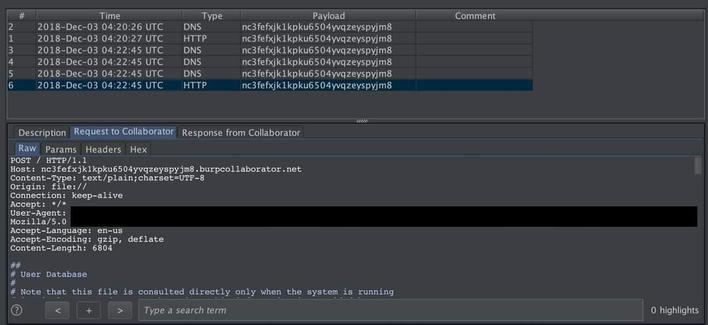
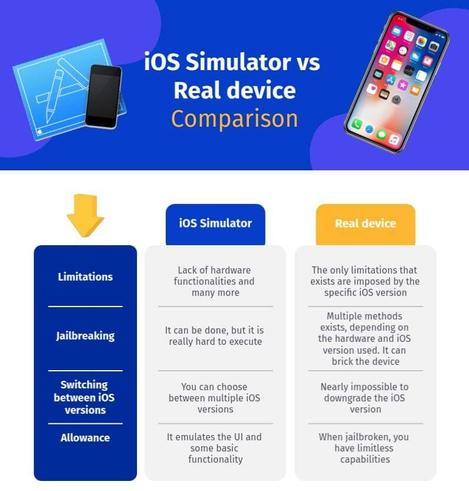
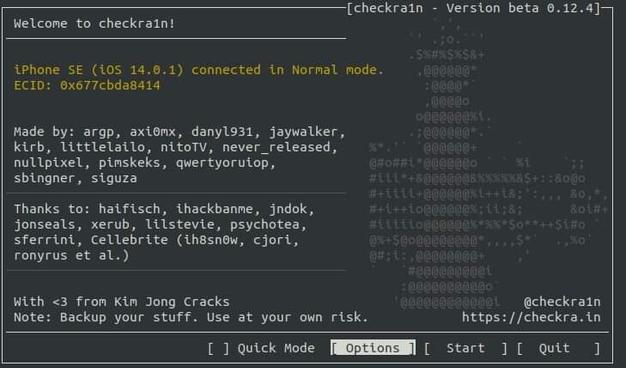
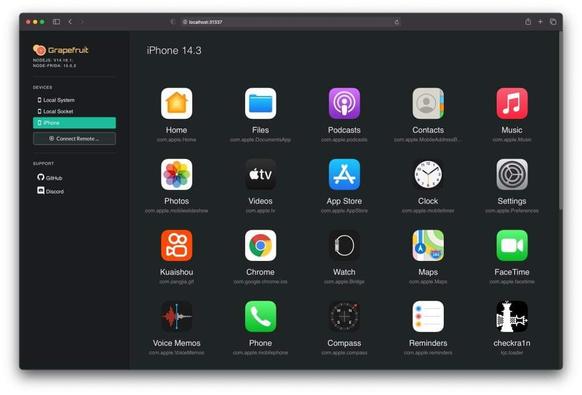
A single iMessage might now compromise your iPhone—no clicks needed. Graphite spyware is targeting journalists worldwide and raising serious questions about our digital safety. Curious to learn more?
https://thedefendopsdiaries.com/graphite-spyware-a-zero-click-threat-to-journalists/
#graphitespyware
#zeroclickexploit
#iossecurity
#cyberthreats
#journalistprotection