#VibeCoding your MFA
Futurist. Mentor. Microservice advocate. Security SaaS - CTO Authress. Philosopher. Critic. Climate activist. Will tear apart anything not done correctly.
@mattl I own aws-login.cloud. And as soon as I have a good opportunity it will finally fix the most important missing part of AWS identity.
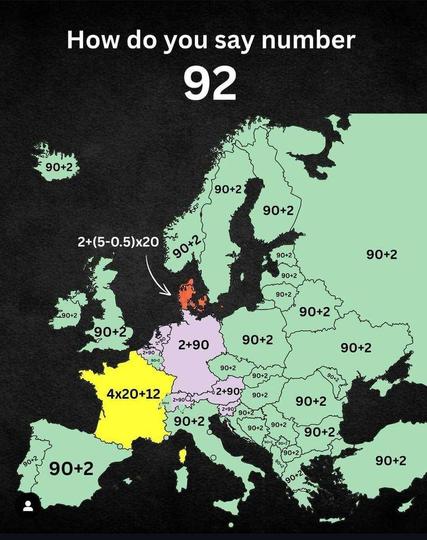
How To Say The Number 92 In Various European Languages
Nice analysis: https://brilliantmaps.com/number-92/
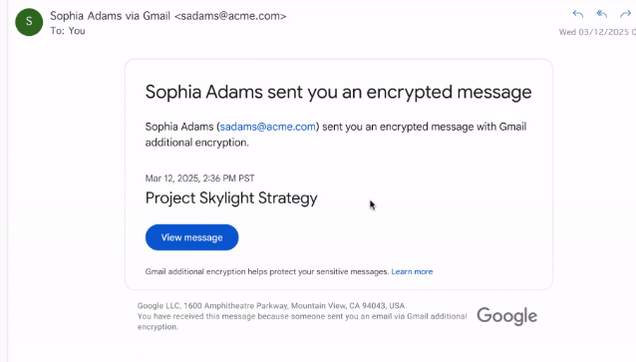
@mttaggart This is absolutely horrifying.
My first thought with this approach is that it's a phisher's dream come true.
Take a look at how non-GMail users will receive encrypted mail. These sorts of messages, especially with an expected auth flow, will be spoofed instantly.
The internet of things is truly a wonder. 😝
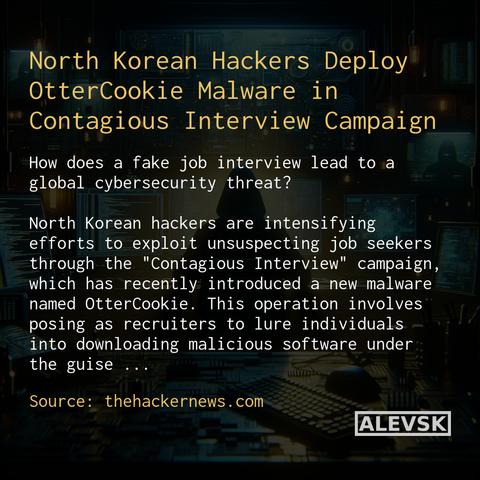
How does a fake job interview lead to a global cybersecurity threat? 🕵️♂️💻
North Korean hackers are intensifying efforts to exploit unsuspecting job seekers through the "Contagious Interview" campaign, which has recently introduced a new malware named OtterCookie. This operation involves posing as recruiters to lure individuals into downloading malicious software under the guise of a job interview process.
One key method is distributing malware-laden videoconferencing apps or npm packages hosted on platforms like GitHub or official registries. These tools pave the way for deploying other malware like BeaverTail and InvisibleFerret. Notably, BeaverTail now uses Python scripts, collectively referred to as CivetQ, to enhance its modular approach for stealing sensitive information.
OtterCookie, first detected in September 2024, is a JavaScript-based malware that communicates with command-and-control (C2) servers using the Socket.IO library. Once activated, it can execute shell commands to steal files, clipboard content, and, more critically, cryptocurrency wallet keys. A newer version, spotted just last month, builds upon its predecessor by tweaking how it steals crypto wallet keys—integrating this directly into its code rather than relying on remote commands.
The attackers' persistence in updating their tools while keeping their infection strategy intact underscores the effectiveness of their operations. These activities share similarities with other North Korean campaigns but stand distinct from larger efforts like "Operation Dream Job."
Beyond malware advancements, this campaign ties into broader illicit schemes. Recent sanctions by South Korea’s Ministry of Foreign Affairs highlight how North Korea sends IT workers abroad to secure funds for its nuclear and missile programs. Sanctioned entities like the 313th General Bureau exemplify how these cyber operations stretch globally, undermining international security by funneling stolen resources into military projects.
#Infosec #Cybersecurity #Software #Technology #News #CTF #Cybersecuritycareer #hacking #redteam #blueteam #purpleteam #tips #opensource #cloudsecurity
— ✨
🔐 P.S. Found this helpful? Tap Follow for more cybersecurity tips and insights! I share weekly content for professionals and people who want to get into cyber. Happy hacking 💻🏴☠️
in switzerland you aren't allowed to have a train with exactly 256 axles because of an integer overflow in the axle counting machine
i wish i could fix my software bugs by making it illegal to cause them
It's official a can of Guinness no longer fills up a Guinness glass.
I'm so disgusted by the fact people can be so hyped something and at the same time can't TL;DR it. I will buy you an expensive dinner in Switzerland the next time you are here if you can explain to a junior engineer what problem System Initiative solves.
How is it legal for companies like Apollo.io to steal and sell my data in EU, and force me to use their broken UI to request an opt out.
The opt out form doesn't even work. I hope the regulators come for them.
@b0rk cron
Today's Security Offender: @Vimeo
How can you be asking me to create a password in 2024. I already have a fully secured account, and you want me to make it less secure....
@calamari That for sure is great, it's actually something Dorota brought up in her talk this year https://devopsdays.org/events/2024-zurich/program/dorota-parad/
Google released a new login page today, it's probably what affected SSO accidentally for tons of businesses. But it seems like there was a small mistake, so I've fixed it here
Just why?
Biggest lie in technology today is that monoliths can work.
If you’ve got anything that remotely looks like a two-pizza team, then through Conway’s Law, you’ve already decided that the only right answer is microservices.
It’s not possible on one hand to have autonomous teams and on the other attempt to have a monolith. It’s an approach that is always doomed to failure.
@bagder Mine had similar problems, so I ended up learning kdenlive yesterday to get it resolved. I don't mind having this new skill, and I think it turned out well despite my amateur video editing skills. (The original had the slides off by whole 6 seconds 😅)
My #FOSDEM talk recording from this weekend is now available. Learn all about the common API threats and solutions to them: https://youtu.be/xLjxbX0hbPo