We released new Pwndbg: https://github.com/pwndbg/pwndbg/releases/tag/2025.05.30 !
Among others it brings:
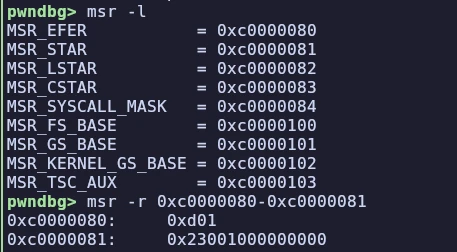
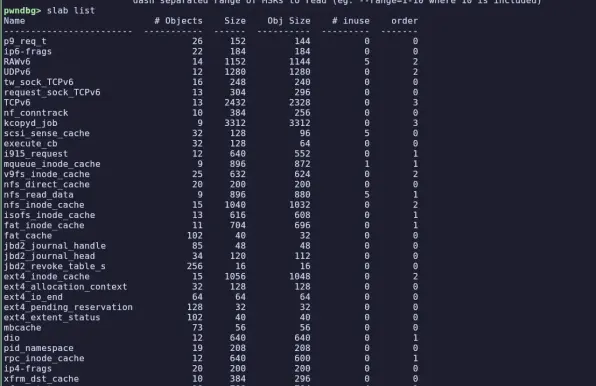
- New & improved kernel debugging commands (buddydump, msr, slab) and more x64 regs in context
- New command for dealing with armcm exceptions: dump-register-frame
- Disasm now shows an ✘ marker for emulated branches we know won't be taken
- Improved disasm for ARM, MIPS and LoongArch64 architectures
- Initial support for the IBM s390x architecture
- IDA sync integration fixes
And also cool portable one-liner installers:
$ curl -qsL 'https://install.pwndbg.re' | sh -s -- -t pwndbg-gdb
$ curl -qsL 'https://install.pwndbg.re' | sh -s -- -t pwndbg-lldb
Want to support us? Sponsor us at https://github.com/sponsors/pwndbg !