#ESETresearch joins Europol’s Cyber Intelligence Extension Programme (CIEP) 🤝 We are proud to announce ESET’s participation in the pilot phase of CIEP, a new initiative launched by Europol 's European Cybercrime Centre (EC3).
The program aims to strengthen public-private cooperation in the fight against cybercrime by enabling real-time collaboration and intelligence sharing. ESET Chief Research Officer Roman Kovac & Senior Malware Researcher Jakub Soucek, spent several days at Europol’s HQ.
ESET has already cooperated in EC3's Advisory Group, where we are represented by ESET Senior Research Fellow Righard Zwienenberg. ESET has also contributed to successful law enforcement operations: #Gamarue, #RedLine, #Grandoreiro, #LummaStealer #Danabot.
The new CIEP initiative elevates this collaboration further, creating opportunities for direct, real-time engagement with Europol’s operational teams. Partnerships like this one are crucial in mitigating risks within today's rapidly evolving cyber threat landscape.
Cyber threats evolve rapidly, but through these partnerships, so does our collective defense. Together we can make Europe a safer place. 🤝
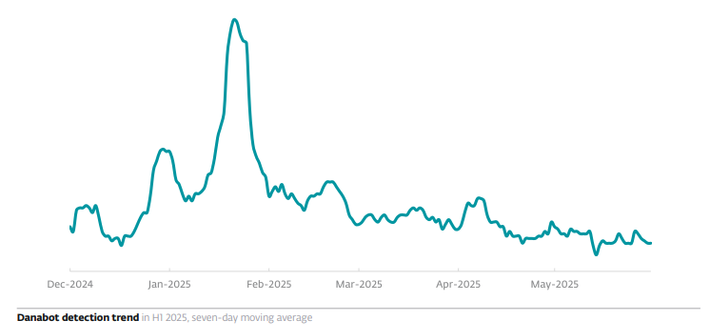
#DanaBot
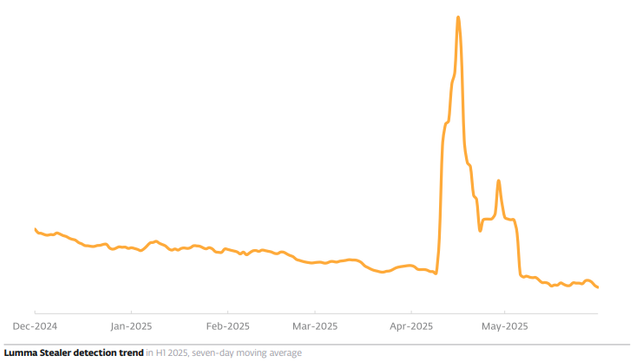
In May 2025, #ESET participated in operations that largely disrupted the infrastructure of two notorious infostealers: #LummaStealer and #Danabot.
As part of the Lumma Stealer disruption effort, carried out in conjunction with Microsoft, BitSight, Lumen, Cloudflare, CleanDNS, and GMO Registry, ESET supplied technical analysis and statistical information.
Danabot was targeted by the #FBI and #DCIS, alongside #OperationEndgame led by #Europol and #Eurojust. ESET participated together with several other companies. We provided the analysis of the malware’s backend infrastructure and identified its C&C servers.
Before these takedowns, both infostealers were on the rise: in H1 2025, Lumma Stealer detections grew by 21%, while Danabot’s numbers increased by more than 50%.
For a time, Lumma Stealer was the primary payload of HTML/FakeCaptcha trojan, used in the #ClickFix social engineering attacks that we also cover in this issue of the #ESETThreatReport. In recent months, we have seen Danabot being delivered via ClickFix as well.
For more details on these two operations and on the ClickFix attacks, read the latest #ESETThreatReport: https://welivesecurity.com/en/eset-research/eset-threat-report-h1-2025
Zazwyczaj donoszę Wam (oczywiście uprzejmie) o wyciekach, kradzieżach, szpiegostwie i innych bezpiecznikowych katastrofach. Ale dziś? Mamy dwie gigantyczne wygrane w wojnie z cyberprzestępcami - i to z polskim akcentem! 🦫
W nowym odcinku opowiadam o spektakularnym rozbiciu LummaStealera i ciosie wymierzonym w Danabota - dwóch złośliwych bestiach, które przez lata truły życie firmom i zwykłym użytkownikom na całym świecie. Jak działały? Jak je rozpracowano? Jakie miało to konsekwencje?
I co najważniejsze - jak w ogóle wygląda "fraud-as-a-service" od kuchni, łącznie z cenami, dokumentacją i obsługą klienta 24/7?
Odcinek przygotowany przy współpracy z ESET i DAGMA Bezpieczeństwo IT🦾
Zapraszam 👇
https://youtu.be/fcTdhBq4U88
#cybersecurity #LummaStealer #Danabot #ESET #DagmaBezpieczeństwoIT
DanaBleed: DanaBot C2 Server Memory Leak Bug from https://www.zscaler.com/blogs/security-research/danableed-danabot-c2-server-memory-leak-bug
The security researchers used a bug in an updated version of DanaBot, where a new buffer was allocated but not initialized and thus contained some process information of the C2 like username, IP address, victim etc.
Well done! That was clever.
cc: @VirusBulletin
A tiny memory flaw turned the tables on cybercrime. How did a missed byte expose a hidden criminal network and spark a massive law enforcement takedown? Read on for how DanaBleed changed the game.
https://thedefendopsdiaries.com/the-danableed-vulnerability-a-turning-point-in-cybersecurity/
A tiny coding error unleashed a cyber sleight of hand—leaking sensitive data and setting off a takedown of a notorious malware network. How did a forgotten memory bug bring cybercriminals to their knees?
https://thedefendopsdiaries.com/danableed-a-turning-point-in-cybersecurity/
DanaBleed: DanaBot C2 Server Memory Leak Bug
#DanaBot
https://www.zscaler.com/blogs/security-research/danableed-danabot-c2-server-memory-leak-bug
🚨 Researchers warn of a surge in #ClickFix scams impersonating #Booking.com. Fake CAPTCHAs trick users into running malware like XWorm and DanaBot.
Read: https://hackread.com/clickfix-email-scam-fake-booking-com-emails-malware/
Operation Endgame 2: 15 Millionen E-Mail-Adressen und 43 Millionen Passwörter | Security https://www.heise.de/news/Operation-Endgame-2-15-Millionen-E-Mail-Adressen-und-43-Millionen-Passwoerter-10396199.html #HaveIBeenPwned #Malware #Ransomware #Hacking #CyberCrime #Bumblebee #Latrodectus #Qakbot #DanaBot #HijackLoader #Warmcookie #Trickbot #Prolock #Doppelpaymer #REvil #Conti #BlackBasta #Cactus #OperationEndgame2
Global operation dismantles DanaBot malware network, indicting 16 and recovering $50M+ in losses. #Cybersecurity #DanaBot #OperationEndgame
More details: https://cyberscoop.com/danabot-malware-botnet-seizure-takedown - https://www.flagthis.com/news/15679
El #gobierno de EE. UU. desmanteló la red de malware #DanaBot y acusa a 16 personas en una operación global de ciberdelincuencia de 50 millones de dólares
https://blogs.masterhacks.net/noticias/hacking-y-ciberdelitos/ee-uu-desmantela-la-red-de-malware-danabot-y-acusa-a-16-personas-en-una-operacion-global-de-ciberdelincuencia-de-50-mdd/
#DanaBot botnet disrupted, #QakBot leader indicted: #OperationEndgame, mounted by law enforcement and judicial authorities from the US, Canada and the EU, continues to deliver positive results by disrupting the DanaBot botnet and indicting the leaders of both the DanaBot and Qakbot Malware-as-a-Service operations. (May 2025)
🔥 Latest issue of my curated #cybersecurity and #infosec list of resources for week #21/2025 is out!
It includes the following and much more:
🇦🇪 🇺🇸 UAE Recruiting US Personnel Displaced by #DOGE to Work on #AI for its Military;
🇺🇸 Madhu Gottumukkala New Deputy Director of #CISA;
📊 New metric called Likely Exploited Vulnerabilities (LEV) introduced;
🇪🇺 European Union sanctions Stark Industries for enabling #cyberattacks;
❌ 📸 @signalapp now blocks #Microsoft Recall screenshots on #Windows 11;
🇺🇸 🇪🇺 The #FBI and #Europol have disrupted the Lumma Stealer #malware network;
❌ 🦠 #DanaBot malware operation taken down;
📨 Subscribe to the #infosecMASHUP newsletter to have it piping hot in your inbox every week-end ⬇️
https://infosec-mashup.santolaria.net/p/infosec-mashup-21-2025
Operation Endgame 2.0: 20 Haftbefehle, Hunderte Server außer Gefecht gesetzt | Security https://www.heise.de/news/Operation-Endgame-2-0-20-Haftbefehle-Hunderte-Server-ausser-Gefecht-gesetzt-10394215.html #OperationEndgame #OperationEndgame2 #Malware #Ranswomware #Hacking #CyberCrime #Bumblebee #Latrodectus #Qakbot #DanaBot #HijackLoader #Warmcookie #Trickbot #Prolock #Doppelpaymer #REvil #Conti #BlackBasta #Cactus
16 indicted in global DanaBot malware scheme causing $50M+ in damages. #Cybercrime #DanaBot #Malware
More details: https://cyberscoop.com/danabot-malware-botnet-seizure-takedown - https://www.flagthis.com/news/15513
⛔ #OperationEndgame: Police takes down DanaBot malware network; 300 servers neutralized, €21.2M in crypto seized and 16 charged/
Read: https://hackread.com/operation-endgame-danabot-malware-neutralizes-servers/
Inside DanaBot’s Infrastructure: In Support of Operation Endgame II
#DanaBot
https://blog.lumen.com/inside-danabots-infrastructure-in-support-of-operation-endgame-ii/
More 📰! @ESETresearch participated in global disruption of notorious infostealer #Danabot by the US DOJ, DOD and FBI, and others. Since 2018, @ESET Research has tracked the evolution of this powerful malware-as-a-service operation. 🔎💻
More👀: https://www.welivesecurity.com/en/eset-research/danabot-analyzing-fallen-empire/
Happy Friday everyone!
With the news breaking that the #DanaBot was disrupted, it got me thinking: How do these pieces of malware function and how do they stay on the victim's machines? And when you think of what a botnet operator really needs is repeated access to the compromised machine which gets me thinking about persistence. So, I poked around my favorite resources, the MITRE ATT&CK Matrix, looked at as many bot malware they have, and looked at what they had in common from a perspective of persistence. Two of the most common techniques used were T1547.001 - Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder and T1053.005 - Scheduled Task/Job: Scheduled Task. So, if you are hunting for bots, you may want to start there! Enjoy the read and Happy Hunting!
DanaBot malware disrupted, threat actors named
https://intel471.com/blog/danabot-malware-disrupted-threat-actors-named
Intel 471 Cyborg Security, Now Part of Intel 471 #ThreatIntel #ThreatHunting #ThreatDetection #HappyHunting #readoftheday
🔥 Operation Endgame is BACK! This time targeting #BumbleBee, #Latrodectus, #DanaBot, #WarmCookie, #Qakbot and #Trickbot!
Once again this is a HUGE win, with a truly international effort! 💪
As with phase one of #OperationEndgame, Spamhaus are providing remediation support - those affected will be contacted in due course with steps to take.
For more information, read our write-up here:
👉 https://www.spamhaus.org/resource-hub/malware/botnets-disrupted-worldwide-operation-endgame-is-back/