@split if google translate isn't blocked, you can use its 'translate website' thing as a free HTTP proxy to get around blocks like these
i do stuff 🏳️⚧️🏳️🌈
pronounced /ɭɛɳa/, not /ɭiɳa/
rust evangelist and train enjoyer 🚆🚂
fuck cars
antifa militant
owner of a twinkpad
this is my tech/serious/whatever account, for more personal/shitpostig/flirty/lewd stuff see @lena
@cadey lmfao they don't even attack it on the basis of accessibility and open web, but for 'autonomy' and 'control over their own computing'.
have they ever visited a website made in the past 20 years???
"Whatever" is a brilliant essay on "AI" by @eevee:
"But I think the core of what pisses me off is that selling this magic machine requires selling the idea that doing things is worthless. Because if doing something has some value, then it must be somehow better than pushing a button and receiving Whatever for essentially no cost."
@GrapheneOS @newhinton the 'security issue' they mention is very funny because an app shouldn't be able to ask for permissions that F-Droid doesn't know about.
they're supposed to have automated checks and scans for each update, there is literally NO WAY for that to ever happen
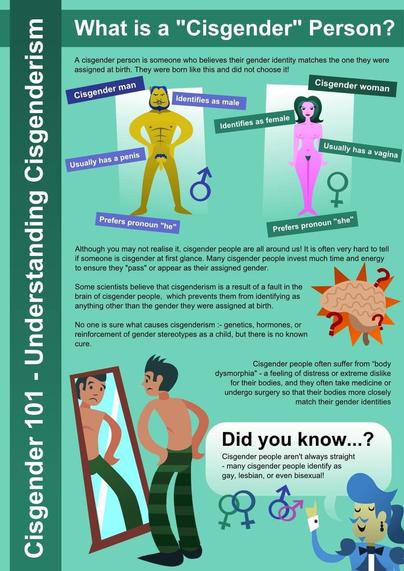
Cisgender 101!
This one has been going around for a long time from what I understand, but it's still super relevant. 😁
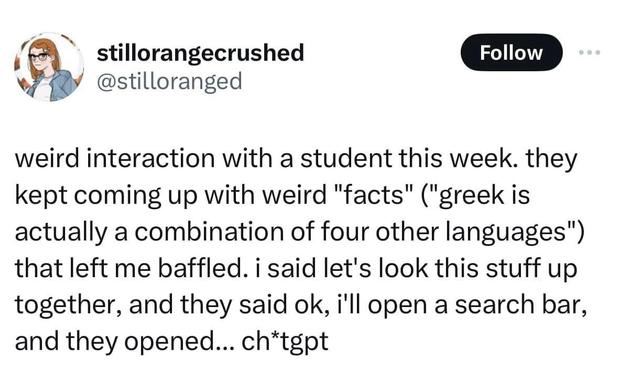
People are shocked to discover they need to fact-check ChatGPT and I'm having the uncomfortable realization that they never fact-checked their uncle's Facebook posts, their friend's medical advice, or literally anything Google's top result told them, and suddenly the last decade makes sense...
@bagder "create issues with copilot" is such a beautiful description for it because it is so unintentionally true. all it does is create issues LMAO
@a1ba sudo processed the --chroot option before actually reading sudoers, so you can make it load a custom binary https://openwall.com/lists/oss-security/2025/06/30/3
@mildsunrise @a1ba lmfao
When people say “don’t replace your staff with AI” they don’t want to hear “don’t worry, we are only replacing CONTRACTORS with AI, not full-time staff.” You just made everyone in the room roll their eyes so hard.
Obviously what people want is not poorly done work. They want work done by actual humans. Don’t try to turn this into another capitalist shell game. Fuck off with this shit
Nonmention:
If you are victim to a ransomware attack and your data gets leaked on the darknet, you shouldn't write a press release that this happened "despite your high security standards", when everyone can see your standards in your password file PW.docx.
LLMs are responsible for a lot of sins but let us not forget the harm it has caused the em-dash enthusiast community, of whom i consider myself a fellow
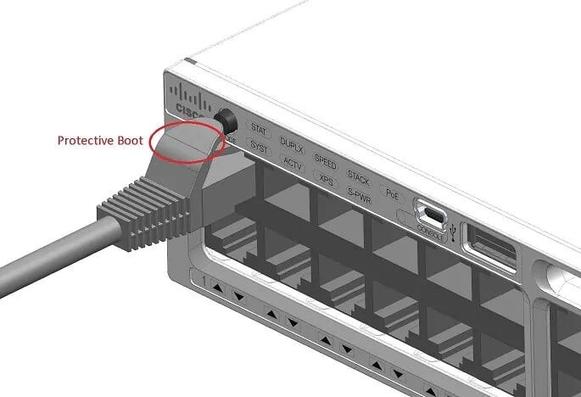
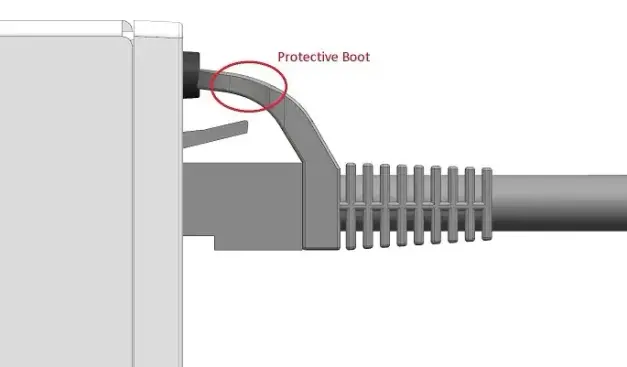
if you've ever messed up a dimension or a hole position on something you're building, don't be too hard on yourself.
at least you're not the Cisco design engineer who caused an entire product line recall by placing the mode button (which resets the switch if held) directly above an RJ45 port.
If FOSS isn't woke, why is it called copy_left_ and not copy_right_?
People keep telling me I don’t know how good I have it. That modern systems are easy, and that accessibility has come so far I should be grateful. So I decided to test that claim the hard way.
I’m running Windows XP for a month. Not in a VM. Not themed. Real XP. Real hardware. A 2009 Samsung NC10, with 2GB of RAM, an SSD, and the original drivers I had to dig up from the depths of the internet.
No speech at install. I used OCR to get through it.
Display drivers broke four times.
Serpent is the only browser I could get working.
I installed Office 2003.
Got JAWS 15 running after a registry hack.
NVDA still works fine.
I even played some old audio games I never got to try growing up.
I haven’t found a decent ad blocker or antivirus yet. I’m not expecting this to go smoothly. I don’t even really believe I’ll make it the full 30 days. But I’m doing it anyway.
Day 1 is up. Written and published from Windows XP.
https://fireborn.mataroa.blog/blog/dead-os-walking-30-days-on-windows-xp-in-2025/
#WindowsXP #Accessibility #BlindComputing #RetroTech
#NVDA #JAWS #audiogames
#30DaysOfXP
what they say: no politics in foss
what they mean: I'm a little pee pee baby with no idea what labor means or where foss came from or under what socio-economic conditions technology gets (re-)produced and deployed; please change my diapy, i did a little wee wee because it upsets me when people aren't talking exclusively about 1s and 0s in the platonic realm of pure computing
the "no politics in foss" ideology (and it is an ideology to say "no politics in foss" and therefore the statement is itself political!!) is a remarkable example of how capitalism is able to co-opt even explicitly political movements into itself and turn them into something that serves its own interests; in this case, foss as a political movement against closed-source, for-profit, proprietary software is turned into nothing more than a stockpile of free labor for shitbag capitalist vultures to get their claws into; and god forbid you should dare to speak up for yourself or to point out that this state of affairs only serves fashy capitalist wankers
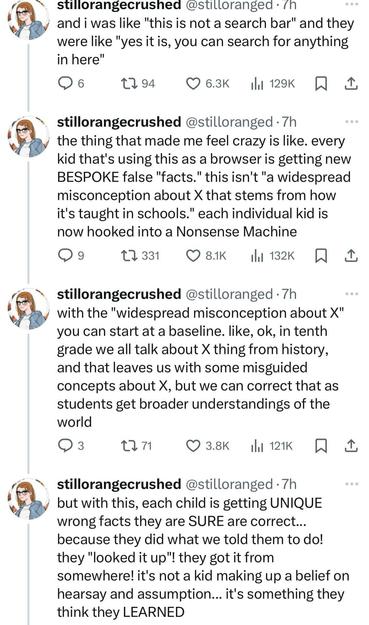
"each individual kid is now hooked into a Nonsense Machine"
Edit: I got those screenshots from imgur. It might be from Xitter, with the account deleted or maybe threads with the account not visible without login? 🤷
2nd Edit: @edgeofeurope found this https://threadreaderapp.com/thread/1809325125159825649.html
#school #AI #KI #meme #misinformation #desinformation