Good day everyone!
Cisco Talos brings us a HOT report on a new backdoor they observed in a widespread campaign that they dubbed #TorNet, owing to the fact that the actor connects the victim's machine to the TOR network for stealthy command and control (C2) communications and detection evasion.
Attack Summary:
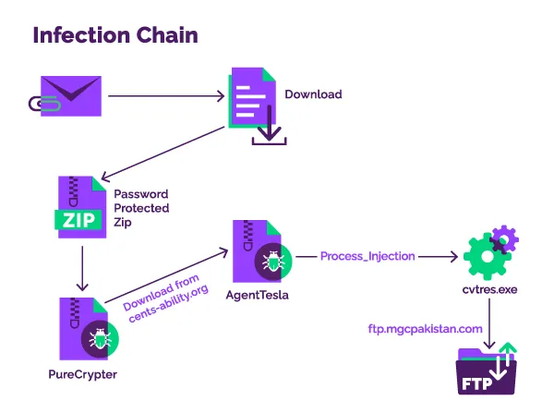
The attack starts with a phishing email with a malicious attachment, which leads to a .NET loader executing and downloads the #PureCrypter malware, which is responsible for dropping and running the TorNet backdoor. After a successful connection to the C2 server it connects the victim's machine to the TOR network which enables it to receive and run arbitrary .NET assemblies in memory.
Behavior Summary:
Initial Access:
Phishing Email with Attachment - in this case, a .tgz (compressed file)
Defense Evasion
Released and renewed the ip address of the compromised machine - "cmd /c ipconfig /release" and "cmd /c ipconfig /renew"
Modifcaiton of the machine - "Add-MpPreference -ExclsuionPath" and "Add-MpPreference -ExclusionProcess"
Discovery:
WMI Activity - "Select * from Win32_BIOS" and "Select * from Win32_ComputerSystem"
Persistence:
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder - Dropped a VB script in the windows Startup folder
These are just some of the behaviors, for the rest, go and enjoy the read! Happy Hunting!
New TorNet backdoor seen in widespread campaign
https://blog.talosintelligence.com/new-tornet-backdoor-campaign/
Intel 471 Cyborg Security, Now Part of Intel 471 #ThreatIntel #ThreatHunting #ThreatDetection #HappyHunting #readoftheday