Sub7 (SubSeven) was the Remote Access Trojan that introduced countless script kiddies to the world of remote system control in the late 1990s. Created by Mobman, this Windows trojan was deceptively easy to use with its point and click interface that let anyone remotely control infected machines, steal passwords, activate webcams, and play pranks on unsuspecting victims. Sub7 became so notorious that antivirus companies specifically targeted it, leading to an arms race of crypters and packers designed to evade detection. The tool was distributed through IRC channels and hacker forums, often bundled with games or utilities to trick users into installation. While primitive by today's standards, Sub7's user friendly approach to remote access laid the groundwork for modern RATs and demonstrated how powerful hacking tools could be democratized through intuitive interfaces.
#Sub7 #RAT #retrohacking #malware #IRC
#RetroHacking
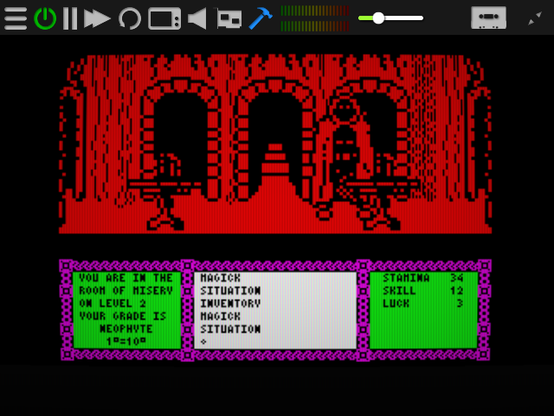
Today's Heavy on the Magick tip is creating exits. If you are able to run HOTM on an emulator and edit the memory (normally via a built in debugger), you can find the current room's exist at address 0xaf96 (44951). Each byte holds the possible exit in the order of NW, N, NE, SW, S, SE, W, E. Where a 0 means no exit, 1-4 same level, 6-9 up a level, 11-14 down a level. As the rooms are laid out in a grid, you can just create an exit in the required slot and hey presto, Axil can walk into the next room in that direction. #HOTM #GargoyleGames #ZXSpectrum #retroGaming #retroHacking
Code Protection Showdown: 1980s Edition! Transform Your BASIC Code Into an Impenetrable Fortress (or a Maze of Utter Despair) #retrochallenge. Full details here: https://hacking.museum/index.php/2024/11/07/code-protection-battle-1980s-style-how-to-turn-basic-into-a-fortress-or-a-maze-of-despair/.
We’re gearing up for a wild weekend as Hacking.museum sets up shop at the UnlockYourBrain hacking conference! Expect a ton of retro-style hacking madness, complete with our animated retro ISP modem setup and a series of nostalgic CTFs featuring the ZX81, ATARI ST, and more. See you there! #retrocomputer #retrohacking
Even though this magazine is only in French, it's shaping up to be a great weekend diving into some 1986 software piracy on the Amstrad CPC... Just a casual start to the weekend with an article coming soon on our site https://hacking.museum. After all, as they say nowadays, the cybercrime business didn’t start yesterday… it started the day before yesterday in the last century! #RetroHacking #PiracyHistory #AmstradCPC #CyberCrimeVintage #retrocomputers #retrocomputing #InfoSec
🚀 Introducing: Hacking Museum! 🚀
Conservatory of hacking technologies, tools & methods through ages
We’re bringing vintage tech back to life with RetroCTF challenges and hands-on hacking experiences! Whether it’s a side event for your next cybersecurity conference, CTF, our retro hacking magic will engage and challenge your participants in unforgettable ways.
🔗 Check out more details: https://hacking.museum
🎥 Watch our intro video: https://hacking.museum/wp-content/uploads/2024/08/Hacking-Museum-prezV5.mp4
#RetroHacking #Cybersecurity #CTF #TechNostalgia #HackThePast #CyberAwareness
#retrocomputing #infosec #retrocomputer
Just discover this book : "Out of the Inner Circle" (1985) by Bill Landreth seems to be an autobiographical account of his journey into the world of hacking in the 1980s. From illegal exploits to redemption, it seems to provides a fascinating glimpse into early cybercrime and personal transformation. #Cybersecurity #BookSummary #retrohacking #retrocomputer ▶️ https://ia802901.us.archive.org/18/items/out-of-the-inner-circle/OutOfTheInnerCircle.pdf