I cannot stop thinking about how a century of speculative fiction about catastrophic rogue AI meltdown became a self-fulfilling prophecy by building an AI that functions by running a probabilistic lookup on a table of all fiction humans have ever written to determine what the average AI would do in the current situation
Author of open-source projects oletools, olefile, ViperMonkey, ExeFilter, Balbuzard. Posting about #DFIR, #malware analysis, maldocs, file formats and #Python.
https://linktr.ee/decalage
Pwning agentic models with ClickFix.
What a crap turducken we've created here.
https://embracethered.com/blog/posts/2025/ai-clickfix-ttp-claude/
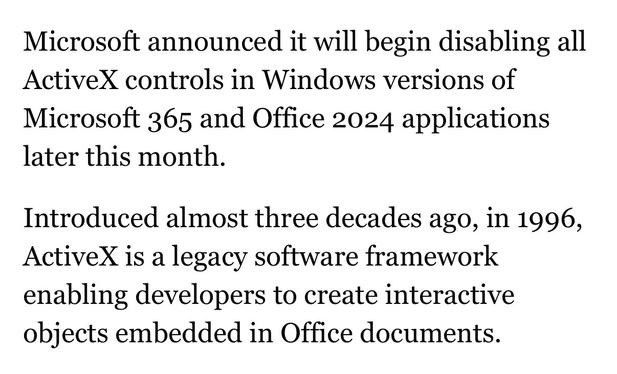
Microsoft blocks ActiveX by default in Microsoft 365, Office 2024
https://www.bleepingcomputer.com/news/microsoft/microsoft-blocks-activex-by-default-in-microsoft-365-office-2024/
About damn time!
“Slopsquatting” in a nutshell:
1. LLM-generated code tries to run code from online software packages. Which is normal but
2. The packages don’t exist. Which would normally cause an error but
3. Nefarious people have made malware under the package names that LLMs make up most often. So
4. Now the LLM code points to malware.
https://www.theregister.com/2025/04/12/ai_code_suggestions_sabotage_supply_chain/
Le programme du SSTIC 2025 est en ligne : https://www.sstic.org/2025/programme/
N'oubliez pas les inscriptions demain vers 13h.
In today's episode of reading through infosec drivel produced by self-serving organizations:
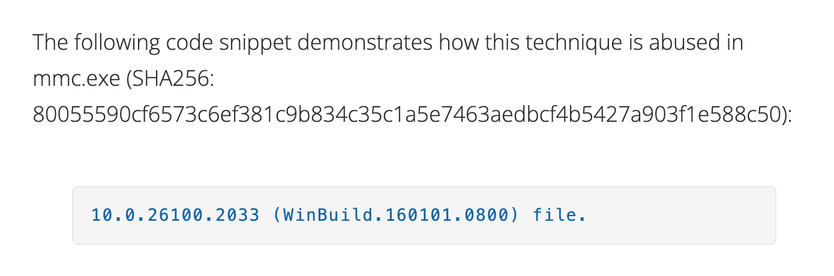
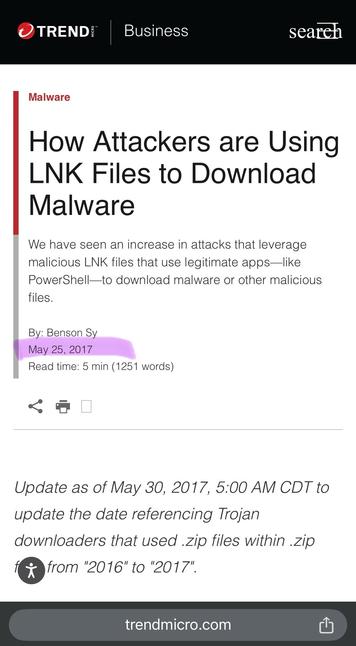
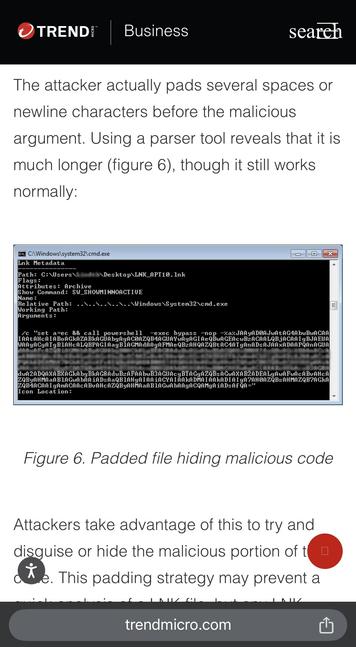
Trend Micro's writeup of CVE-2025-26633 ("MSC EvilTwin").
For starters, rather than giving an IOC of an example exploit, they give the SHA256 of mmc.exe. Thanks?
They also slightly hand-wave over the fact that this ITW exploit starts with executing a PowerShell script. That is, the attack chain begins with the ability of the attacker to execute code on the target system as a prerequisite. Sorry, I'm sort of bored already.
But they've got my attention, so let's dig in a little deeper as to why this is a prerequisite...
Side note:
Trend Micro THEMSELVES mentioned this happening ITW about 8 years ago.
But I guess it was a slow news day, so PR coerced an invented story to suggest their relevance. 🤷♂️
Microsoft released copilot in Excel, and it is officially caught up with Google on the AI race.
Fantastic to watch.
Picard management tip: Don't assume anything is possible or impossible until you've asked the people who will be doing the work.
Do you know examples of polyglot files that have been used in real-life to hide malware from detection/analysis tools?
There is at least this PDF/MHT: https://blogs.jpcert.or.jp/en/2023/08/maldocinpdf.html
Do you know other real malware cases?
Peeps:
I'm looking for a few years old PoC (not mine) which was a graphical game (breakout?) in PDF+JS+WebAsm (not a polyglot), Chrome-only and IIRC, it stopped working on newer versions.
Rings a bell?
The recent PDFTris/Doom/Breakout games are not using Webasm.
🧐 In threat intelligence, you often have to deal with a bunch of different data sources, but these data can come in different forms and need to be processed before they can be analyzed!
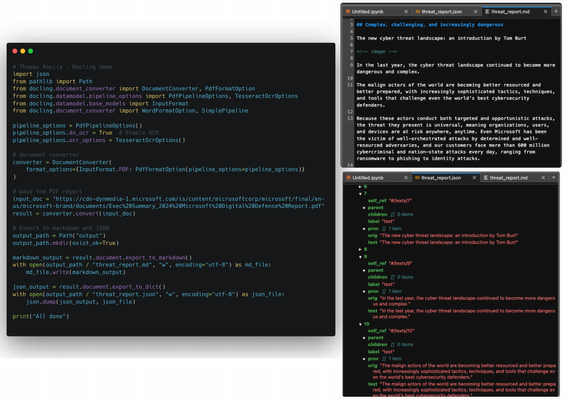
Well, that’s exactly what you can do with Docling, an open-source library that allows you to process different kinds of data (PDF, DOCX, PPTX, XLSX, images, and more). Bonus: you can also use it for chunking your data, for example for a RAG.
One of the easiest ways to use it is as follows, where I pass a PDF report and convert it into JSON and Markdown, and now it is much easier to process further and extract additional details without polluting my pipeline with garbage data from the file structure.
And it supports OCR 🤓
You can find my code below 👇
➡️ https://github.com/DS4SD/docling/tree/main
➡️ Code: https://gist.github.com/fr0gger/251cf87e70313f6d7271a09b30c4c0d5
Make Malware Happy https://isc.sans.edu/diary/31560
My stream about crafting a PDF file from scratch is over.
https://www.youtube.com/live/q6KgFezu8tw?si=Ep9Gm-scYSr1FFcg
It was nice and chill to take the time to answer questions, thanks again for joining!
Smuggling payloads and tools in, using WIM images
https://www.hexacorn.com/blog/2024/12/31/smuggling-payloads-and-tools-in-using-wim-images/
Clean hash set - 12M rows
https://www.hexacorn.com/blog/2024/12/31/clean-hash-set-12m-rows/
🎁 GenAI x Sec Advent #9
Today I want to talk about two things: context in threat intelligence and LLM structured outputs.
What is the relation? Let me explain 🤔
🔍 Threat Intel is all about context—understanding an information and making it usable. Without context, most IOCs are just noise. Context tells us why an IP address is flagged, how a threat actor operates, and what actions to take next.
Threat intel reports are all about providing the context of why a specific indicator is malicious. However, most of the time, you have to dig through the report to understand the context of an IOC and why it is considered malicious.
This is where LLMs and structured outputs come in. 👇
👨💻 Structured Outputs is a feature that allow to keep the model consistently generates responses based on a supplied JSON Schema. This removes concerns about missing required keys or invalid values. We can define a structured JSON schema to extract the exact data we need from a report.
I built a basic example where I extract all kinds of IOCs from a threat report.
The output includes:
- Type of IOC
- Value of IOC
- Context of the IOC
- MITRE ID
- Recommended Action
You can find my code in my gist, along with the execution details below! 👇
➡️ Code: https://gist.github.com/fr0gger/3acd7d8235421c3ca12be2b2d0dfbc26
➡️ OpenAI Structured Output: https://platform.openai.com/docs/guides/structured-outputs
Of course, if you have a structured and consistent output, you can do whatever you want with it. But that is a topic for another day! 😉
#genai #threatIntel #llm #iocs #mitre #infosec #cybersecurity