Google has just updated its 2FA Authenticator app and added a much-needed feature: the ability to sync secrets across devices.
TL;DR: Don't turn it on.
The new update allows users to sign in with their Google Account and sync 2FA secrets across their iOS and Android devices.
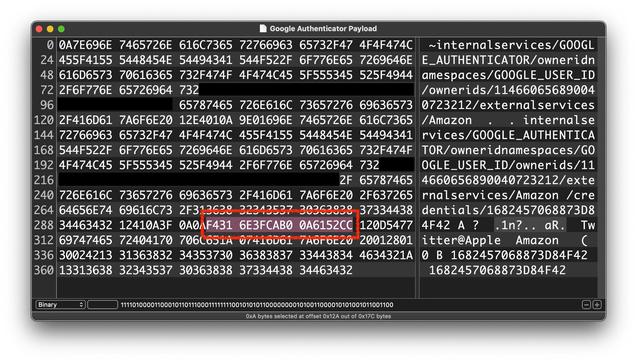
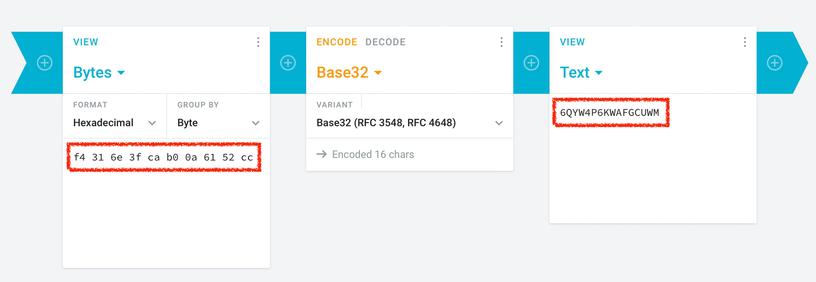
We analyzed the network traffic when the app syncs the secrets, and it turns out the traffic is not end-to-end encrypted. As shown in the screenshots, this means that Google can see the secrets, likely even while they’re stored on their servers. There is no option to add a passphrase to protect the secrets, to make them accessible only by the user.
Why is this bad?
Every 2FA QR code contains a secret, or a seed, that’s used to generate the one-time codes. If someone else knows the secret, they can generate the same one-time codes and defeat 2FA protections. So, if there’s ever a data breach or if someone obtains access .... 🧵
#Privacy #Cybersecurity #InfoSec #2FA #Google #Security