https://www.sciencedirect.com/science/article/pii/S2352467725001778
Sustainable Energy, Grids and Networks, Volume 43, September 2025
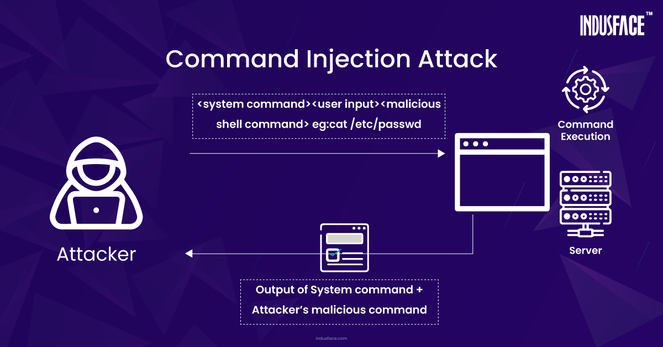
"a systematic #cybersecurity assessment of a #digitalsubstation…A testbed was developed to assess the different attack vectors with a focus on targeting #virtualmachines #resourceexhaustion and #injectionattacks…use case was successfully demonstrated with multiple targeted cyber attacks on the testbed where the non-attacked IED successfully cleared the grid fault."