#directorytraversalmemes
Another sev:CRIT ../ ? This time in ZendTo. LMAO. PoC in the post.
We discovered a path traversal vulnerability in ZendTo versions 6.15-7 and prior. This vulnerability allows malicious actors to bypass the security controls of the service to access or modify potentially sensitive information of other users. This issue is patched in 6.15-8, and we encourage all users to upgrade as soon as possible.
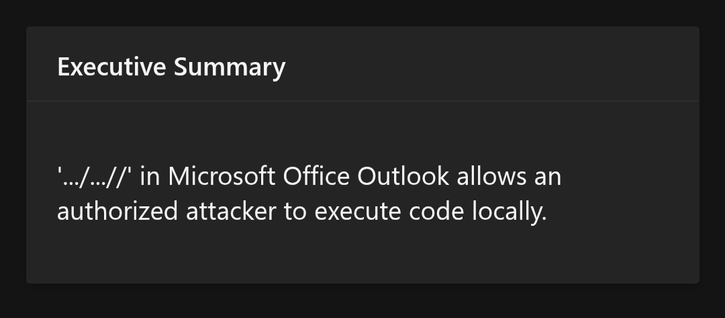
Has #directorytraversalmemes gotten a look at CVE-2025-47176 yet? https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-47176
sev:CRIT ../ in Python ( Kind of, it's CWE-22 but... You can read the details. )
46.46.47.0/24 is a very special network. hilariously it is assigned to .ru
Don't think I've seen one of these. #directorytraversalmemes
464647
Digging through the overnight CVEs like