One of my favorite aspects of IT and cyber security is that I'm often treated to those moments of awe and wonder with some of the amazing tech and how people utilize it.
With experience working in information security, including almost two decades of investigations in the fields of cybersecurity and risk assessment, I’ve excelled at triaging, investigating and securing high-tech systems emerging cyber threats.
My training and experience have allowed me to stay on the cutting edge of technology; combating new threats and implementing successful techniques to mitigate and resolve complex cyber matters.
I believe in the importance of team building, the ability to foster a positive working environment and bringing out the best in the people around me. I’m a lifelong learner, with a goal of continuously improving myself and passing knowledge to colleagues and the communities I serve.
@lucasmz @kkarhan @squads I'm in agreement with the use of passkeys over PGP public/private security for simplicity. There is a reason passkeys have progressed more in the last three years than PGP has in 30+ years. Obviously there is a place for all security options; it depends on each person or business's specific risk appetite.
@slashdot If there's money involved there's crime. If everyone froze their credit at the three major credit bureaus it would likely reduce several types of identity fraud. I suggest US residents check out identitytheft.gov for more details on securing your credit. Unfortunately, this means more work for the consumer. As for the higher education facilities it's more time spent vetting students and less time providing a quality education.
@slashdot No one likes thieves!
Stolen iPhones from an Apple Store Remotely Disabled, Started Blaring Alarms https://apple.slashdot.org/story/25/06/14/0549236/stolen-iphones-from-an-apple-store-remotely-disabled-started-blaring-alarms?utm_source=rss1.0mainlinkanon
Dangling DNS entries can lead to reputational damage, data loss, or account compromise. Post-project cleanup is often a low priority for many teams. Unfortunately, failing to remove outdated or unused DNS records can result in significant security risks.
Abandoned DNS subdomains pointing to third-party applications may be discovered and exploited by threat actors. These malicious actors can use them to host phishing sites, counterfeit data upload portals, or various forms of deceptive content — all appearing under your organization's domain name, lending it a false sense of legitimacy.
To mitigate this risk, ensure your decommissioning protocols include the removal of obsolete DNS subdomains as a standard item on your checklist.
We're only human and if checklists are good enough tools for professionals in medicine, aviation, and law enforcement, then they should be good enough for cybersecurity teams as well.
Keep your exposure management skills sharp! Even experienced pros need to refresh and adapt to stay ahead.
Here's a #Free course on Cyber Threat Exposure Management.
Those we sometimes call "dinosaurs" often carry the institutional knowledge critical for navigating and recovering from devastating cyber attacks.
They’ve seen breaches before “cyber” was even a buzzword.
They’ve managed crises without the luxury of today’s tools.
They know what can go wrong — and how to bounce back.
- Tap into their insights.
- Respect their war stories.
- Invite them to mentor the next generation.
Cyber resilience isn't just about the latest tech; it's about wisdom earned over decades.
Let’s treat our experienced professionals as the mentors, stewards, and resources they truly are.
#CyberSecurity #MentorshipMatters #InstitutionalKnowledge #CyberResilience #InfoSec #Leadership #RespectExperience
Insider threats aren't always disgruntled employees. Issues often stem from unintentional actions by employees either not knowing the proper process or not having guidance on sensitive data. Either way,having policies in place can make a world of difference.
@squads I use a password manager because I'm only human and could never remember all of the complex passwords necessary to keep my 100's of accounts secured. Remember, even with complex passwords you should also enable 2FA on all of your accounts, or pass keys, if available.
As an FAA-licensed drone pilot, I perform pre-flight checks, especially after software updates. However, even thorough testing can miss subtle issues, as seen in Amazon's recent drone crashes. Kudos to the FAA and Amazon for grounding flights until the issue was resolved.
https://tech.slashdot.org/story/25/05/18/1957205/why-two-amazon-drones-crashed-at-a-test-facility-in-a-december
#FAA #DroneSafety #Aviation #Tech
@akaetis I agree, logon limitations along with geo-fencing, time of day restrictions and PAM are also important. Getting the end user thinking security plays into the whole security landscape.
This is yet another reminder to utilize a password manager and allow it to generate long, complex passwords. Also, always enable MFA!
According to the FBI's 2024 Internet Crime Complaint Center (IC3) report, ransomware attacks increased by 9% from the previous year, with 3,156 incidents reported. Critical infrastructure sectors—such as healthcare, manufacturing, government facilities, financial services, and information technology—were heavily targeted, accounting for nearly half of all ransomware complaints.
Despite significant international law enforcement efforts, including operations against major ransomware groups like LockBit, ransomware continues to pose a substantial threat. The losses, estimated at $12 million, likely underrepresent the true impact, as many incidents go unreported or lack comprehensive loss data.
Ransomware remains a dynamic and evolving threat. Organizations must stay vigilant and prepared to protect their operations and data.
#CyberSecurity #Ransomware #FBIIC3 #CriticalInfrastructure #CyberResilience #IncidentResponse #StayPrepared
Don't fall victim to a remote access scam. No legitimate business should ever need to access your digital devices (laptops, desktops, tablets, phones, etc.) remotely to refund money or verify account details.
If a scammer does gain access to your device remotely, they can potentially access your email and/or financial accounts, which can lead to unauthorized transfers and loss of money.
If you have been victimized by this scam, I suggest the following:
1. Discontinue use of the digital device and disconnect it from the Internet.
2. Backup your photos and personal items.
3. Reinstall your device to its factory settings.
Alternatively, you may want to seek out a qualified IT professional to service your device.
Lastly, but most importantly, you should immediately update the passwords for all accounts and enable multi-factor authentication to prevent unauthorized access by scammers who may have recorded your passwords during access to your device.
Memory Error - We've all been there before!
@Da_Gut Thank you, we appreciate your support.
@fastfox Vielen Dank, wir wissen ihre unterstützung zu schätzen.
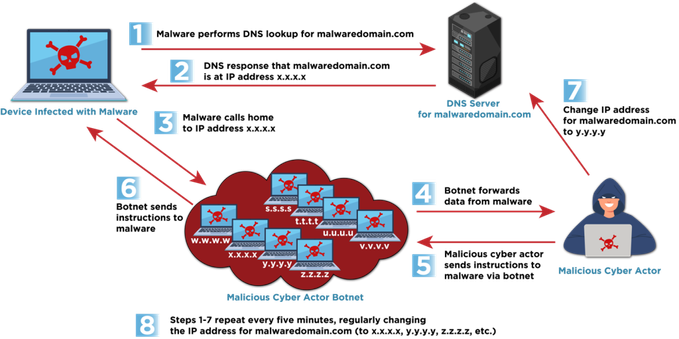
Lately I've been seeing more reporting about the use of fast flux DNS by threat-actors to thwart detection. Let's try explaining how fast flux works, in hopes of identifying its use in the real world.
Fast flux DNS is a technique used by threat-actors to make malicious sites harder to track and take down.The technique achieves this by rapidly changing the IP addresses associated with a specific domain name, sometimes as often every few minutes.
These rapid changes are accomplished by scripting/automation and allow a threat-actor to manipulate traffic to various IP addresses and geo-locations around the globe. This rapid shifting of IP addresses often complicates the process of attribution and the potential of identifying the responsible individual(s).
So how do defenders detect fast flux DNS activities? Well..it's complicated.
Cybersecurity professionals can detect fast flux DNS by analyzing network traffic, DNS logs, and threat intelligence feeds, but if you plan on detecting this in real time you'll need to implement some type of machine learning solution. The speed in which these DNS changes occur, coupled with the volume of network traffic and users accessing online resources makes it unreasonably difficult for someone working in an SOC to detect this technique without the watchful eye of a trained algorithm.
Further complicating the matter, during a cyber incident, defenders are often less interested in attribution and primarily focused on mitigation. The amount of time which passes after an incident could mean hundreds, if not thousands of DNS changes which may not be logged or trackable.
Although fast flux sounds interesting; I don't know how regularly it would be implemented by criminal threat actors.
Security budgets and resources may be better spent on core cyber security principles such as multi-factor authentication, segmentation, encryption and the implementation of zero trust principles and policies.
This post does not cover double fast flux, please see CISA's site for more details.
https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-093a
#fastflux #fast_flux #cyber #cybersecurity #cyberthreats #security