Secure your online world with RoboForm Password Manager, the ultimate tool for keeping your credentials safe and accessible! Enjoy one-click logins, cross-device syncing, and military-grade encryption to protect against cyber threats. Don't miss out on our limited-time deals—take control of your digital security today! #CyberSecurity #PasswordManager #StaySafeOnline #RoboForm
https://livingsafeonline.com/product/roboform-password-manager/
#Roboform
-2-
Joe and Bruno's Guide to Hacking Time: Regenerating Passwords from RoboForm's Password Generator
When Joe started talking about RoboForm and cracking password generators, something clicked — I remembered watching a Youtube video about abusing random number generation to unlock a bitcoin wallet worth millions...
Turns out, it was Joe and Bruno’s video! It’s incredibly well-edited, and you should definitely watch it right after the DEFCON talk (though it spoils the ending a little 😉): https://www.youtube.com/watch?v=o5IySpAkThg
The talk dives into pseudo-random number generators (PRNGs) — software that takes an initial seed to generate a sequence of random numbers. If the generator doesn’t use real randomness (like lava lamps, for example), knowing the initial seed lets you predict all the numbers it will generate, including passwords.
RoboForm, a well-known password generator, used to rely on the current time as its seed — specifically a Unix timestamp in seconds. Unfortunately, this means that the number of passwords that can possibly be generated given a time frame is relatively small. This means that if you know roughly when a password was generated and its options (like length, capitals, symbols), you could easily brute-force all possible passwords in that timeframe.
Joe and Bruno exploited this exact idea! They knew (from the wallet’s owner) when the password was generated and the generation options. They reverse-engineered the RoboForm app, found a way to iteratively change the system time, and hooked into the code to regenerate the password as if it was created back then.
They managed to generate around 1,000 passwords per second, and within hours, they cracked open the wallet!
https://www.youtube.com/watch?v=N2eKCAzM2kw
#DEFCON
#Passwords
#RoboForm
#HackingTime
Gestor de contraseñas y 2FA ROBOFORM -> https://burp.es/gestor-de-contrasenas-y-2fa-roboform/
#roboform
Probando el gestor de contraseñas RoboForm. Muy, muy bien de momento.
Security Week 2423: о плохих генераторах случайных чисел и пароле к криптокошельку
«Взлом» криптокошелька, пароль к которому был утерян больше 10 лет назад, — это самая красивая история по теме кибербезопасности на прошлой неделе. Пожелавший остаться анонимным пользователь приобрел биткоины на сумму примерно 4000 евро в 2013 году. Криптовалюта хранилась в цифровом кошельке, доступ к которому был защищен паролем. Известный исследователь Джо Гранд на пару с коллегой помогли владельцу криптокошелька восстановить пароль, и не при помощи простого перебора, а, как правильно отметили в обсуждении на Хабре, «решив проблему мозгами». Джо Гранд любит подавать свои истории красиво, он снял видео и дал интервью журналу Wired, где использовал красивые и понятные более широкой аудитории метафоры типа «мы нашли способ повернуть время вспять». Реально интересная техническая информация этой работы, впрочем, уместилась на одну страницу текстом . Для облегчения «взлома» криптокошелька хакерам требовалось уменьшить количество возможных вариаций пароля для перебора. Им удалось это сделать благодаря одной особенности программы RoboForm, которую владелец кошелька использовал для генерации пароля. И это, пожалуй, самое интересное: анализ старой версии RoboForm показывает нам пример, как не надо генерировать случайные последовательности символов.
The #RoboForm password regeneration source code and technical notes are up! https://grandideastudio.com/portfolio/security/roboform-password-regeneration/
How Researchers Cracked an 11-Year-Old #Password to a $3 Million#CryptoWallet
Thanks to a flaw in a decade-old version of the #RoboForm password manager and a bit of luck, researchers were able to unearth the password to a #crypto wallet containing a fortune.
#security
https://www.wired.com/story/roboform-password-3-million-dollar-crypto-wallet/
How Researchers Cracked an 11-Year-Old Password to a $3 Million Crypto Wallet | WIRED
https://www.wired.com/story/roboform-password-3-million-dollar-crypto-wallet/
Thanks to a flaw in a decade-old version of the RoboForm password manager and a bit of luck, researchers were able to unearth the password to a crypto wallet containing a fortune.
🌘 研究人員破解11年前價值300萬美元的加密錢包的密碼
➤ 研究人員利用漏洞找回11年前的加密錢包密碼
✤ https://www.wired.com/story/roboform-password-3-million-dollar-crypto-wallet/
研究人員利用一個十年前版本的RoboForm密碼管理器的漏洞和一些運氣找到了一個加密錢包的密碼,其中包含著一大筆財富。
+ 這真是太厲害了!破解加密錢包的方法層出不窮,這次的方法與之前的不同,仍然令人驚訝。
+ 這再次證明瞭密碼安全的重要性,我們應該時刻保持警惕。
#加密錢包 #密碼破解 #RoboForm
@stk @shipp @mmiasma @tokyo_0 @cooopsspace
@alfredo @xmetal
EN
Thanks SO much everyone for the tips and encouragement about dealing with my gmail password problems! I've purchased and installed #Roboform as an affordable #PasswordManager and I've set them as the default for passwords on my phone. Always a learning curve with a new process. Since I have 2FA for Google, it's possible that folks couldn't do anything with my password, even if they found it. I've had no unusual security alerts.
#RoboForm "Version 9.4.3 Feb 28, 2023
* Security: fixed a number of security bugs mentioned in the security audit report.
...
* Security: increased default number of PBKDF2 iterations to 100,000.
..."
Not high enough, but better than the 4096 it was before. You can manually up this, and I suggest you do (300,000+). Now what is this security audit report that they mention? No posts about it on BirdSite or their blog. #lastpass
Which password manager do you use? If you choose other, please comment and mention which one you use.
P. S.: About to migrate away from LastPass and am looking for suggestions...
#lastpass #hack #hacked #passwords #1password #bitwarden #nordpass #roboform #iolo #totalav #kaspersky #vault #security
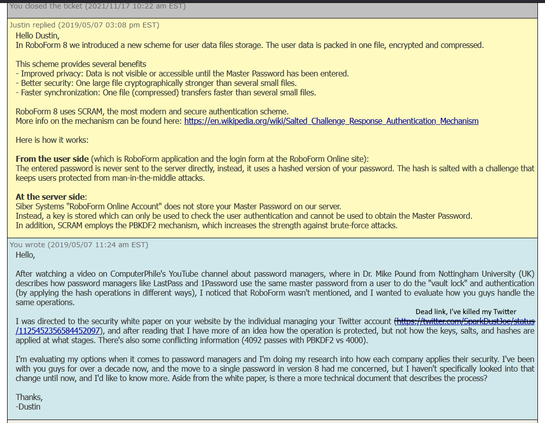
Regarding #LastPass Alternativies: Oh great, #RoboForm uses PBKDF2 SHA256 as well... with 4096 iterations (still the default) and not HMAC apparently... crap! It IS configurable on the number of iterations (ticket screenshot attached is from Version 8, they are on Version 9 now, according to their website, looks like they are in the same boat). DEFINITELY time to update the number of iterations! (originally posted Dec 22, 2022, 20:22, had wrong privacy settings, third time's the charm...)
Tijden tevreden klant geweest bij #Lastpass echter de laatste tijd teveel issues geweest. Vooral de toegang to de broncode is een groot risico.
Ben nu bezig met overstap naar #RoboForm.
Mooi moment om meteen wat accounts op te zeggen die ik niet gebruik. Jammer dat je op sommige sites wel makkelijk een account kunt aanmaken maar verwijderen niet makkelijk is, zoals bijvoorbeeld bij @Tweakers waar je een formulier bij de consumentenbond moet invullen.
I haven't used #LastPass for about 4 years, but certainly I still had a vault on their server.
I've been using #Roboform, and took at a look at it today.
Of the 2,000 logins, about 300 were classified as weak #passwords, or had turned up at some point in HIBP.
I started changing the weak ones. Since I've been on the internet 30 years, there was a shitload of sites that were long gone, merged or which I had log forgotten. Yet my password manager keeps those for me, forever. Throwing more garbage onto a never ending pile of passwords that can only get bigger.
I don't have time to regularly change 2,000 passwords. I can't manage the time to weed the website garden.
It seems every year there's a great idea for replacing the password that never comes to adoption. Meanwhile, the password pile gets even deeper.
I'm seriously considering a clean start. A change of phone number, change of email, just pick the top 50 sites I regularly use, scale back the online services I use, and let everything else just rot.
@jenny_sivapalan If you do look to moving in be been very happy with #RoboForm.
Moderne Passwortmanager sollten sich komfortabel auf verschiedenen Geräten nutzen lassen, gut einstellbar sein und nicht zu viele Nutzungsdaten weitergeben.
Im Test: 25 Passwortmanager für PC und Smartphone
What is your password manager of choice?
Polls are limited to 4 options?
#infosec #linux #password #security #lastpass #1password #bitwarden #icloud #roboform #dashlane
Wer einem Passwortmanager Zugangsdaten anvertraut, will diese sicher wissen. Deswegen prüfen wir, ob die Produkte Geheimnisse auf unvorgesehenen Wegen verraten.
Passwortmanager im Sicherheitscheck: Speicher und Netzwerkverkehr analysiert
#1Password #Avira #AviraPasswordManager #Bitwarden #Blur #Cyclonis #Dashlane #Keepass #Keeper #Lastpass #McAfee #OneSafeSafePasswords #Passwort-Manager #Passwörter #RoboForm #SaferPass #Steganos #SteganosPasswort-Manager #StickyPassword #TrueKey
Passwortmanager sollen nicht nur sicher, sondern auch komfortabel sein. Daher müssen die Testkandidaten Cloudspeicher und 2FA unterstützen.
15 Passwortmanager im Vergleich
#1Password #Avira #AviraPasswordManager #Bitwarden #Blur #Cyclonis #Dashlane #Keepass #Keeper #Lastpass #McAfee #OneSafeSafePasswords #Passwort-Manager #Passwörter #RoboForm #SaferPass #Steganos #SteganosPasswort-Manager #StickyPassword #TrueKey