Can't stop, won't stop: TA584 innovates initial access
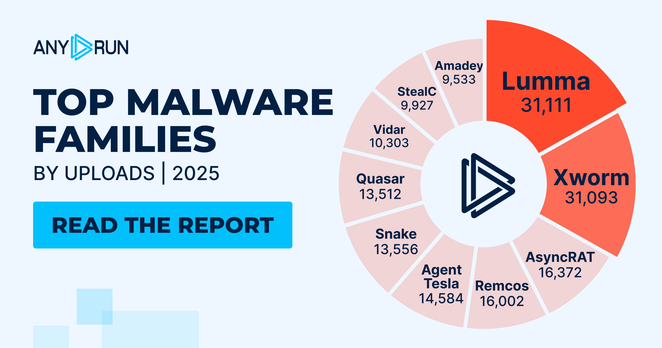
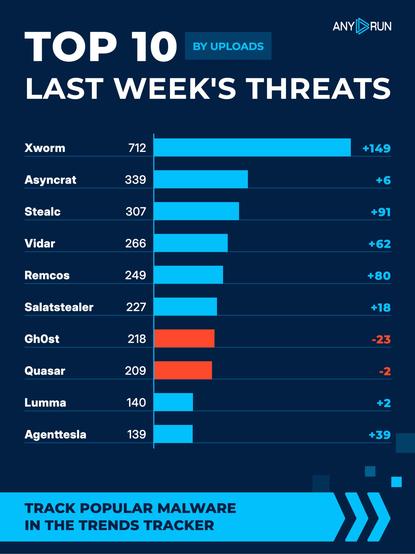
TA584, a prominent initial access broker targeting organizations globally, demonstrated significant changes in attack strategies throughout 2025. The actor expanded its global targeting, adopted ClickFix social engineering techniques, and began delivering new malware called Tsundere Bot. TA584's operational tempo increased, with monthly campaigns tripling from March to December. The actor uses various delivery methods via email, often sending from compromised individual accounts. TA584's campaigns now feature rapid succession and overlapping, with distinct lure themes and short operational lifespans. The actor has shown adaptability in social engineering, brand impersonation, and payload delivery, making static detection less effective. Recent payloads include XWorm with the 'P0WER' configuration and the newly observed Tsundere Bot, both likely part of Malware-as-a-Service offerings.
Pulse ID: 697a54c77c23553aa2d3be96
Pulse Link: https://otx.alienvault.com/pulse/697a54c77c23553aa2d3be96
Pulse Author: AlienVault
Created: 2026-01-28 18:26:15
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#CyberSecurity #Email #InfoSec #Malware #MalwareAsAService #OTX #OpenThreatExchange #RAT #SocialEngineering #Worm #XWorm #bot #AlienVault