Ich hab mal dieses Plakat für euch fertig gemacht.... @MRMCD #mrmcd25
#hackover #ho25
❄️ NixOS 🤩 (Security, Infra, Python and Release-Manager 22.11/23.05)
Day: Network & Infrastructure.
Night: FOSS, Home Automation
Bei GitHub wird ein Maskottchen für das #Angular-Framework gesucht. In den Kommentaren hatte jemand diesen - vermutlich nicht ganz ernst gemeinten - Vorschlag. 😂
🤡 ↪️ - Spahn ließ sich übrigens 2021 vom Grundbuchamt die Namen von Journalisten geben, die zu seinen umstrittenen Immobiliengeschäften recherchierten.
„Wenn Spahn mit den Informationen des Grundbuchamts Berichterstattung verhindern wollte, habe er gegen die Verfassung verstoßen“. Das sei „viel schlimmer“ als die Verletzung des Datenschutzes, sagte der damalige Bundesvorsitzende des DJV Frank Überall zu dem Fall.
➡️ https://www.tagesspiegel.de/politik/ruffel-fur-grundbuchamt-wegen-mitteilung-an-spahn-4238950.html
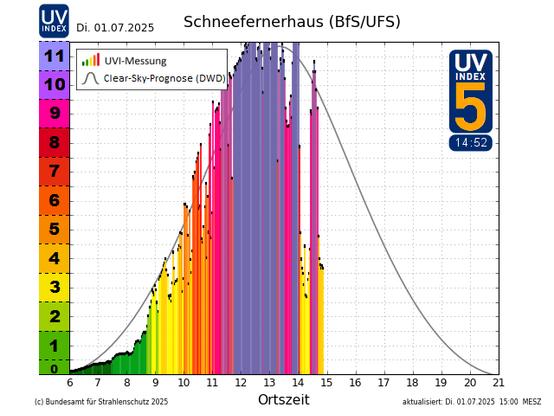
☀️ Der Sommer hat die #UV-Index-Skala gesprengt. 💥
An unserer UV-Messtelle am Schneefernerhaus an der Zugspitze wurde heute ein UV-Index-Wert von 12 gemessen. Normalerweise reicht diese Skala von 0 bis 11 - ein echter Rekord also!
In Nord- und Süddeutschland erreichen die Spitzenwerte aktuell einen UV-Index von 7 bis 9. Die Werte und Tagesverläufe findet ihr immer auf unserer #BfS-Website: https://www.bfs.de/uv-aktuell
It's only #gravy if it comes from the Graveaux region of France. Otherwise it's just sparkling meat bechamel.
🔴 🤡 - Die Union will sich das fehlende Geld für die groß angekündigte und dann gecancelte Stromsteuersenkung für alle jetzt beim Bürgergeld und der Förderung für Wärmepumpen holen. Wie shizegal kann einem der eigene Ruf eigentlich sein?
@fleaz Scheiss Faulenzer. Du machst halt sonst auch Nix.
Go out, touch grass!
@f2k1de Dazu kann ich nichts sagen, dafür musst du den alten Toot raussuchen. 🤡
https://github.com/NixOS/infra/commit/e126083f9004a664972905a7a7892ffb597d9a10 *hust*
@piegames It's nice when they are for once busy amongst themselves.
@cccda or via the wonderful CLI tool https://git.clerie.de/clerie/improv-setup by @clerie
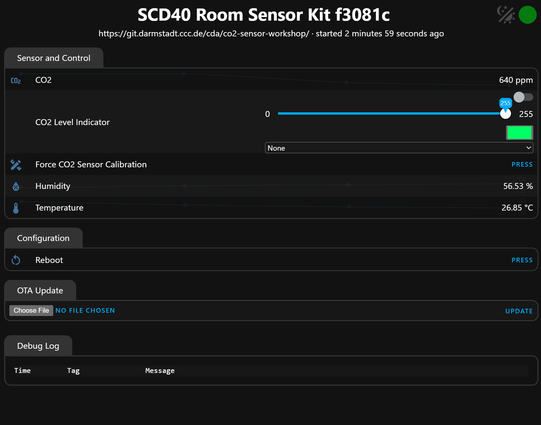
Wir haben ordentlich an der Firmware für unsere CO2 Sensoren gearbeitet und das Setup ist jetzt deutlich einfacher geworden. Ihr müsst die Firmware nicht mehr selber konfigurieren und kompilieren, sondern könnt einfach die fertigen Dateien aus unserer Pipeline nehmen und danach eure WLAN Zugangsdaten mittels "Improv Wi-Fi" über Bluetooth oder den Browser konfigurieren.
Meldet euch bei Fragen gerne bei uns oder kommt Di/Fr vorbei :)
https://git.darmstadt.ccc.de/workshops/scd4x-esphome-workshop
Das komplizierteste daran pretix und pretalx zu nutzen, ist dass man sich merken muss wer von beiden /orga/und wer /control/ benutzt 🙃
@snarkweek I think we're not alone in this and still have a long way to go.
@undltd No, that one is builtin, given that the Kernel provides the interfaces to set it up.
@DerMario Hab diesen Feed hier
https://feeds.simplecast.com/Y_bRXaw2
Aber höre den dann doch eher unterwegs mittels Antennapod, das tut einfach.
@DerMario Das erinnert mich an "Alles gesagt?" von der Zeit 💢
Selbst der RSS-Feed linkt für die einzelnen Folgen auf die Hauptseite.
For #NixOS Unstable users:
We're about to stop shipping VPN plugins by default with #networkmanager.
This means you'll need to explicitly configure the ones you need via `networking.networkmanager.plugins`.
In fact, if you are relying on a VPN via #NetworkManager go and do that now to prevent any interruptions.
See this post for further details:
https://discourse.nixos.org/t/breaking-changes-announcement-for-unstable/17574/85?u=hexa
Danke, dass ihr mich bei euren Datingkonzepten bedenkt.
Als Teil des Vorstands möchte ich hiermit verlautbaren, dass wir uns am ehesten für die Reihe mit den Klimazonen der Erde begeistern können.
https://www.bundesbank.de/de/aufgaben/bargeld/euro-muenzen/sammlermuenzen/5-euro-821344
Das garantiert euch dann auch die Gunst von mir als Gastgeber.