Radio Frequency Identification cards used for building access and payment systems create a false sense of security through proximity based authentication that's trivially defeated with cheap hardware. Tools like the Proxmark3 and Flipper Zero can read, clone, and emulate most low frequency RFID cards within seconds, allowing attackers to duplicate access credentials by simply walking past targets in crowded areas. Many organizations still deploy basic 125kHz cards that transmit static identifiers with no encryption, making them as secure as writing your password on a sticky note. Even supposedly secure HID Prox cards and hotel key cards fall victim to replay attacks and cryptographic weaknesses that researchers have documented for over a decade. The persistence of vulnerable RFID systems in high security environments demonstrates how legacy technology and misplaced trust in "proprietary" solutions continue to create massive security gaps.
#RFID #Proxmark3 #FlipperZero #physicalsecurity #hacking
#flipperZero
I'm working on a piece about #Hacker #MultiTools; what devices am I missing? 🤘🕵️🤘
#FlipperZero #DevKitty #LILYGO #CC1101 #CapibaraZero #hack #EDC
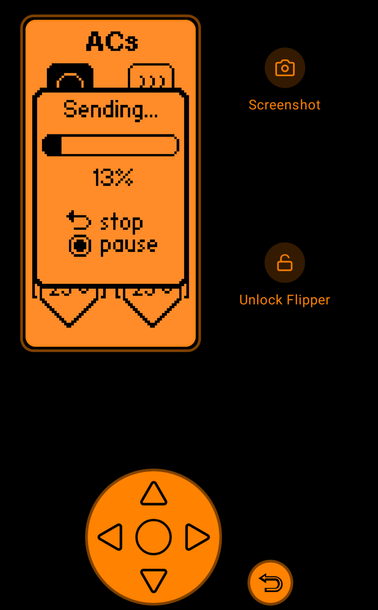
Today's "silly use case for stuff": I have a Flipper I use a criminally small amount. It's basically an overly aggressive remote control for stuff around my apartment at this point.
I forgot to turn off my AC in my living room (one of the big not-quite-window-units.) The flipper has the ability to control it, and it's in the living room
Remote control flipper, hit the power control via it to turn off the AC.
Modern problems, modern solutions.
Anyone looking for a #FlipperZero ?
Im trying to sell a transparent limited edition but eBay won’t allow it 🤦♂️
Hardly used. Happy to post or organise a pickup in #edinburgh area.
Anyone want to buy my #FlipperZero ? I haven't used it in a while and it's just too cool to gather dust. I can bring it to #GPN23 if you want to have a look.
Did you know you can get ADMIN articles and news delivered to your inbox every week? Check out this week's ADMIN Update newsletter and subscribe free to get it every Wednesday.
https://mailchi.mp/admin-magazine.com/admin-update-a-gui-for-warewulf-4
#HPC #Warewulf4 #RockyLinux #Docker #NordVPN #Linux #Proxmox #FlipperZero #Podman #events #jobs
showing people a #FlipperZero is an excellent nerd test, because they might not know it or have An Opinion on it.
If the opinion is 'omg dangerous hacking device' then you know they're at least interested but perhaps not very versed on it.
If they have one too then you can try out the sub-ghz chat thingy!
..And if they immediately start showing you other SDRs and how to set up your own stingray then you know the nerd level is exquisite and they're at very least interested in HAM/radio stuff.
There it is, my first Flipper Zero App on the official App Store:
https://lab.flipper.net/apps/qrcode_generator
NeoScout — Инструмент для пентеста и развлечений
NeoScout — это открытый мультифункциональный инструмент на базе ESP32-S3, сочетающий возможности сетевого сканера, BadUSB, Bluetooth-анализатора и образовательной платформы.
https://habr.com/ru/articles/910470/
#neoscout #flipperzero #m5stick #гик #девайс #хакер #хакерство #хакерские_инструменты
Radio Data System, SI4735 и Flipper Zero
Названия музыкальных произведений, которые проигрываются на радиостанциях, можно получать прямо из радиоэфира с помощью radio data system (англ. Radio Data System , RDS). Представим ситуацию, когда из радиоприёмника играет музыка, которая очень понравилась, и стало интересно кто её автор. Конечно, можно "зашазамить", но ведь это не наш метод. Интереснее будет взять микросхему si4735 и подключить её к Arduino. Почему бы и нет. Есть хорошая библиотека SI4735 . При таком подходе самым сложным будет качественно оформить устройство в корпусе с кнопками для изменения частоты и громкости, а ещё дисплеем и батареей, чтобы устройство было автономным. Далее будет описан способ с использованием Flipper Zero и созданием простого шилда для него. Тогда не надо терять время на кнопки и дисплей, но нужно немного потрудиться и перенести программную часть на Flipper Zero. Работа с микросхемами SI473x очень хорошо описана в статье журнала Хакер. Всё, что там написано, проверено и работает. Но там нет работы с RDS. Так что эту статью можно считать просто продолжением той статьи в части работы с RDS.
@novalug I'm looking forward to this weeks meeting and I'm bringing some fun 'hacking' toys.
#flipperZero
Custom 3D-printed Flipper Zero extension enclosure
Custom 3D-printed Flipper Zero extension enclosure
https://toobnix.org/videos/watch/346bc095-c195-4ed6-9767-ea71fda0c524
#Interrupt: Starker #FlipperZero-Konkurrent kommt mit #Linux :tux: und Tastatur - Golem.de https://www.golem.de/news/interrupt-starker-flipper-zero-konkurrent-kommt-mit-linux-und-tastatur-2505-196028.html #PenTest #PenTesting #PenetrationTesting
Alguien a experimentado/construido un #CapibaraZero o similar?
Musiałem na początek dolutować sobie piny, dla łatwiejszego podłączenia płytki.
Potem za pomocą elektronicznego multitoola #flipperzero wgrałem najnowszy firmware tasmoty przez webflasher.
Koniec końców wygląda, że wszystko działa. Standardowe ustawienia dla 4CHPROR3 weszły od ręki i przekaźniki działają.
Teraz zostało już podpięcie pod nodered na cerbogx i można przepiąć kilka ręcznych przycisków i stare przekaźniki z modbus rtu (które jest mega niestabilne po serial porcie).
At physical security village's #rsac sandbox, we learned how easy it is to emulate or clone common 125 khz RFID keyfobs with a #FlipperZero!
I’m so friendly! Just plug me in! Nothing bad will happen, I promise. 🐬 #FlipperZero
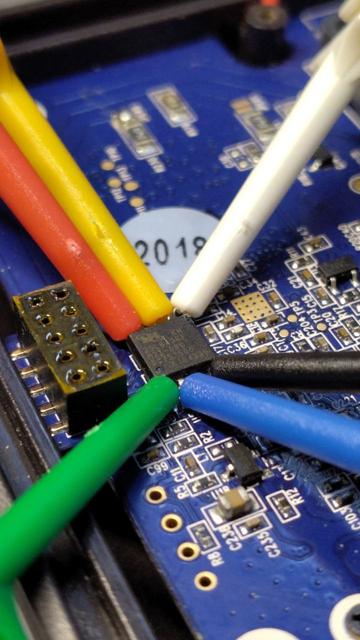
Saturday evening project
Flipper, dump all the bits! #hardwarehacking #flipperzero
Just ordered a Flipper Zero as a new toy 👀