🚨 On May 8, GreyNoise observed a coordinated scanning operation launched by 251 malicious IPs, all hosted by Amazon and geolocated in Japan. ColdFusion, Apache Struts, Tomcat targeted. Full analysis: https://www.greynoise.io/blog/coordinated-cloud-based-scanning-operation-targets-75-known-exposure-points
#greynoise
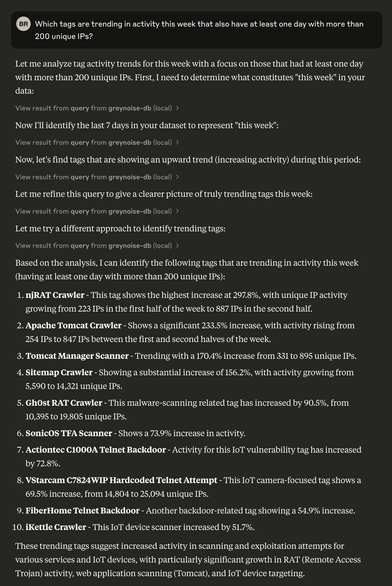
GreyNoise observed a major spike in scanning against Ivanti products weeks before two zero-days were disclosed in Ivanti EPMM. Full update: https://www.greynoise.io/blog/surge-ivanti-connect-secure-scanning-activity
#Ivanti #GreyNoise #Cybersecurity #ZeroDays
📣 Presentation drop — GreyNoise recently shared intel + insights with our friends at IT-ISAC. Watch the 3 minute highlights to get up to speed & download our full report for the details: https://www.greynoise.io/resources/how-resurgent-vulnerabilities-jeopardize-organizational-security #GreyNoise #Cybersecurity
⚠️ Spike in Git Config Crawling Highlights Risk of Codebase Exposure. We observed 4,800+ malicious IPs engaged in this activity daily from April 20-21. Full analysis & malicious IPs: https://www.greynoise.io/blog/spike-git-configuration-crawling-risk-codebase-exposure #Cybersecurity #ThreatIntel #GreyNoise
New Research Alert: Attackers are exploiting a dangerous class of cyber flaws—resurgent vulnerabilities. Learn how they work, why they matter, and what defenders can do. Full analysis ⬇️
#Cybersecurity #GreyNoise #Vulnerabilities
Our Founder, @morris is speaking at QCTR next Friday on “The Big Hairy Edge Device Problem.” Don’t miss it. 🗓️ April 25, 8–10AM ET. Register: https://bit.ly/42x325a
AI/LLM/GPT haters gonna hate, but this is fun/helpful. #DuckDB #MCP #Claude #GreyNoise
Spike in Exploitation Attempts Targeting TVT NVMS9000 DVRs — reportedly used in security and surveillance systems. Full analysis: https://www.greynoise.io/blog/surge-exploitation-attempts-tvt-dvrs #GreyNoise #Exploitation #ThreatIntel #Cybersecurity
New Threat Update from GreyNoise — Significant spike in exploitation attempts targeting Linksys E-Series routers, likely Mirai. Full analysis ⬇️
https://www.greynoise.io/blog/heightened-in-the-wild-activity-key-technologies
In-the-wild activity targeting SonicWall, Zyxel, F5, Linksys, Zoho, and Ivanti. Surge on March 28. Full analysis: https://www.greynoise.io/blog/heightened-in-the-wild-activity-key-technologies
#GreyNoise #F5 #Ivanti #SonicWall #Zoho #Linksys #CVE #Vulnerability
🚨 Following reports of widespread DrayTek router reboots, GreyNoise is bringing awareness to in-the-wild activity against multiple known vulnerabilities in DrayTek devices. Read the analysis ⬇️
https://www.greynoise.io/blog/in-the-wild-activity-against-draytek-routers
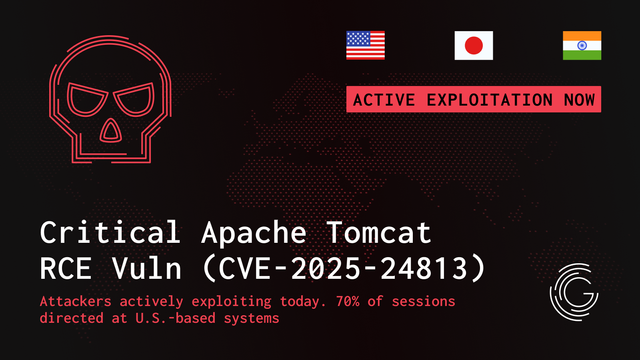
🚨Active Exploitation Alert: Critical Apache Tomcat RCE (CVE-2025-24813). Majority of traffic targeting U.S.-based systems. Exploits limited to naive attackers using PoC code. Full analysis & attacker IPs: https://greynoise.io/blog/active-exploitation-critical-apache-tomcat-rce-vulnerability-cve-2025-24813
#ApacheTomcat #Apache #GreyNoise #Vulnerability #CVE202524813
🚨 March 12 UPDATE: Grafana Exploitation May Signal Multi-Phase SSRF Attacks. Update + original analysis: https://www.greynoise.io/blog/new-ssrf-exploitation-surge #Cybersecurity #GreyNoise #Vulnerability
🚨 GreyNoise has detected active exploitation of Silk Typhoon-linked CVEs in the past 24 hours. 90 threat IPs actively targeting. Full analysis: https://www.greynoise.io/blog/active-exploitation-silk-typhoon-linked-cves #GreyNoise #Cybersecurity #SilkTyphoon
🚨 Exploitation of Newly Added KEV CVEs. GreyNoise tagged 3 of them before KEV addition. Full analysis: https://greynoise.io/blog/greynoise-observes-exploitation-three-newly-added-kev-vulnerabilities
#GreyNoise #KEV #CISA
🚨 New DDoS Botnet Discovered: Over 30,000 Devices Reportedly Used in Attacks. Majority of observed activity traced to Iran. Block these IPs immediately.
I posted a quick/fun little blog about the dangers of invisible bytes, particularly when everybody copies/pastes exploits without understanding them:
https://www.labs.greynoise.io/grimoire/2024-11-20-null-problem/
#Google :google: und #Greynoise melden Erfolge bei KI-gestützter Schwachstellensuche | Security https://www.heise.de/news/Google-und-Greynoise-melden-Erfolge-bei-KI-gestuetzter-Schwachstellensuche-10004183.html #ArtificialIntelligence
I love it when companies put their name in the PoC, it makes it so much easier to track down what I'm seeing when it gets sprayed out on the internet. Thanks watchTowr!
(This is Palo Alto Expedition - CVE-2024-9463)
Just ran a pcap on one of my server, and I also get the LOVE letters of the #ICMP #noisestorm