RIP Claus Peter Schnorr https://mittelhessen-gedenkt.de/traueranzeige/claus-peter-schnorr https://en.m.wikipedia.org/wiki/Schnorr_signature
security & software engineering · operating systems & kernel engineering · cyber defense · civil society
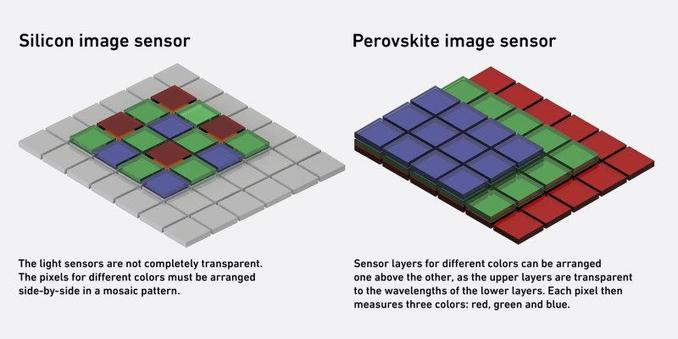
📸 ETH Zürich & Empa researchers have developed an image sensor using stacked perovskite layers, capturing full-color images with higher efficiency and accuracy and without the need for traditional color filters.
Goodbye demosaicing, two-thirds more light in the same surface!
Redox is Hiring!
Check out the job description in our monthly report:
https://www.redox-os.org/news/this-month-250531/#redox-is-hiring
Pixels remain the only devices providing a high level of security combined with proper secure support for using another OS. We hope to have more options by the end of 2026 based on contact with an OEM interested in meeting our requirements but there's no specific timeline.
Looking forward to present some fun NSO exploit archaeology at @recon next week, with Bill Marczak of @citizenlab :
«A Trip to Ancient BABYLON: Unearthing a 2017 Pegasus Persistence Exploit»
From:
Fink Telecom CEO Andreas Fink said: "Our company provides infrastructure and technical services, including signalling and routing capabilities. We do not analyze or interfere with the traffic transmitted by our clients or their downstream partners."
Notice what is conspicuously absent from the list of stuff Fink says they're not doing:
"We do not copy or mirror traffic -- neither all traffic, nor a selected subset of traffic --- for any reason, nor otherwise make traffic available to third parties."
Today we’re publishing a new report on Intellexa’s #Predator #spyware, which is still active despite global sanctions, now with a new client and ties to a Czech entity. Check out the full report here: https://www.recordedfuture.com/research/predator-still-active-new-links-identified
Graphite Caught: First Forensic Confirmation of Paragon’s iOS Mercenary Spyware Finds Journalists Targeted
End spyware use against civil society! Report confirms that Italy’s intelligence services used #Graphite by #Paragon against NGO founder Casarini & Giuseppe Caccia https://www.accessnow.org/press-release/no-normalising-spyware-italy/ #Staatstrojaner
NEW: Cellebrite, maker of phone unlocking tech, to buy mobile testing startup Corellium for $170 million.
We have finished going through the court docs and hearing transcripts from the WhatsApp v. NSO lawsuit.
Here's everything we learned, from how NSO's customers use Pegasus, to the spyware's cost.
New blog post!
How I got a Root Shell on a Credit Card terminal
https://stefan-gloor.ch/yomani-hack
#reverse_engineering #reverseengineering #hardwarehacking #hacking #security
New blog post (about an old exploit): tachy0n.
For iOS 13.0-13.5, dropped as an 0day at the time.
Google quantum researcher Craig Gidney published yesterday a preprint demonstrating that 2048-bit RSA encryption could theoretically be broken by a #quantum computer with 1 million noisy qubits running for one week.
This 20x decrease in estimated required ressources for quantum factoring comes from better algorithms and better error correction.
https://security.googleblog.com/2025/05/tracking-cost-of-quantum-factori.html
The European Council 🇪🇺 has issued sanctions against Stark Industries, a hosting company registered in the UK 🇬🇧, as "they have been acting as enablers of various Russian state-sponsored and affiliated actors to conduct destabilising activities including, information manipulation interference and cyber-attacks against the Union and third countries."
Happy #curl inspired Swisscom to add a "disclose your use of AI" to their bug-bounty program:
https://github.com/swisscom/bugbounty?tab=readme-ov-file#55-reporting-guidelines
I just released a long blog post about using #dtrace on #macOS to debug a thorny bug in the macOS kernel that was breaking #Lix's socket disconnect detection.
It goes through what the fault was, how I found it, where to find information about DTrace on macOS (which is not really well documented), and how the macOS kernel's networking/events system works at a high level. It also explains how one can take an unfamiliar kernel and quickly find relevant code.
Bumped iometa to version 1.7.0.
This update (finally) merges back the `wip` branch with a complete rewrite of the Mach-O parsing layer, which should resolve many issues. Tested against all kernels that I have between 11.0 and 18.5, and it didn't error out on any of them.
Known issues:
- Fails to find IOService vtable on a bunch of kernels between 12.0 and 14.x, which then cascades to all subclasses.
- Doesn't work on visionOS. This is really cursed stuff that will have to wait for multiple inheritance support.