🚨 How #Rhadamanthys Stealer Slips Past Defenses using ClickFix
⚠️ Rhadamanthys is now delivered via ClickFix, combining technical methods and social engineering to bypass automated security solutions, making detection and response especially challenging.
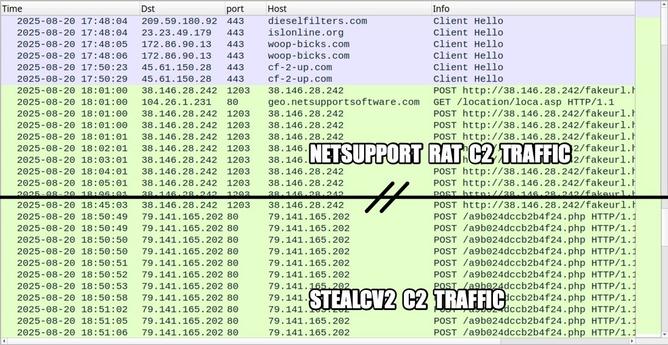
👾 While earlier ClickFix campaigns mainly deployed #NetSupport RAT or #AsyncRAT, this C++ infostealer ranks in the upper tier for advanced evasion techniques and extensive data theft capabilities.
#ANYRUN Sandbox lets SOC teams observe and execute complex chains, revealing evasive behavior and providing intelligence that can be directly applied to detection rules, playbooks, and proactive hunting.
🔗 Execution Chain:
ClickFix ➡️ msiexec ➡️ exe-file ➡️ infected system file ➡️ PNG-stego payload
In a recent campaign, the phishing domain initiates a ClickFix flow (#MITRE T1566), prompting the user to execute a malicious MSI payload hosted on a remote server.
🥷 The installer is silently executed in memory (#MITRE T1218.007), deploying a stealer component into a disguised software directory under the user profile.
The dropped binary performs anti-VM checks (T1497.001) to avoid analysis.
In later stages, a compromised system file is used to initiate a TLS connection directly to an IP address, bypassing DNS monitoring.
📌 For encryption, attackers use self-signed TLS certificates with mismatched fields (e.g., Issuer or Subject), creating distinctive indicators for threat hunting and expanding an organization’s visibility into its threat landscape.
🖼️ The C2 delivers an obfuscated PNG containing additional payloads via steganography (T1027.003), extending dwell time and complicating detection.
🎯 See execution on a live system and download actionable report: https://app.any.run/tasks/a101654d-70f9-40a5-af56-1a8361b4ceb0/?utm_source=mastodon&utm_medium=post&utm_campaign=rhadamanthys&utm_term=120825&utm_content=linktoservice
🔍 Use these #ANYRUN TI Lookup search queries to track similar campaigns and enrich #IOCs with live attack data from threat investigations across 15K SOCs:
https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=rhadamanthys&utm_content=linktoti&utm_term=120825#%7B%2522query%2522:%2522threatName:%255C%2522clickfix%255C%2522%2522,%2522dateRange%2522:180%7D
https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=rhadamanthys&utm_content=linktoti&utm_term=120825#%7B%2522query%2522:%2522threatName:%255C%2522rhadamanthys%255C%2522%2522,%2522dateRange%2522:180%7D
https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=rhadamanthys&utm_content=linktoti&utm_term=120825#%7B%2522query%2522:%2522(threatName:%255C%2522clickfix%255C%2522%2520OR%2520threatName:%255C%2522susp-clipboard%255C%2522)%2520AND%2520threatName:%255C%2522netsupport%255C%2522%2522,%2522dateRange%2522:180%7D
https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=rhadamanthys&utm_content=linktoti&utm_term=120825#%7B%2522query%2522:%2522(threatName:%255C%2522clickfix%255C%2522%2520OR%2520threatName:%255C%2522susp-clipboard%255C%2522)%2520AND%2520threatName:%255C%2522asyncrat%255C%2522%2522,%2522dateRange%2522:180%7D
👾 IOCs:
84.200[.]80.8
179.43[.]141.35
194.87[.]29.253
flaxergaurds[.]com
temopix[.]com
zerontwoposh[.]live
loanauto[.]cloud
wetotal[.]net
Find more indicators in the comments 💬
Protect critical assets with faster, deeper visibility into complex threats using #ANYRUN 🚀
#cybersecurity #infosec


![Example of initial URL from sites.google[.]com.](https://files.mastodon.social/cache/media_attachments/files/115/805/248/319/213/212/small/a269fb9f29e1651b.jpg)













![Screenshot of the browser window for a fake update page after visiting a compromised website at banks-canada[.]com.](https://files.mastodon.social/cache/media_attachments/files/113/666/471/479/580/503/small/df42333967103df4.jpg)
![Example of SmartApeSG injected script highlighted in orange in HTML code from a page from the compromised site. The URL from this injected script is hxxps[:]//depostsolo[.]biz/work/original.js](https://files.mastodon.social/cache/media_attachments/files/113/666/471/509/749/692/small/be4be6777759a010.jpg)
![Traffic from an infection filtered in Wireshark showing the NetSupport RAT post-infection traffic to 194.180.191[.]64 over TCP port 443. All of the SmartApeSG and fake browser update page traffic prior to the NetSupport RAT activity is over HTTPS.](https://files.mastodon.social/cache/media_attachments/files/113/666/471/535/207/024/small/9fe0727827475553.jpg)
![The NetSupport RAT installation persistent on an infected Windows host. Shows the Windows registry entry for persistence and the associated NetSupport RAT files. The file are located in a hidden directory at C:\ProgramData\cvkfkmt\ with the NetSupport RAT executable client32.exe using client32.ini for its configuration to use the malicious C2 server at 194.180.191[.]64.](https://files.mastodon.social/cache/media_attachments/files/113/666/471/559/760/363/small/f065d295993a6219.jpg)