Decai decompiling a malicious shellcode.
The instructions are not so readable, if you're not used to syscalls int 0x80. AI does it for you.
#decai
A blog post on r2ai / decai by @pancake which shows decompiling to Swift :
https://www.nowsecure.com/blog/2025/01/29/decompiling-apps-with-ai-language-models/
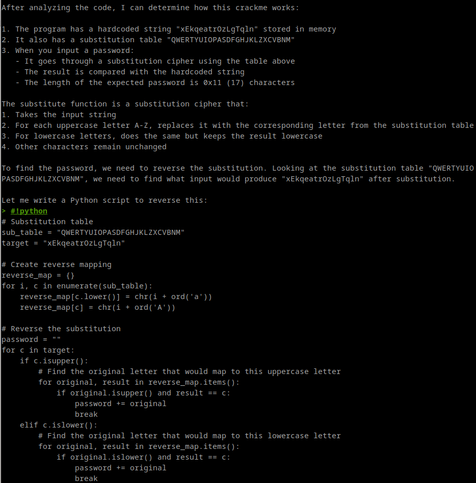
r2ai solves my CrackMe in a few seconds. It's both elegant and educational.
Read this: https://cryptax.medium.com/cracking-my-own-crackme-with-r2ai-5629bcc7d5fe
And view @dnakov video at r2con: https://www.youtube.com/watch?v=UxE5GNUBCXo
cc: @radareorg
I've been running decai with Claude AI on a malware named Goldoon.
Ghidra is usually quite good to decompile, but just compare the decompiled output with r2 (@radareorg) decai/Claude and ghidra!
This is marvelous. So much clear and concise + Claude immediately thought this was malicious (I didn't hint anything).
NB. I will talk about this at @1ns0mn1h4ck
@radareorg the program was implemented using Swift, which does not disassemble very nicely. So, I tried decai. Output in C wasn't nice, but output in Java is quite usable. At least, the password is very visible.
When you find a method with a curious name and what to know what it’s doing with #decai.
(But don’t use it for cheating, you know 😜)
#r2con2024
Once again #r2ai, #decai and #r2frida to the rescue!
They were really helpful in @as0ler’s, combining them in the process.
#r2con2024
Tomorrow we’ll be able to see how #decai was really helpful to decompile the STM8 firmware. So don’t miss it!
#r2con2024
Some more examples of #decai decompilation.
And with -Q command you can also ask if the code is vulnerable and where, and it will answer that! Isn’t it awesome?
#r2con2024
Decompiling with #decai provides a really nice output, as you can see in the example below. But even with more complex binaries the results are surprising.
#r2con2024
When dealing with python is a mess, you can write your own plugin in js, so that was how #decai was born. #ia
#r2con2024
And now… surprise talk from @pancake! He will show us some of the #decai magic.
#r2con2024
I got decai (radare2's AI-assisted decompiler) to work with a local model, and tried it over a basic Caesar implementation in C and in Dart.
To be honest, I think the conclusion is that the model I selected is not good enough ;) but #r2ai and #decai are really great tools. Read my post to understand how to install, configure and use. Or RTFM :P
https://cryptax.medium.com/using-ai-assisted-decompilation-of-radare2-e81a882863c9
many thanks to @Pancake for his patience! "it's not working on my laptop", "try this then" etc