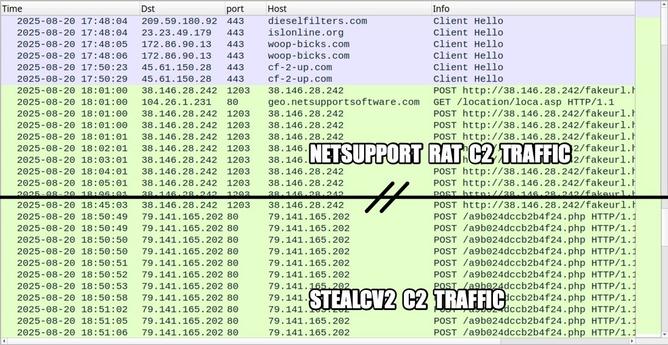
Campaign uses ClickFix page to push NetSupport RAT
The SmartApeSG campaign, also known as ZPHP or HANEYMANEY, has evolved from using fake browser update pages to employing ClickFix-style fake CAPTCHA pages. This campaign distributes malicious NetSupport RAT packages as its initial infection vector. The attack chain begins with an injected script on compromised websites, which, under certain conditions, displays a fake CAPTCHA page. When users interact with this page, malicious content is injected into the Windows clipboard, prompting users to paste and execute it. This leads to the download and installation of NetSupport RAT, which maintains persistence through a Start Menu shortcut. The campaign frequently changes domains, packages, and C2 servers to evade detection.
Pulse ID: 69370db0cd2bc81cbbe13d51
Pulse Link: https://otx.alienvault.com/pulse/69370db0cd2bc81cbbe13d51
Pulse Author: AlienVault
Created: 2025-12-08 17:41:04
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#Browser #CAPTCHA #Clipboard #CyberSecurity #FakeBrowser #InfoSec #NetSupport #NetSupportRAT #OTX #OpenThreatExchange #PHP #RAT #SmartApeSg #Windows #bot #AlienVault