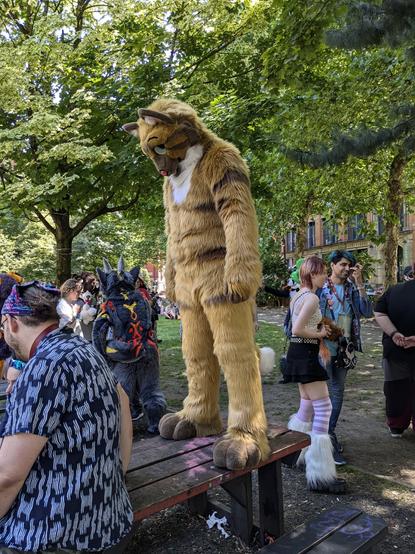I almost melted from the heat but I had fun at the #MancFurs #furmeet
He/him. Gay/demi dhole (Cuon Alpinus) furry.
Blogger, programmer, security engineer, cryptography nerd. 30+
Too spicy for Twitter (banned with all the prominent journalists on 2022-12-16)
I don't represent any company, individual, or community.
In the name of the Yass, the Queen, and the Holy Bean. Slay Men. 🙏
#Furry #Furries #Fursuit #FursuitFriday #Photography #Anthro #FurryArt #FurryArtist #FWA #FWA25 #ArtShare #Art
So Bluesky is about to require people to verify their age, which means sharing their real identity. I’ve no problem with people knowing my identity but then I’m not trying to hide from abusers. Or explore my gender. Or be a whistleblower. Or protest without getting arrested. Or or or… there are so many reasons people need anonymity.
Despite being myself online I am not keen to show Bluesky my scanned face or my bank card. So I guess I won’t be sticking around there.
I gave my advice before I left, which was “Switch to Mastodon, nobody there cares who you are, as long as you’re funny.”
@rootwyrm I suspect people are asking so I'll shit on it
@soatok also, it being Jerk Dorsey tells you everything you need to know:
- has no original ideas
- quarter-assed if somebody else worked on it
- invites Nazis and terrorists
tbh, I wish "bored billionaire builds bullshit barn" weren't news fit to print.
@jkmcnk It's called bitchat
still can't believe they called a company "post hog"
Keep ‘em coming!
Via Kyle Cheney:
#BREAKING: Judge rules that during its large-scale enforcement operation in LA, DHS/ICE has been arresting people without probable cause -- based on factors like accent and line of work.
She orders the agencies to stop.
https://storage.courtlistener.com/recap/gov.uscourts.cacd.975351/gov.uscourts.cacd.975351.87.0.pdf
I've been asked a few times and so:
Yeah, I heard about Jack Dorsey rolling his own crypto.
No, I don't have anything interesting to say about it.
Will I look at it in the future? Unlikely. I'm kind of busy these days.
@soatok gfdi soatok
Using Python for mathematics is actually part of a long tradition.
It began with Adder.
Orange gang! 🧡
🐲 Flow
📷 Kydos & me
#FursuitFriday #furry #fursuit #FursuitPhoto #FoxFurry #FoxFursuit #DragonFurry #DragonFursuit #CuteFursuit #OutdoorFursuiting #s2meets #AustralianFurry
I cannot overemphasize to you how often law firms are targeted by hackers, sometimes employed by opposing parties in cases they are working on, and how profoundly unprepared most law firms are to defend themselves.
https://www.cnn.com/2025/07/11/politics/chinese-hackers-suspected-law-firm-hack
dancers on fedi! How does this one learn to dance? It has a particular focus on hard dance/jumpstyle/shuffle vibes and dancing at raves but any advice on basics for (especially freestyle) dancing less awkwardly are appreciated!!
It has a good sense of rhythm already from playing music and playing dance games, but really struggles to dance outside of the context of playing SMX or pump.
:boost_ok:
VR avatar commission for @k0w0m4n, featuring his charr Koman Dragonrage!
Thank you so much for the commission, and I hope you’ll have a great time with him in VR soon!