Exploit details for max severity #Cisco #IOSXE flaw now public
#IOSXE
🚨 Cisco issues emergency alert: A critical vulnerability (CVSS 10.0) in IOS XE Wireless Controller risks root access. Learn mitigation steps now.
#SecurityLand #CyberWatch #SecurityVulnerability #CVE #IOSXE #Cisco #WirelessController
⚠️ Kritisk sårbarhet i Cisco IOS XE Wireless Controller – godtycklig filuppladdning möjlig. CVSS-score på 10 av 10 möjliga!
#Cisco #IOSXE #CiscoWLC #CVSS10 #CVE202520188 #Sårbarhet #Informationssäkerhet #ITsäkerhet #RootAccess #RCE #JWT #HardCodedCredentials #PathTraversal #WirelessLAN #Catalyst9800 #Nätverkssäkerhet #Sårbarhetsanalys #Exploit #Cybersecurity #SecurityAdvisory
🚨 #Cisco #IOSXE #CVE-2023-20198 #CVE-2023-20273
It's been a while, exploit activity has decreased || mostly consists of Auth Bypass + simple recon.
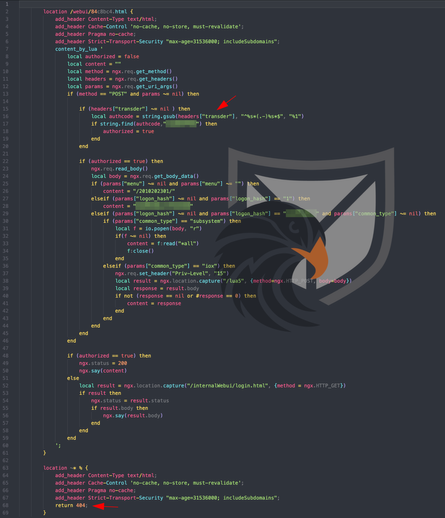
However, we recently found a new version of the Implant 👀 No clear #attribution for now, original TA or copycat? #IoC ⬇️
Since the MO and Implant code of the original TA are widely known by now we can't tie it to them confidently.
What stands out in this case:
1. new path (84c8bc4.html) + 404 return
2. separation of the Implant delivery and C2 infra:
138.122.193[.]157📥
134.122.75[.]64📣
The commands issued during the Implant delivery stayed the same for the most part, although now the attacker calculated SHA-1 hashsums of dropped files to read back and verify their integrity.
/var/www/f099.css
/tmp/pvp_coco
/tmp/pvp_wd_run
Did anyone spot similar activity? We'd love to hear from you!
Thanks for reading today's thread 🍪
🚨 #Cisco #IOSXE #CVE-2023-20198 #CVE-2023-20273
We updated our #IoC for exploit attempts that hit our honeypot. You can find them on #GitHub: https://github.com/SIFalcon/research/blob/main/CVE-2023-20198/ioc.txt
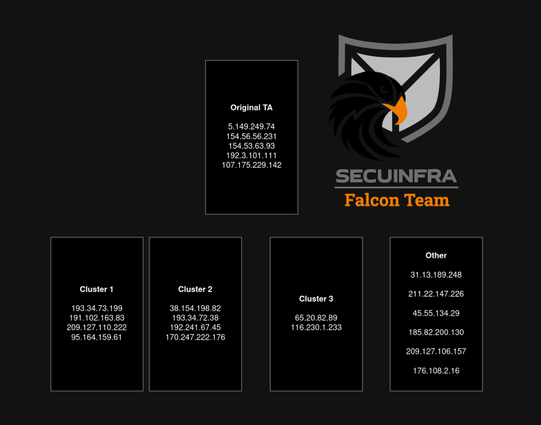
Based on modus operandi and infrastructure we managed to cluster certain attacking hosts togehter ⬇️
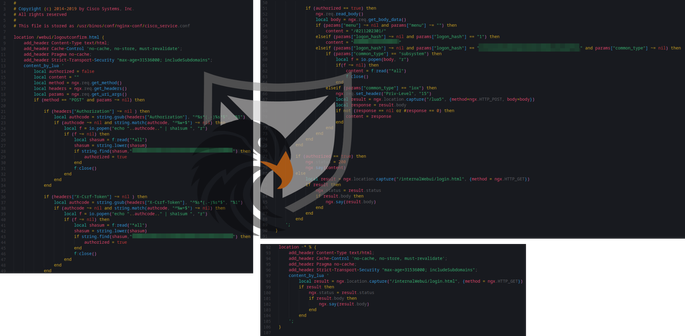
We also saw new traffic to the Implant, this time from 107.175.229[.]142, again via the user "cisco_support". Executed recon commands include:
show ip interface brief
show ip dns view
show ip name-servers
Cisco IOS XE und die verschwundenen Hintertüren
Die Anzahl der offensichtlich kompromittierten Geräte ist auch in Deutschland schlagartig gefallen, was wohl kaum an den gerade erschienenen Patches liegt.
🚨 #Cisco #IOSXE #CVE-2023-20198 #CVE-2023-20273
Let's recap on the exploitation activity this weekend in a thread. We are open-sourcing the logs from our honeypots, you can find them here: https://github.com/SIFalcon/research/tree/main/CVE-2023-20198
In total we recorded four exploitation attempts on our honeypots since Friday evening. Out of those, three incidents only differ by the password set for the "cisco_support" user in our logs.
A curious case occurred on Oct. 21 at 13:12 UTC when SELinux logged "ACV denied" msgs related to an exploit attempt. We can infer that a shell command with a heredoc was executed (sh-thd tmp files) + attempts to write nginx-conf, cisco_service.conf and an exec of "ps". The user account cleanup now also includes the other two account names "cisco_tac_admin" and "cisco_sys_manager", that were previously documented by Cisco, but did not show up in any of our logs.
Low confidence: the SELinux logs could be related to the "cleanup" of the implant that seems to have occurred. According to @shadowserver
the number of appliances with active implants plummeted suddenly: https://dashboard.shadowserver.org/statistics/combined/time-series/?date_range=7&source=compromised_website&source=compromised_website6&tag=device-implant%2B&group_by=geo&style=stacked
.@BleepingComputer is also reporting on the significant decrease of active webshells, with details on how or why still unclear.
📰 You can find the article here: https://bleepingcomputer.com/news/security/number-of-hacked-cisco-ios-xe-devices-plummets-from-50k-to-hundreds/
Feel free to share your interpretations and observations on the matter! 😃
As a side note: Cisco updated their advisory to include the second vulnerability (#CVE-2023-20273) and is now providing a patch for the most recent IOS XE version 17.9: https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z#REC
If you have not already done so, you should patch your #Cisco devices with #IOSXE now. It appears that this #vulnerability is already being actively exploited.
#CVE-2023-20198
Wer es noch nicht getan hat, sollte jetzt seine #Cisco Geräte mit #IOSXE patchen. Offensichtlich wird die #Sicherheitslücke bereits aktiv ausgenutzt.
#CVE-2023-20198
🚨 #Cisco #IOSXE #CVE-2023-20198
A new Priv. Esc. vulnerability in the web UI of many Cisco enterprise network appliances (e.g. Catalyst series) is actively being exploited.
📰 Check out our advisory here: https://secuinfra.com/en/techtalk/cisco-ios-xe-vulnerability-cve-2023-20198-thousands-of-internet-exposed-devices-potentially-compromised/
➡️#CompromiseAssessment #dfir 🔍
The raw numbers recorded by Shadowserver are looking very bleak...
New Cisco IOS XE zero day vulnerability has been disclosed as CVE-2023-20198.
This vulnerability is being actively exploited with thousands of Cisco IOS XE devices being breached.
This vulnerability has a CVSS score of 10/10 and affects any Cisco IOS XE devices with HTTP/HTTPS service enabled & is Internet facing. Successful exploitation by the attacker could allow them to create admin-level accounts & take over the network.
https://arstechnica.com/security/2023/10/actively-exploited-cisco-0-day-with-maximum-10-severity-gives-full-network-control/
#infosec #cybersecurity #Cisco #IOSXE #CVE_2023_20198 #zeroday
"🚨 Critical Vulnerability in Cisco IOS XE Software Web UI! 🚨"
Cisco has identified a critical privilege escalation vulnerability in the web UI feature of Cisco IOS XE Software. If exposed to the internet or untrusted networks, this flaw allows remote, unauthenticated attackers to create an account with privilege level 15 access, potentially gaining control of the affected system. 🕸️💻
Cisco is actively aware of the exploitation of this vulnerability. The issue was discovered during the resolution of multiple Cisco TAC support cases. There are currently no workarounds available. However, Cisco recommends disabling the HTTP Server feature on all internet-facing systems as a precautionary measure. 🚫🌐
For more details and to check if your system might be affected, visit the official advisory: Cisco Security Advisory
Tags: #Cisco #IOSXE #WebUI #Vulnerability #PrivilegeEscalation #CyberSecurity #InfoSec #PatchNow 🛡️🔐
"Mehr als 15 Millionen verwundbare Systeme mit #Schwachstellen aus dem Known-Exploited-Vulnerabilities-Catalog (#KEV) der US-Cyber-#Sicherheitsbehörde #CISA haben IT-Sicherheitsforscher von Rezilion mit der Datenbank #Shodan aufgespürt."
#KRITIS #Security #Exploits #Windows #AdobeFlashPlayer #InternetExplorer #MicrosoftOffice #GoogleChrome #AppleiOS #CiscoIOS #IOSXE