Black Lives Matter
Dreamer | Speaker | Legend | SRE | MCT | Shadow Architect
He/him/his/Skills
VB better than PowerShell
Have we met?
My ideal role would be primarily technical, aimed to dissect software to uncover vulnerabilities. Beyond bug mining I'd love to learn to mine better and make new kinds of pickaxes.
My public works and contact info are on my homepage:
https://scrapco.de
Get in touch if you want to know more!
Boosts are appreciated! #FediHire
Long before the internet, some phone networks were hackable by playing a single tone at 2600Hz.
Whistled into a phone, it could grant you unrestricted access. Do you have the vocal chops to be an old-school phone phreak?
I built a web app to test your ability to produce the legendary frequency. You won't get free long distance calls but you will get some honor in the knowledge that you could have been a cool hacker. 😎
I am sad to say that I can only whistle up to 1100Hz... But my wife (a long time woodwind player) is able to consistently get it.
Give it a try: https://phreak.kmcd.dev/
#phreaking #2600Hz #bluebox #RetroComputing #hacker #infosec #Tech
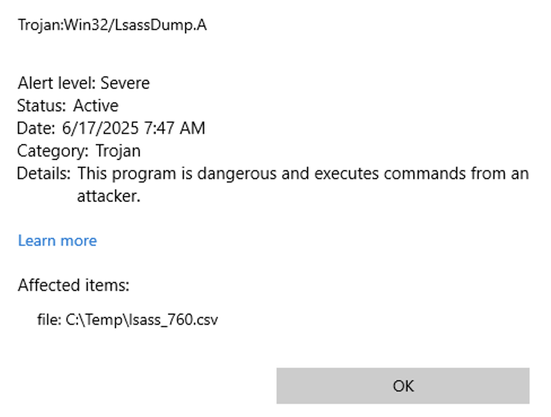
I successfully tested a LSASS dumping technique on a Windows 10 lab machine, which we encountered on a recent Incident Response engagement (no EDR, default Defender installed).
The "MiniDumpWriteDump" technique, as described here [1], was successful in writing the LSASS process to disk.
However, as soon as I tried to copy the dump to my Kali machine, Defender jumped into action, prohibited access to the LSASS dump, and removed the file to the quarantine. And here is the catch.
I browsed to the following folder:
C:\ProgramData\Microsoft\Windows Defender\Quarantine
In the ResourceData folder, you will find different sub-folders (or not, if Defender never quarantined something on that host), each folder containing a quarantine file.
The files are encrypted with a static key that leaked years ago, and this 10-year-old code snippet is still sufficient to decrypt the files back to their original state. [2]
Long story short: I copied the encrypted file to my Kali machine, decrypted it using the Python code from [2], and extracted the credentials and hashes with pypykatz. [3]
Classic example of "No, it's not enough when your AV blocked or removed a threat". As you can see, an attacker can easily get the LSASS dump, even if Defender removed it from the disk ¯\_(ツ)_/¯
[1 ]https://www.ired.team/offensive-security/credential-access-and-credential-dumping/dumping-lsass-passwords-without-mimikatz-minidumpwritedump-av-signature-bypass
[2] https://raw.githubusercontent.com/malmoeb/DFIR/refs/heads/master/quarantine.py
[3] https://github.com/skelsec/pypykatz
At just 3 years old, I have a penthouse suite, 2 passive incomes, a personal chef and driver. Follow me for financial advice.
"Works on my machine", oil on canvas.
Unknown artist, 2025
@psconf.eu you can always just run the other way
Hold up... those things come in orange?
Incidentally, if you’re not paying attention to the EU’s Cyber Resillience Act, it seems to require publishing threat models (as of the effective dates). Specifically, Article 13 states:
“3. The cybersecurity risk assessment shall be documented and updated as appropriate during a support period to be determined in accordance with paragraph 8 of this Article. That cybersecurity risk assessment shall comprise at least an analysis of cybersecurity risks based on the intended purpose and reasonably foreseeable use, as well as the conditions of use, of the product with digital elements, such as the operational environment or the assets to be protected, taking into account the length of time the product is expected to be in use. The cybersecurity risk assessment shall indicate whether and, if so in what manner, the security requirements set out in Part I, point (2), of Annex I are applicable to the relevant product with digital elements and how those requirements are implemented as informed by the cybersecurity risk assessment...
4. When placing a product with digital elements on the market, the manufacturer shall include the cybersecurity risk assessment referred to in paragraph 3 of this Article in the technical documentation required pursuant to Article 31 and Annex VII.”
Futher, Annex 7, Part 2(a) specifies that:
“The technical documentation referred to in Article 31 shall contain at least the following information, as applicable to the relevant product with digital elements: ... 2. a description of the design... including: necessary information on the design and development of the product with digital elements, including, where applicable, drawings and schemes and a description of the system architecture explaining how software components build on or feed into each other and integrate into the overall processing...”
(4/5)
Scottish Police Authority.
May 2024.
FOI-Request
@powers-hell.com will be on stage for #PSConfEU 2025 in #Malmö (23-26 June)! 🎙️Argument completers, Dynamic parameters, and more: Building better PowerShell functions 🎙️Authentication unpacked: What does MSAL actually do? 🎟️ Tickets at psconf.eu #PowerShell #Svenska
It seems selling Microsoft software licenses in Hungary is very attractive for criminals...
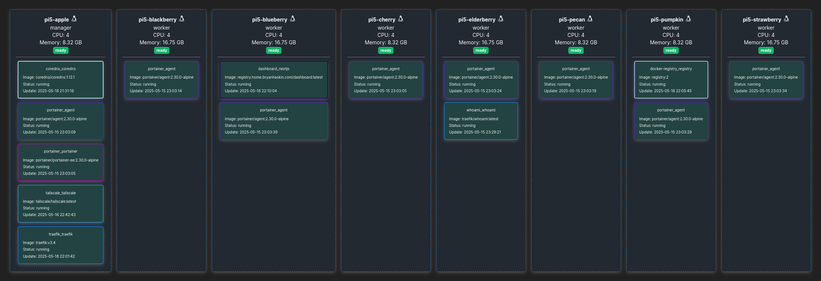
Here is my new #minirack !
DeskPi RackMate T1, 2x GeeekPi 10 Inch 2U Rack Mount for Raspberry, MikroTik CSS610-8G-2S+in Network Switch, and DeskPi 7.84-inch Touch Screen.
4xpi5-8gb and 4xpi5 -6gb, 8 total nodes. There is also an additional pi4 running the display.
Running docker swarm with Portainer.
So far my stacks are: CoreDNS, traefik, tailscale, docker-registry, and nextjs dashboard for the display.
Once you flatten knowledge into prediction, once you replace the actual road of learning with a shortcut that feels smarter than you are, you’ve done more harm than you know.
15/16
Unpatched holes could allow takeover of GitLab accounts https://www.csoonline.com/article/4006160/unpatched-holes-could-allow-takeover-of-gitlab-accounts.html
To understand the future of identity, you have to know its past.
I had an incredible conversation with Microsoft's "Yoda of Entra" Tarek Dawoud, about the entire 20+ year history of Microsoft's Identity platform.