A Practical Guide to PrintNightmare in 2024
https://itm4n.github.io/printnightmare-exploitation/
#infosec
A leading provider of offensive #security solutions & contributor to the #infosec community. #pentesting #appsec #netsec
Change can present a ripe opportunity for attackers – and when it’s broadcast to the world, they take notice. Using the recent string of high-profile X (aka Twitter) breaches, Bishop Fox Red Team Practice Director Trevin Edgeworth discusses what organizations need to consider from a #cybersecurity lens when openly sharing company news like earnings reports and mergers & acquisitions, and even wide-reaching world events.
The prevalence of #AI-generated content signals a tipping point in #socialengineering, requiring us to develop new tools to detect & counter malicious intent. In this recap of a recent Bishop Fox fireside chat featuring Rob Ragan, @alethe, Derek Rush, and Ben Lincoln, we explore the importance of understanding social engineering tactics and strategies, implementing technical controls, and the role of internal network testing.
Ostorlab KEV: a one-command tool to detect most remotely known exploitable vulnerabilities 🐞🔍
SonicWall next-gen firewall (NGFW) series 6 and 7 devices are affected by 2 DoS #vulnerabilities that can lead to remote code execution (RCE): #CVE-2022-22274 and CVE-2023-0656. Bishop Fox research revealed that these issues are fundamentally the same, but exploitable at different HTTP URI paths. Read more & download our test script at our blog.
Bitconned is a scammer’s guide to crypto https://www.theverge.com/24035066/bitconned-ray-trapani-centra-tech?utm_content=buffera35a4&utm_medium=social&utm_source=bufferapp.com&utm_campaign=buffer
Want to learn more about the Bishop Fox #opensource tool Sliver? Then make sure you attend our upcoming #BFLive training session where we’re dedicated the entire time to upping your #pentesting ante with this popular #CobaltStrike alternative.
We asked our Red Team Practice Director Trevin Edgeworth what long-standing unpatched #vulnerabilities can indicate to a Red Teamer. He uses the examples of two vulnerabilities that have gone unpatched for several years: an RCE flaw in Microsoft Office used to deliver spyware and a vulnerability in the popular #GWT framework discovered by Ben Lincoln. https://bfx.social/3RK49YE
Organizations on average experience 700+ social engineering attacks a year.
Dardan Prebreza is your host as we explore #socialengineering stages from planning to execution, common #phishing techniques, and the necessity of ongoing vigilance and proactive strategies to combat this pervasive issue. Don't miss out!
With the new #opensource tool Swagger Jacker, #pentesters can automate analysis of response codes for each #API defined route, streamline manual testing capabilities with #curl command creation, and gather #endpoint routes.
With it being the first week of the New Year and some still away on vacation, it has been slow with ransomware news, attacks, and new information.
Hackers are increasingly targeting verified accounts on X (formerly Twitter) belonging to government and business profiles and marked with 'gold' and 'grey' checkmarks to promote cryptocurrency scams.
Take a look into what sets the Bishop Fox approach to tabletop exercises in #RedTeaming apart. Senior Red Team Consultant @alethe shares how our team focuses on these highly beneficial exercises as building blocks for stronger #security programs versus mandatory compliance tasks. https://bfx.social/3H7Ech2
Ready to take on the role of #CISO? Let us guide you through your first 100 days in this essential role with our talk track "New CISO," filled with expert insights and strategies to set you up for success.
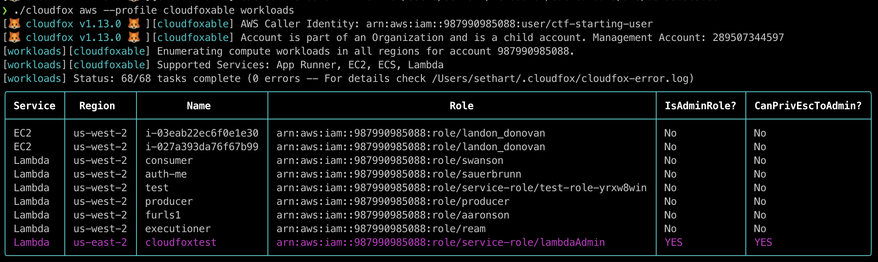
CloudFox v.1.13.0 is out with 2 new AWS commands and a bunch of updates.
* The new workloads command looks at EC2, Lambda, and ECS and highlights any workload that has an admin role attached, as well as any role that can privesc to admin!
* The new api-gws command contributed by Wyatt Dahlenburg finds all API gw endpoints and crafts custom curl commands for you with any API keys found in the endpoint metadata)
* The env-vars command has been upgraded to help you find secrets stored in environment variables. It highlights interesting variable names and creates a separate output file with just the interesting items.
* The role-trusts command has been upgraded to help you find overly permissive role trusts, particularly those that trust :root, without an ExternalID.
Join our Discord server to connect with likeminded #security professionals! We have a few events on the way for 2024.
We'd like to wish everyone a joyous holiday season; thank you for your continued support! Looking forward to what 2024 has in store.
Have you tried our #opensource tool Swagger Jacker? Use this #pentesting tool to easily automate the process of analyzing response codes for each defined #API route. An essential for doing #attacksurfacemanagement, read more in this tutorial. https://bfx.social/47Zubyk
You can also watch Tony West demo Swagger Jacker in this video tutorial recorded in December 2023. https://bfx.social/47ox9Mm
Follow along as Ben Lincoln goes through an unauthenticated #Java deserialization vuln in #opensource web app framework #GWT. This issue has remained unpatched for 8 years; see how to set up an intentionally vulnerable GWP web app for testing.
Have you joined our #infosec Discord server yet? 🤔