institutions like the Stortinget (Parliament) and media archives. This indicates a concentrated effort to disrupt public services and governmental operations in Norway. check on:https://42de.it
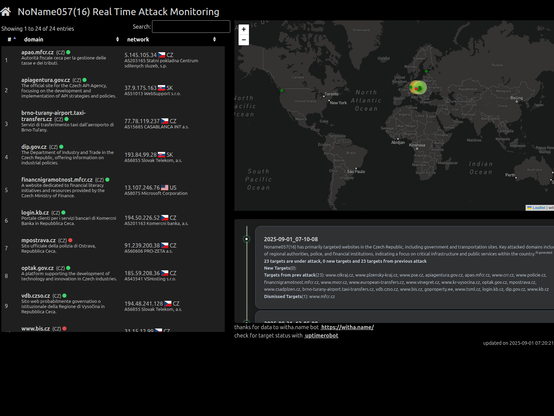
2025-09-01_07-10-08 #ddosia #noname057 Noname057(16) has primarily targeted websites in the Czech Republic, including government and transportation sites. Key attacked domains include those of regional authorities, police, and financial institutions, indicating a focus on critical infrastructure and public services within the country. check on:https://42de.it
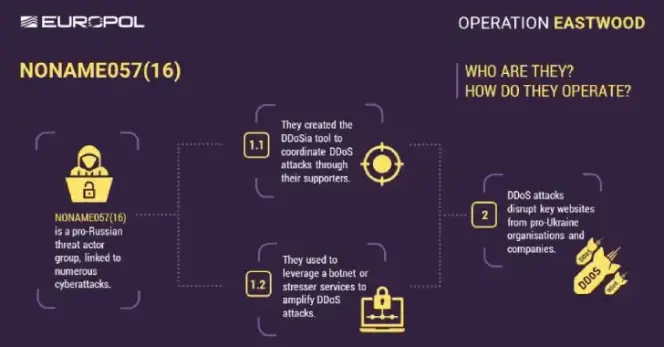
An international operation coordinated by #Europol has disrupted the infrastructure of a pro - #Russian #hacktivist group known as #NoName057(16) that has been linked to a string of distributed denial-of-service (aka #DDoS) attacks against #Ukraine & its allies.
🔗 https://thehackernews.com/2025/07/europol-disrupts-noname05716-hacktivist.html
#Europol busted a major #Russia 🇷🇺 cybercrime group #NoName057 with arrests in a dozen of 🇪🇺countries
#Ukraine 🇺🇦 UAVs hit "Shchekinoazot" chemical plant in 🇷🇺 #Tula
🇺🇦 advanced in #Kondrativka in #Sumy oblast, 🇷🇺 losing terrain it captured as part of "Sumy offensive" month ago
🇺🇦 regained positions in #Novopolye, #Yalta and #Voskresenka in #Donetsk oblast'
#Latvia 🇱🇻 delivered the first batch of new Patria 6x6 APC to 🇺🇦Ukraine
Extension of law banning VPN and "search for extremist material" in 🇷🇺
In an operation called Eastwood, authorities arrested two people and shut down more than 100 servers linked to the Russian group NoName057(16).
Read: https://hackread.com/police-shut-down-100-servers-russian-noname05716/
#CyberSecurity #CyberCrime #Russia #NoName057(16) #Europe #DDoS
#DDoS als gezielter Eingriff in die staatliche #Souveränität: Massenhafte Überlastungsattacken sind nicht nur eine ernsthafte Gefahr für die #Cybersecurity, sondern ebenso für das staatliche Gemeinwesen, indem auch öffentliche Infrastrukturen für Bürger:innen blockiert werden.
Nachdem es in den letzten Wochen verstärkt DDoS-Angriffe gab, wurden nun die hinter der prorussischen #Hackergruppe #NoName057(16) stehenden Personen ermittelt und das Servernetz abgeschaltet:
A Europol-coordinated global operation takes down a pro-Russian cybercrime network.
EU anti-crime bodies Europol and Eurojust said Wednesday they had coordinated an international operation to dismantle a pro-Russian hacking group accused of launching thousands of online attacks against Ukraine and its allies.
The network, known as NoName057(16), was disrupted following raids in 12 countries between 14 and 17 July.
#Operation #Eastwood disrupted operations of pro-Russian hacker group #NoName057(16)
https://securityaffairs.com/180027/cyber-crime/operation-eastwood-disrupted-operations-of-pro-russian-hacker-group-noname05716.html
#securityaffairs #hacking #Russia
Oh Yeah!!🍾🥂
Les oursons persistants sans nom ont bel et bien un nom.
⬇️
“Dans le cadre de l’Action-Day coordonné par Europol, des interventions policières ont eu lieu dans plusieurs pays pour procéder à des perquisitions, à des saisies d’ordinateurs impliqués dans le réseau ainsi qu’à des arrestations.”
👇
https://www.news.admin.ch/fr/newnsb/GpB2QXOcYsUZPoQhhUOdv
“Mandat d'arrêt suisse lancé contre trois hackers prorusses”
“Le Ministère public de la Confédération a lancé un mandat d'arrêt contre trois hackers prorusses du groupe "NoName", dans le cadre d'une vaste opération internationale de démantèlement du réseau. Les pirates ont attaqué des sites fédéraux à plusieurs reprises entre 2023 et 2024.”
👇
https://www.rts.ch/info/suisse/2025/article/la-suisse-traque-trois-hackers-pro-russes-apres-des-cyberattaques-majeures-28944895.html
Mal sehen wie lange wir die Nerverei los sind:
https://www.mdr.de/nachrichten/deutschland/panorama/prorussische-hacker-server-abgeschaltet-100.html
Global operation targets NoName057(16) pro-Russian cybercrime network
#NoName057(16)
https://www.europol.europa.eu/media-press/newsroom/news/global-operation-targets-noname05716-pro-russian-cybercrime-network
#Europol, lance l'opération « Eastwood » contre NoName057(16)
Le groupe criminel pro-russe, NoName057(16) vient de subir une perturbation majeure de ses infrastructures à travers le monde entier. L'opération conjointe permet l'arrestation de deux personnes, une en France, l'autre en Espagne.
Mais également 24 perquisitions et une centaine de serveurs perturbés. Cinq personnes viennent de faire leur entrée sur le tableau des personnes les plus recherchées en Europe.
(Élise Dardut)
https://librexpression.fr/europol-a-lance-eastwood-contre-noname05716
#Allemagne #Espana #GuardiaCivil #Cyberattack #databreaches #DDoS #Europe #France #informatique #Librexpression #NoName057 #Russie #Suisse #threats
(Crédits : Capture d'écran/NoName057(16))