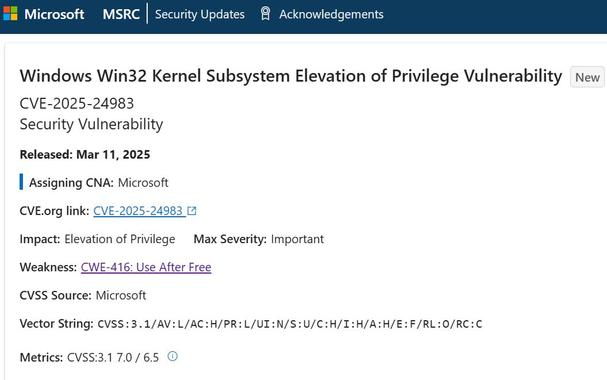
#ESETresearch has discovered a zero day exploit abusing #CVE-2025-24983 vulnerability in the Windows kernel 🪟 to elevate privileges (#LPE). First seen in the wild in March 2023, the exploit was deployed through #PipeMagic backdoor on the compromised machines.
The exploit targets Windows 8.1 and Server 2012 R2. The vulnerability affects OSes released before Windows 10 build 1809, including still supported Windows Server 2016. It does not affect more recent Windows OSes such as Windows 11.
The vulnerability is a use after free in Win32k driver. In a certain scenario achieved using the #WaitForInputIdle API, the #W32PROCESS structure gets dereferenced one more time than it should, causing UAF. To reach the vulnerability, a race condition must be won.
The patches were released today. Microsoft advisory with security update details is available here:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24983