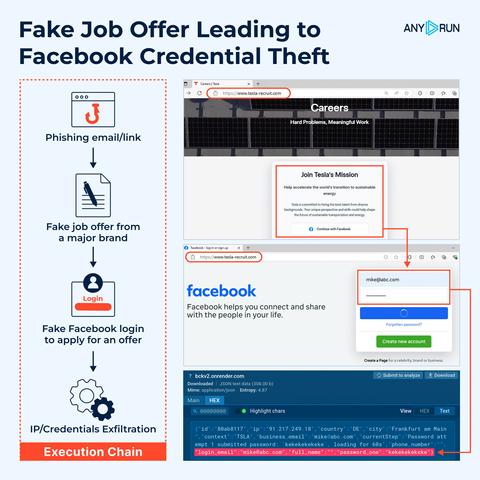
💼 Recruitment-Themed #Phishing Campaigns Target Facebook Users.
🚨 A new wave of phishing attacks is targeting job seekers with fake job offers impersonating brands like Red Bull, Tesla, Meta AI, and others. Attackers use #spearphishing emails to lure victims into applying for fictional positions by logging in via Facebook. These campaigns often spoof legitimate recruitment platforms like indeed[.]com using #typosquatted domains.
👨💻 See analysis sessions:
Porsche: https://app.any.run/tasks/cce7aac5-0cea-400b-aec6-1f436e74dd25/?utm_source=mastodon&utm_medium=post&utm_campaign=phishing_facebook&utm_term=250625&utm_content=linktoservice
Tesla: https://app.any.run/tasks/1ec08aeb-9089-45e4-b649-3acaa2923b77/?utm_source=mastodon&utm_medium=post&utm_campaign=phishing_facebook&utm_term=250625&utm_content=linktoservice
Red Bull: https://app.any.run/tasks/7360ea7f-0496-465a-b9ac-6749aa162d64/?utm_source=mastodon&utm_medium=post&utm_campaign=phishing_facebook&utm_term=250625&utm_content=linktoservice
⚠️ Even though the pages mimic legitimate job platforms, several red flags expose #malicious behavior:
🔹 No redirection to Facebook’s official SSO
🔹 IP fingerprinting via services like ipapi and ipify
🔹 In some cases, exfiltration of credentials using socket[.]io and attacker-controlled Telegram bots
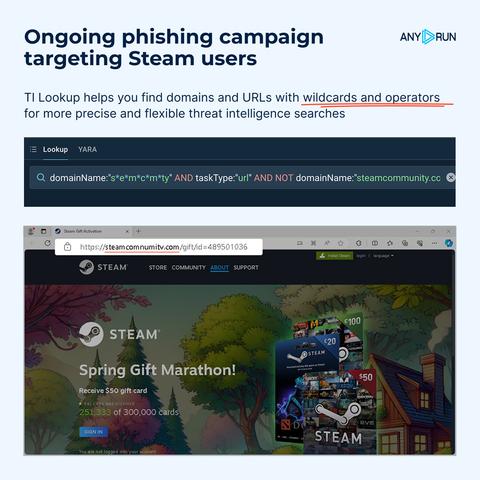
🔍 Search for Red Bull-themed recruitment phishing using TI Lookup:
https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=phishing_facebook&utm_content=linktoti&utm_term=250625#%7B%2522query%2522:%2522domainName:%255C%2522redbull%255C%2522%2520AND%2520(domainName:%255C%2522ipapi%255C%2522%2520OR%2520domainName:%255C%2522ipify%255C%2522)%2520AND%2520domainName:%255C%2522.onrender.com%255C%2522%2522,%2522dateRange%2522:180%7D%20
Another observed trend includes the abuse of indeed[.]com through #typosquatting: lndeed[.]com. See example: https://app.any.run/tasks/fce3c537-de65-4138-bd1f-2dccc16c32c2/?utm_source=mastodon&utm_medium=post&utm_campaign=phishing_facebook&utm_term=250625&utm_content=linktoservice
🔍 Find more typosquatted domains using this TI Lookup request:
https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=phishing_facebook&utm_content=linktoti&utm_term=250625#%7B%2522query%2522:%2522domainName:%255C%2522lndeed%255C%2522%2522,%2522dateRange%2522:180%7D%20
🔗 Execution chain:
Phishing email or link ➡️ Fake job offer ➡️ Fake Facebook login form ➡️ Credentials & IP exfiltration via WebSocket or Telegram bot
🛡️ Recommendation for users and organizations:
🔹 Always enable 2FA
🔹 Cross-check job offers on official company websites
🔹 Avoid disclosing PII unless interacting via verified recruiting platforms like LinkedIn or Indeed
#IOCs:
aimetahire [.] com
aimetajobs [.] com
aimetatalents [.] com
applyjobfast [.] com
jobapplycareer [.] com
redbullrecruit [.] com
redbullrecruitee [.] com
redbulltalents [.] com
tesla-recruit [.] com
lndeed [.] help
applyopenjobsonlndeed [.] space
lndeedresume [.] com
🚀 Use #ANYRUN Interactive Sandbox to analyze suspicious emails and URLs, extract #IOCs, and uncover hidden network activity, such as external IP gathering.