The only "irritation" I have is that this is the third time something got changed by the Exchange Team HOURS before an important meeting on breaking changes deadlines. COME ON! 😁
#MSExchange
Several hours ago the #MSExchange Team posted an update on the #SMTP AUTH Basic #Authentication timeline. To summarize: the original date of disabling the option of March 2026 is now delayed to H2 2027 for existing tenants. Newly created tenants will have to deal with this from December 2026.
Day 24 of #ITAdvent. And this concludes yet another run. I hope you found some usefull tips, I had a nasty cold so that might have had an impact. In any case, happy holidays and see you in the next year! And yes, I haven't forgotten that #MSExchange and Start-of-authority blog post ;-)
PSA: EWS block enforcement for Kiosk/Frontline SKUs has been moved back to the end of June https://xf.ms/NoEWSEnforced #MSExchange #Microsoft365
My topic? "IAM and Exchange: Untangling frenemies in Hybrid organizations". The relationship between Identities in Active Directory and Exchange has always tightly integrated, being hybrid made it more complex. I will discuss important IAM considerations designing, managing and moving away from AD.
More info: https://www.exchange-summit.de/ or https://www.linkedin.com/posts/msexchange-summit_exchangesummit-microsoftexchange-iam-activity-7403741450338725888-Zt_8
Day 12 of #ITAdvent. Short low effort self-plug as I'm a bit under the weather: I'll be speaking (in English) at the excellent in-person event Exchange Summit 2026 in Würzburg, Germany on 24/25 February 2026.
We’ve just released Security Updates for #MSExchange Server SE. These updates are also available to customers under the ESU program.
More information: https://techcommunity.microsoft.com/blog/exchange/released-december-2025-exchange-server-security-updates/4474949
Day 4 of #ITAdvent. I always appreciated the idea of Zero-Hour Auto-Purge (ZAP): removing malicious retroactively increasing #security. It works for #MSExchange and #MicrosoftTeams messages, but you needed Defender for O365 Plan 2, but that changes with #MC1187837 https://mc.merill.net/message/MC1187837
Heads-up: EWS blockage for Exchange Online mailboxes with Kiosk/F1/F3 license, which officially do not offer EWS access, will be enforced March 2026 https://xf.ms/NoEWSEnforced #MSExchange
Anyway, on that Start-of-Authority for groups and #MSExchange attributes: Learned a lot of the little things, gotcha's and all. It's really something anyone with a #hybrid org transitioning to cloud-only needs to look into.
Finished a little project removing the last #MSExchange server together with flipping the Start-of-Authority of Group objects and Exchange Attributes. Had to use ADSIEdit to remove some Exchange stuff, made it a bit more interesting 🤓
PSA: Exchange Online Admin API (EWS replacement subset) now available (preview). REST-like alternative for some EWS scenarios, but not full REST replacement; cmdlets still recommended for full functionality https://techcommunity.microsoft.com/blog/exchange/announcing-public-preview-exchange-online-admin-api/4470562?WT.mc_id=M365-MVP-5000284 #MSExchange #EWS
Endlich mal konkrete Infos, von #Outlook zu #Thunderbird und von #MSExchange zu #OpenExchange 👍 https://winfuture.de/news,154283.html
We’ve just released security updates for #MSExchange Server 2016-SE. These updates are the last publicly available SUs for Exchange Server 2016 and 2019.
Hybrid Exchange issues with Free/Busy? It's planned nudge day 3 of 3. Test-OAuthConnectivity likely shows 403 error, eg running (mix with) Exchange with pre-April patch levels. Affected? Act soon, permanent after EoM! https://bit.ly/ETOSecChanges #MSExchange
MS Exchange gibt es seit 1996. SMTP gibt es seit 1982. Microsoft adaptierte die Technologie und zwang Firmen ihre Server auf. Im Internet spielt #MSExchange kaum eine Rolle. Fast 90% sind Open Source. Exchange kennt man primär daher, wenn mal Probleme mit Mailservern auftreten. Und dann bekommt man kryptische Fehlermeldungen, die nicht-standard SMTP sind. Das Krisenmanagement der Landesregierung ist aber schlecht. Der Weg aber richtig. Weg vom Monopol hin zu Standards .
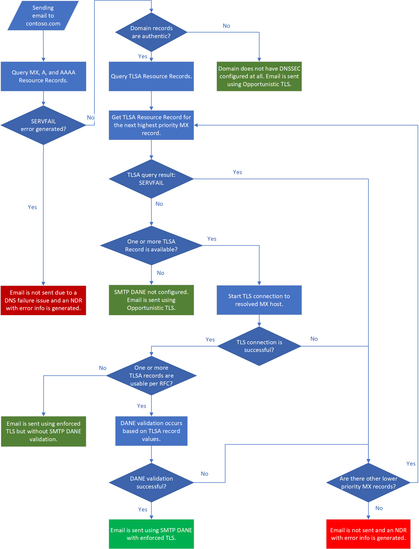
BTW: from October 1st new Accepted Domains will automatically use the new MX infrastructure, which will maken enabling DANE a little less of a hassle as there should be no change in your MX record. See MC1048624 or https://mc.merill.net/message/MC1048624
You must enable DANE on your domain as this change is currently only present on the new https://mx.microsoft infrastructure. Currently for existing accepted domains this is the way to transition to the new infrastructure, although eventually new accepted domains will use this automatically (you do still need to enable DNSSEC & DANE). See more on DANE here https://learn.microsoft.com/en-us/purview/how-smtp-dane-works?wt.mc_id=M365-MVP-5000976
Although for hosted services you do not have control over their certificate management, however I would find it reassuring if such a service would implement CAA. And: Since a few days #MSExchange Online now has CAA records!
With upcoming changes in the maximum validity period of certificates (max 200 days in 2026, 100 in 2027, 47 in 2029) the use of ACME (Automated Certificate Management Environment) will certainly increase. The addition of CAA and combination with ACME is another layer in your security stack. It's recommended for Dutch governments.