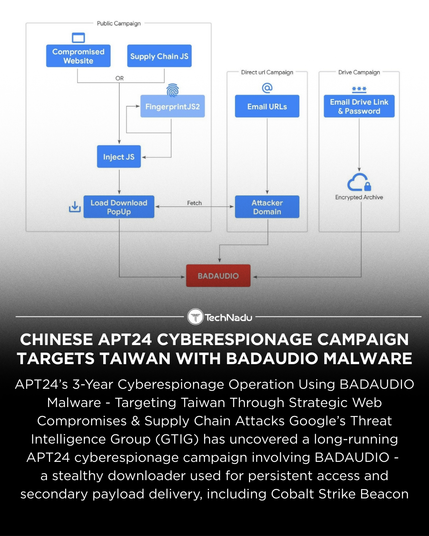
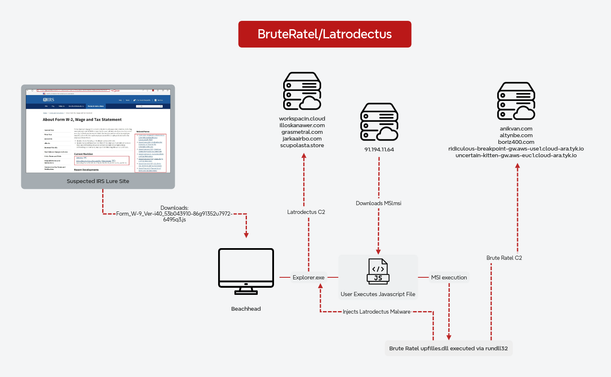
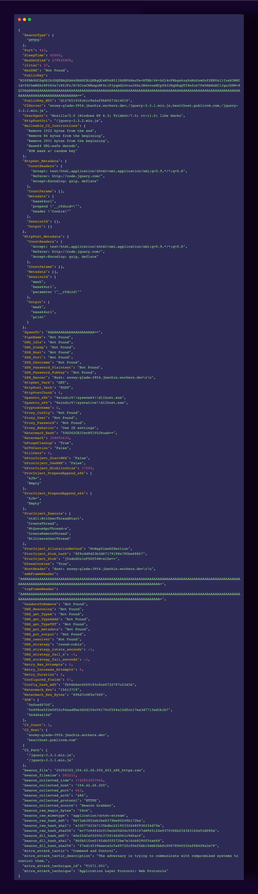
GTIG is tracking a multi-year APT24 cyberespionage campaign leveraging the BADAUDIO downloader.
Notable elements:
• Control-flow flattening + DLL Search Order Hijacking
• Targeted supply chain compromises impacting 1K+ domains
• Cobalt Strike Beacon (shared watermark w/ prior APT24 ops)
• Cloud-hosted phishing + JS injection on legitimate sites
• Strategic web compromise → selective payload delivery
Full report:
https://www.technadu.com/chinese-apt24-cyberespionage-campaign-targets-taiwan-with-badaudio-malware/614191/
Follow @technadu for daily threat intelligence.
#APT24 #BADAUDIO #CyberEspionage #ChinaCyber #GTIG #SupplyChainAttack #Taiwan #CobaltStrike #Malware #ThreatIntel