Top 10 last week's threats by uploads 🌐
⬇️ #Xworm 550 (944)
⬇️ #Quasar 354 (364)
⬇️ #Vidar 282 (371)
⬇️ #Asyncrat 247 (396)
⬇️ #Lumma 222 (284)
⬇️ #Stealc 221 (354)
⬆️ #Guloader 197 (181)
⬆️ #Agenttesla 186 (172)
⬇️ #Smoke 148 (153)
⬇️ #Remcos 128 (212)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=221225&utm_content=linktoregister#register
#Xworm
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 944 (870)
⬇️ #Asyncrat 396 (413)
⬆️ #Vidar 371 (318)
⬇️ #Quasar 364 (395)
⬆️ #Stealc 354 (266)
⬆️ #Lumma 284 (282)
⬇️ #Remcos 213 (269)
⬆️ #Guloader 181 (179)
⬆️ #Agenttesla 173 (141)
⬇️ #Smoke 153 (158)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=151225&utm_content=linktoregister#register
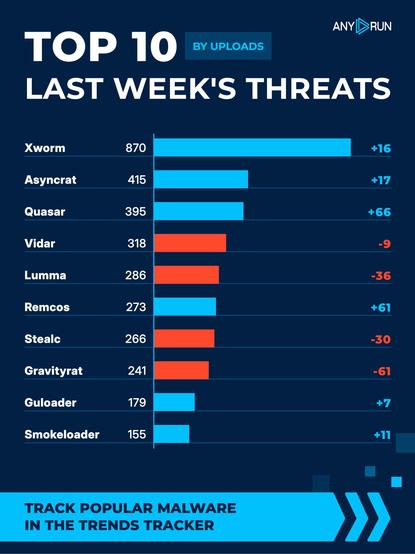
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 870 (854)
⬆️ #Asyncrat 415 (398)
⬆️ #Quasar 395 (329)
⬇️ #Vidar 318 (327)
⬇️ #Lumma 286 (322)
⬆️ #Remcos 273 (212)
⬇️ #Stealc 266 (296)
⬇️ #Gravityrat 241 (302)
⬆️ #Guloader 179 (172)
⬆️ #Smokeloader 155 (144)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=081225&utm_content=linktoregister#register
#xworm SHA256: ad6518380ade796c3d461e42342a5735bf5355a422a0004bf4d907bcbc3eb991 C2: 191[.]96[.]225[.]192:1337
Top 10 last week's threats by uploads 🌐
⬇️ #Xworm 854 (1042)
⬆️ #Asyncrat 398 (381)
⬇️ #Quasar 329 (413)
⬆️ #Vidar 327 (316)
⬇️ #Lumma 322 (370)
⬆️ #Gravityrat 302 (255)
⬆️ #Stealc 299 (251)
⬆️ #Mircop 288 (247)
⬇️ #Remcos 214 (248)
⬆️ #Guloader 172 (168)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=011225&utm_content=linktoregister#register
⚠️ #XWorm in PNG files, #JSGuLdr’s three-stage loader, Linux #ransomware, Android RATs; November was packed with multi-layered attacks.
See the full analysis of the month’s major threats and key detection takeaways for SOC teams 👇
https://any.run/cybersecurity-blog/major-cyber-attacks-november-2025/?utm_source=mastodon&utm_medium=post&utm_campaign=cyber-attacks-nov-2025&utm_term=261125&utm_content=linktoblog
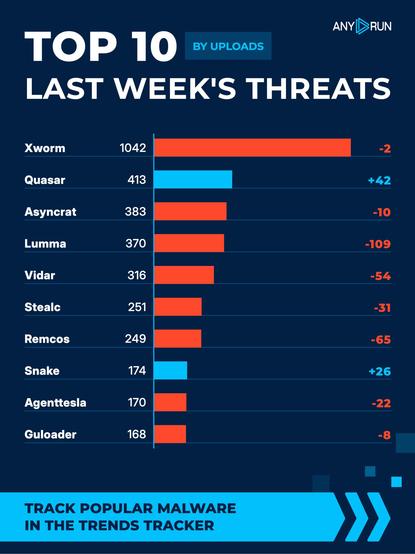
Top 10 last week's threats by uploads 🌐
⬇️ #Xworm 1042 (1044)
⬆️ #Quasar 413 (371)
⬇️ #Asyncrat 383 (393)
⬇️ #Lumma 370 (479)
⬇️ #Vidar 316 (370)
⬇️ #Stealc 251 (282)
⬇️ #Remcos 249 (314)
⬆️ #Snake 174 (148)
⬇️ #Agenttesla 170 (192)
⬇️ #Guloader 168 (176)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=241125&utm_content=linktoregister#register
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 1044 (641)
⬆️ #Lumma 479 (476)
⬆️ #Asyncrat 398 (275)
⬇️ #Quasar 371 (390)
⬆️ #Vidar 370 (292)
⬆️ #Remcos 318 (271)
⬆️ #Stealc 282 (174)
⬆️ #Agenttesla 193 (167)
⬆️ #Guloader 176 (171)
⬇️ #Smoke 160 (164)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=171125&utm_content=linktoregister#register
Top 10 last week's threats by uploads 🌐
⬇️ #Xworm 641 (885)
⬇️ #Lumma 476 (641)
⬇️ #Quasar 390 (554)
⬇️ #Rhadamanthys 296 (463)
⬇️ #Vidar 292 (350)
⬇️ #Asyncrat 278 (368)
⬇️ #Remcos 272 (410)
⬇️ #Snake 181 (346)
⬇️ #Stealc 174 (255)
⬇️ #Guloader 171 (175)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=101125&utm_content=linktoregister#register
🚨#XWorm: PNGs hiding an in-memory loader.
A malicious JavaScript installer named PurchaseOrder_25005092.JS is delivered via #phishing pages and emails (T1566.001). The script uses an IIFE-style obfuscation (T1027), writes three staged files to C:\Users\PUBLIC, and creates a scheduled task to ensure persistence (T1053.005).
This JS checks for required artifacts and, if missing, writes them to disk using long Base64 blobs and AES-encrypted strings (T1027.013). The staged files are named Kile.cmd, Vile.png, and Mands.png.
⚠️ .png files are not images, they are storage containers for Base64-encoded encrypted payloads (T1036.008). It is a common technique to evade quick detection.
Kile.cmd is a heavily obfuscated batch script with variable noise, percent-based substitutions, chunked Base64 fragments, that reassembles commands at runtime.
❗️ At execution, the JS reconstructs readable commands from those fragments and launches a PowerShell payload (T1059). The PowerShell is a two-stage AES-CBC loader:
1️⃣ Reads C:\Users\PUBLIC\Mands.png as Base64 ➡️ AES-decrypt ➡️ yields Base64-encoded commands. Each command is decoded and executed via Invoke-Expression (IEX). This acts as a command runner.
2️⃣ Reads C:\Users\PUBLIC\Vile.png as Base64 ➡️ AES-decrypt ➡️ raw bytes. The loader attempts to load a .NET assembly from memory and execute its entry point (T1620).
This is an in-memory assembly loader, a fileless/memory-loader pattern: command runner + in-memory payload.
👾 At the end, PowerShell runs an assembly in memory to launch XWorm.
A single successful XWorm infection can give adversaries access to critical systems, leading to breaches and operational disruption. Once inside, attackers can steal data, move laterally, and cause costly downtime.
👨💻 Get fast detection and full visibility with #ANYRUN. See live execution and download actionable report: https://app.any.run/tasks/bec21e02-8fb5-4a18-b43c-131e02e21041/?utm_source=mastodon&utm_medium=post&utm_campaign=png-xworm&utm_term=051125&utm_content=linktoservice
👨🍳 Use this CyberChef recipe to decode the final PowerShell string:
https://gchq.github.io/CyberChef/#recipe=Find_/_Replace(%7B'option':'Simple%20string','string':'EPMNJLDRV'%7D,'',true,false,true,false)From_Base64('A-Za-z0-9%2B/%3D',true,false)Decode_text('UTF-16LE%20(1200)')&oenc=65001&ieol=CRLF&oeol=CRLF
🔍 Find similar campaigns using these TI Lookup search queries and enrich #IOCs:
🔹 PowerShell .Replace() obfuscation: https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=png-xworm&utm_content=linktoti&utm_term=051125#%7B%2522query%2522:%2522imagePath:%255C%2522%255C%255C%255C%255Cpowershell.exe$%255C%2522%2520AND%2520commandLine:%255C%2522.Replace(%255C%2522%2522,%2522dateRange%2522:180%7D%20
🔹 PowerShell invoking IEX: https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=png-xworm&utm_content=linktoti&utm_term=051125#%7B%2522query%2522:%2522imagePath:%255C%2522%255C%255C%255C%255Cpowershell.exe$%255C%2522%2520AND%2520commandLine:%255C%2522iex%255C%2522%2522,%2522dateRange%2522:180%7D
🔹 JS droppers in Public\Libraries: https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=png-xworm&utm_content=linktoti&utm_term=051125#%7B%2522query%2522:%2522filePath:%255C%2522%5EC:%255C%255C%255C%255CUsers%255C%255C%255C%255CPublic%255C%255C%255C%255CLibraries%255C%255C%255C%255C*.js$%255C%2522%2522,%2522dateRange%2522:180%7D
Gain full visibility with #ANYRUN to make faster, smarter security decisions 🚀
Top 10 last week's threats by uploads 🌐
⬇️ #Xworm 885 (954)
⬆️ #Lumma 641 (448)
⬆️ #Quasar 554 (389)
⬆️ #Rhadamanthys 463 (268)
⬆️ #Remcos 415 (299)
⬆️ #Asyncrat 370 (231)
⬆️ #Dcrat 356 (228)
⬆️ #Vidar 350 (249)
⬆️ #Snake 346 (111)
⬆️ #Agenttesla 323 (116)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=031125&utm_content=linktoregister#register
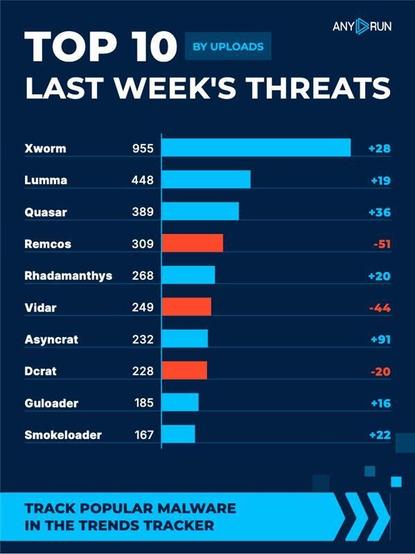
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 955 (927)
⬆️ #Lumma 448 (429)
⬆️ #Quasar 389 (353)
⬇️ #Remcos 309 (360)
⬆️ #Rhadamanthys 268 (248)
⬇️ #Vidar 249 (293)
⬆️ #Asyncrat 232 (141)
⬇️ #Dcrat 228 (248)
⬆️ #Guloader 185 (169)
⬆️ #Smokeloader 167 (145)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=271025&utm_content=linktoregister#register
#xworm SHA256: d6c5d57542327af8306e8b61fdbd0130b72343e1e1eb8c50a9b86197c875a10e C2: 143[.]14[.]44[.]111:6569
#xworm SHA256: c784521be1c5a1646d8f558d7fa5378a88e464c7a813cea548ed612a41eacd79 C2: https://pastebin[.]com/raw/aw493uTM,released-bizrate[.]gl[.]at[.]ply[.]gg:55535
#xworm SHA256: c784521be1c5a1646d8f558d7fa5378a88e464c7a813cea548ed612a41eacd79 C2: https://pastebin[.]com/raw/aw493uTM,released-bizrate[.]gl[.]at[.]ply[.]gg:55535
RE: https://infosec.exchange/@threatinsight/115408637235710538
Auch wir beobachten diese #XWorm-Welle und sehen Verbindungen zum C2-Server in den Netflows.
Wir informieren betroffene Einrichtungen. 🤗
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 927 (558)
⬇️ #Lumma 434 (503)
⬇️ #Remcos 365 (391)
⬇️ #Quasar 353 (370)
⬇️ #Vidar 293 (394)
⬇️ #Rhadamanthys 249 (297)
⬇️ #Dcrat 248 (315)
⬇️ #Njrat 238 (270)
⬇️ #Stealc 175 (255)
⬇️ #Guloader 169 (220)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=201025&utm_content=linktoregister#register
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 558 (259)
⬇️ #Lumma 503 (535)
⬇️ #Vidar 394 (422)
⬇️ #Remcos 392 (415)
⬇️ #Quasar 370 (386)
⬆️ #Dcrat 317 (309)
⬇️ #Rhadamanthys 297 (312)
⬆️ #Snake 283 (230)
⬆️ #Njrat 270 (269)
⬇️ #Agenttesla 255 (507)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=131025&utm_content=linktoregister#register
📢 Nouvelles versions de XWorm diffusées par phishing avec module ransomware
📝 Selon des chercheurs de Trellix, de nouvelles versions du backdoor XWorm sont distribuées via des campagnes de phis...
📖 cyberveille : https://cyberveille.ch/posts/2025-10-08-nouvelles-versions-de-xworm-diffusees-par-phishing-avec-module-ransomware/
🌐 source : https://www.bleepingcomputer.com/news/security/xworm-malware-resurfaces-with-ransomware-module-over-35-plugins/
#XWorm #backdoor #Cyberveille